xStack® DES-3528/DES-3552 Series Layer 2 Stackable Fast Ethernet Managed Switch Web UI Reference Guide
chunk0 chunk1 chunk2 …… chunk29 chunk30 chunk31
B126,
B127,
B0,
B1
B2,
B3,
B4,
B5
B6,
B7,
B8,
B9
…… B114,
B115,
B116,
B117
B118,
B119,
B120,
B121
B122,
B123,
B124,
B125
Example:
offset_chunk_1 0 0xffffffff will match packet byte offset 126,127,0,1
offset_chunk_1 0 0x0000ffff will match packet byte offset,0,1
NOTE: Only one packet_content_mask profile can be created.
With this advanced unique Packet Content Mask (also known as Packet Content Access Control List -
ACL), the
D-Link xStack
®
switch family can effectively mitigate some network attacks like the
common ARP Spoofing attack that is wide spread today. This is why the Packet Content ACL
is able to inspect any specified content of a packet in different protocol layers.
Click the Select button to select an ACL type.
Click the Create button to create a profile.
Click the <<Back button to discard the changes made and return to the previous page.
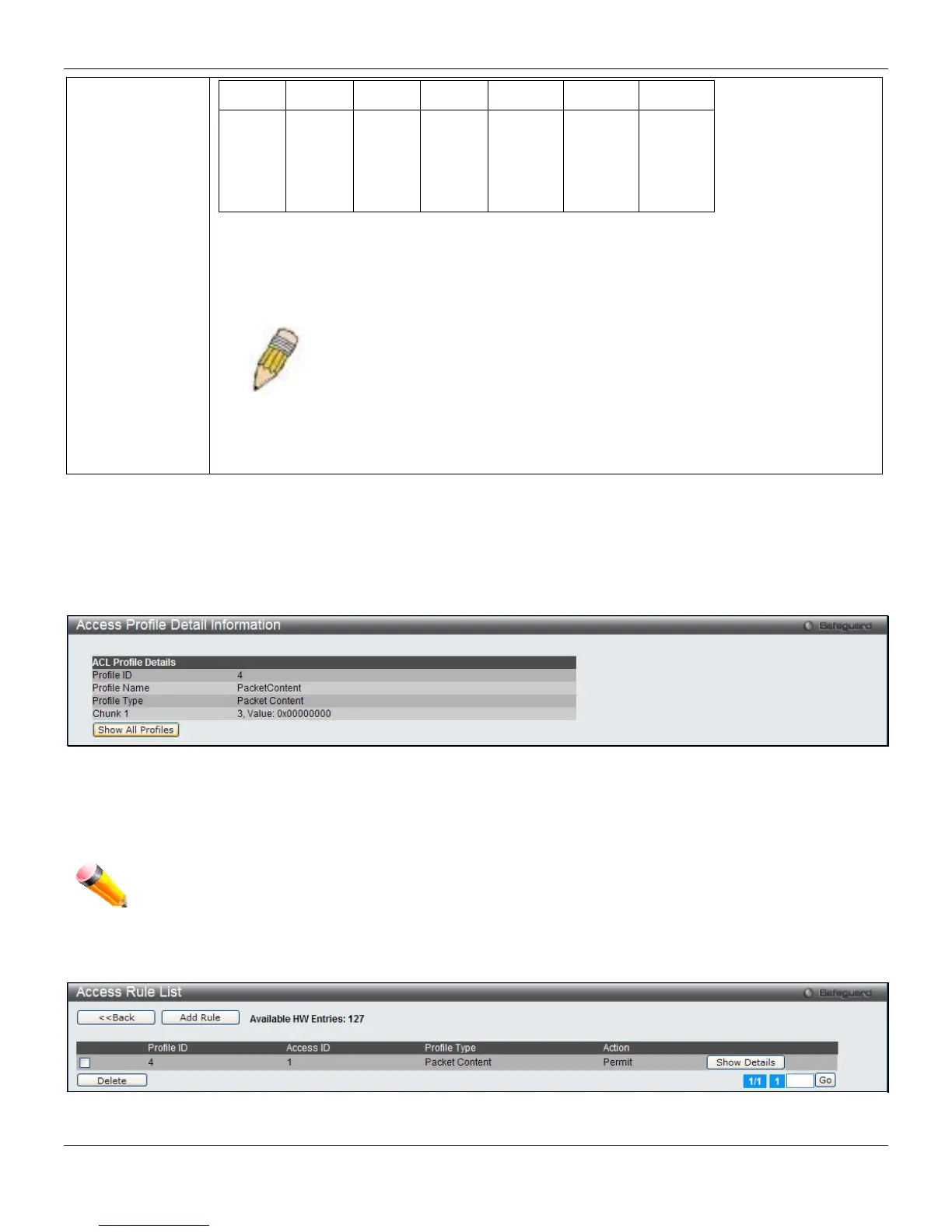
After clicking the Show Details button, the following page will appear:
Figure 7-19 Access Profile Detail Information (Packet Content ACL)
Click the Show All Profiles button to navigate back to the Access Profile List Page.
NOTE: Address Resolution Protocol (ARP) is the standard for finding a host’s hardware address (MAC
address). However, ARP is vulnerable as it can be easily spoofed and utilized to attack a LAN (i.e.
an ARP spoofing attack). For a more detailed explanation on how ARP protocol works and how to
employ D-Link’s unique Packet Content ACL to prevent ARP spoofing attack, please see Appendix
E at the end of this manual.
After clicking the Add/View Rules button, the following page will appear:
Figure 7-20 Access Rule List (Packet Content ACL)
181
 Loading...
Loading...











