Configuring the Switch
3-88
• MAC – Specifies the MAC ACL to bind to a port.
• IN – ACL for ingress packets.
• ACL Name – Name of the ACL.
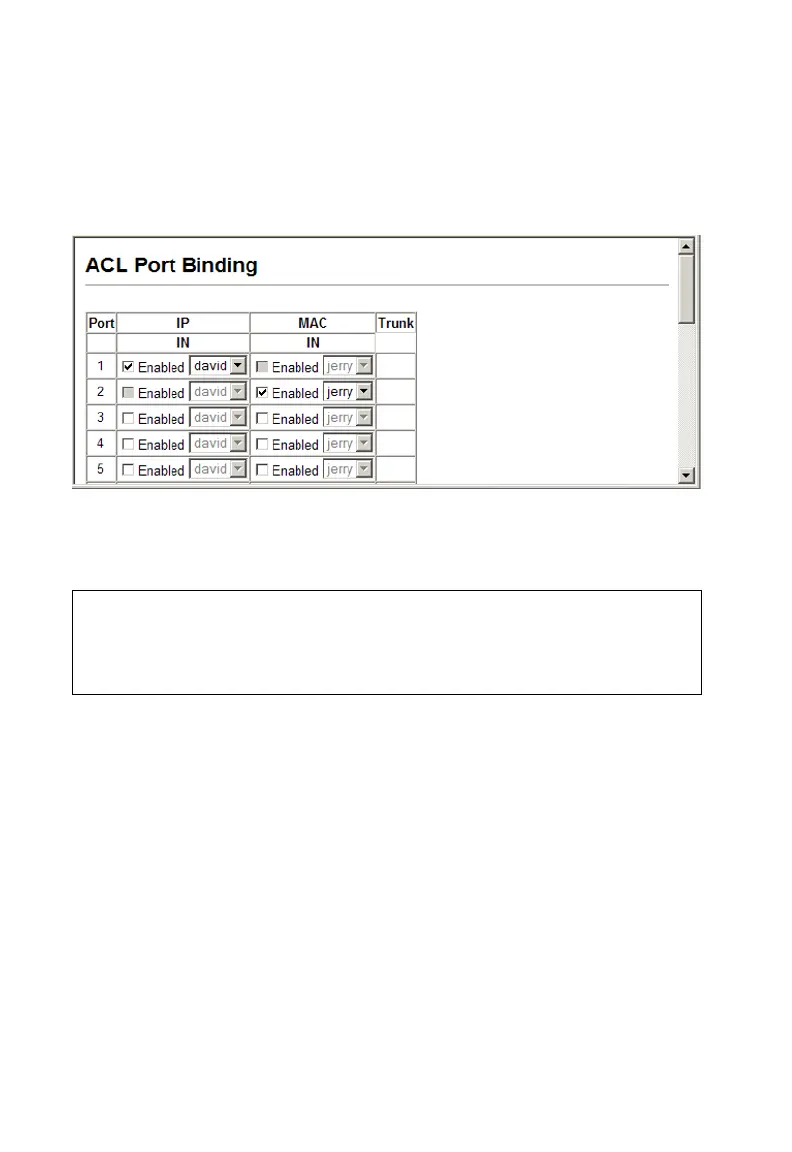
Web – Click Security, ACL, Port Binding. Mark the Enable field for the port you want
to bind to an ACL for ingress traffic, select the required ACL from the drop-down list,
then click Apply.
Figure 3-45 Mapping ACLs to Port Ingress Queues
CLI – This examples assigns an IP access list to port 1, and a MAC access list to
port 2.
DHCP Snooping
The addresses assigned to DHCP clients on unsecure ports can be carefully
controlled using the dynamic bindings registered with DHCP Snooping (or using the
static bindings configured with IP Source Guard). DHCP snooping allows a switch to
protect a network from rogue DHCP servers or other devices which send
port-related information to a DHCP server. This information can be useful in tracking
an IP address back to a physical port.
Command Usage
• Network traffic may be disrupted when malicious DHCP messages are received
from an outside source. DHCP snooping is used to filter DHCP messages received
on a non-secure interface from outside the network or firewall. When DHCP
snooping is enabled globally and enabled on a VLAN interface, DHCP messages
received on an untrusted interface from a device not listed in the DHCP snooping
table will be dropped.
Console(config)#interface ethernet 1/1 4-135
Console(config-if)#ip access-group david in 4-127
Console(config-if)#exit
Console(config)#interface ethernet 1/2
Console(config-if)#mac access-group jerry in
Console(config-if)#

 Loading...
Loading...











