5 - 334 WiNG 5.6 Access Point System Reference Guide
5.4.5.5.5 Overriding General Security Settings
Overriding a Security Configuration
A profile can leverage existing firewall, wireless client role and WIPS policies and configurations and apply them to the
configuration. This affords a profile a truly unique combination of data protection policies. However, as deployment
requirements arise, an individual access point may need some or all of its general security configuration overridden from that
applied in the profile.
To define a profile’s security settings and overrides:
1. Select Devices from the Configuration tab.
2. Select Device Overrides from the Device menu to expand it into sub menu options.
3. Select a target device from the device browser in the lower, left-hand, side of the UI.
4. Select Security to expand its sub menu options.
5. Select Settings.
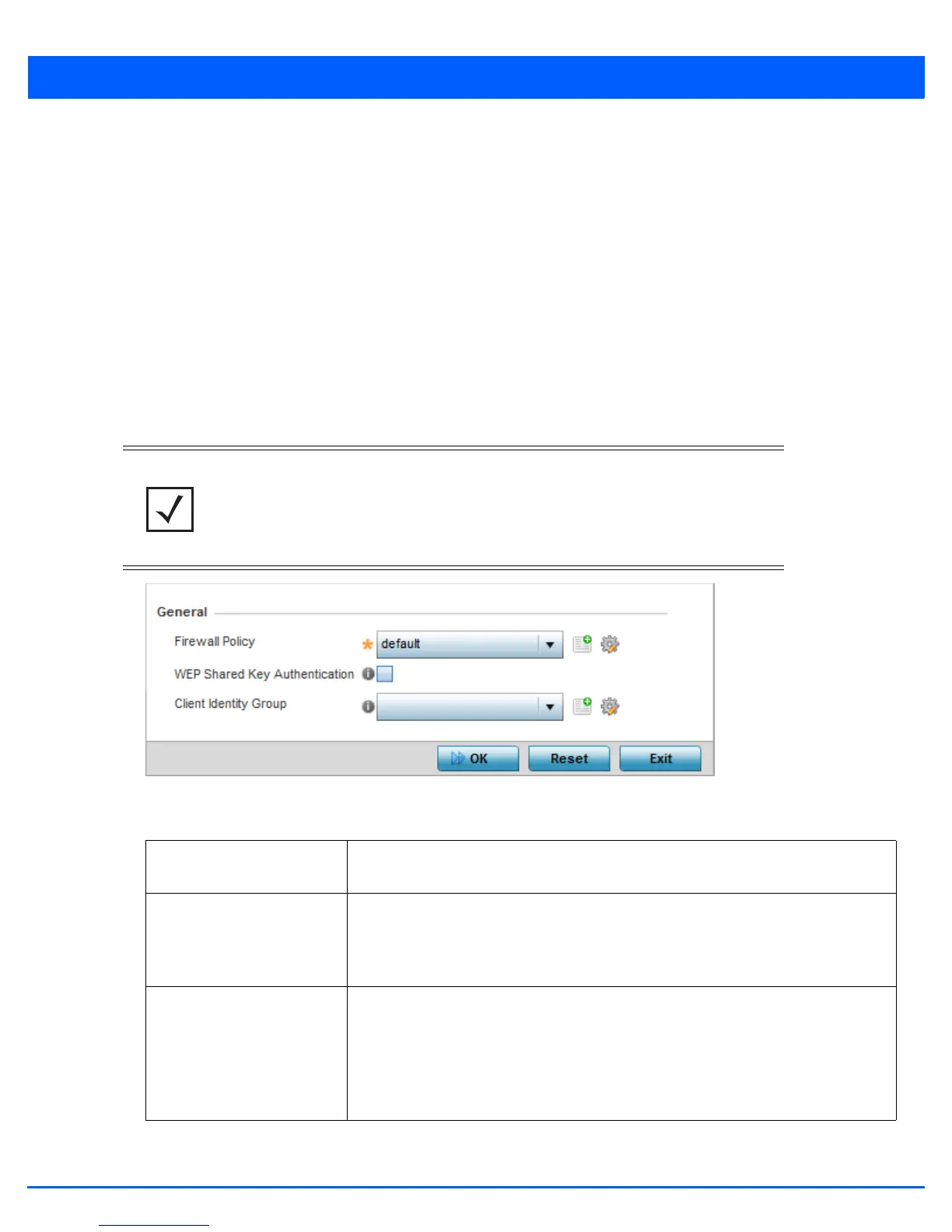
Figure 5-221 Device Overrides - Security Settings screen
6. Refer to the General field to assign or override the following:
7. Select OK to save the changes or overrides. Select Reset to revert to the last saved configuration.
NOTE: A blue override icon (to the left of a parameter) defines the parameter as having
an override applied. To remove an override, go to the Basic Configuration screen’s
Device Overrides field and select Clear Overrides. This will remove all overrides
from the device.
Firewall Policy Select the firewall policy used by devices with this profile. Use the icons next to this
field to create or add new firewall policies.
WEP Shared Key
Authentication
Select this option to require devices using this profile to use a WEP key to access the
network using this profile. Clients without Motorola Solutions adapters need to use
WEP keys manually configured as hexadecimal numbers. This option is disabled by
default.
Client Identity Group Client Identity is a set of unique fingerprints used to identify a class of devices. This
information is used to configure permissions and access rules for devices classes in the
network. It is a collection of client identities that identify devices and applies specific
permissions and restrictions on these devices. From the drop-down menu select the
client identity group to use with this security setting. For more information, see Device
Fingerprinting on page 8-23.

 Loading...
Loading...











