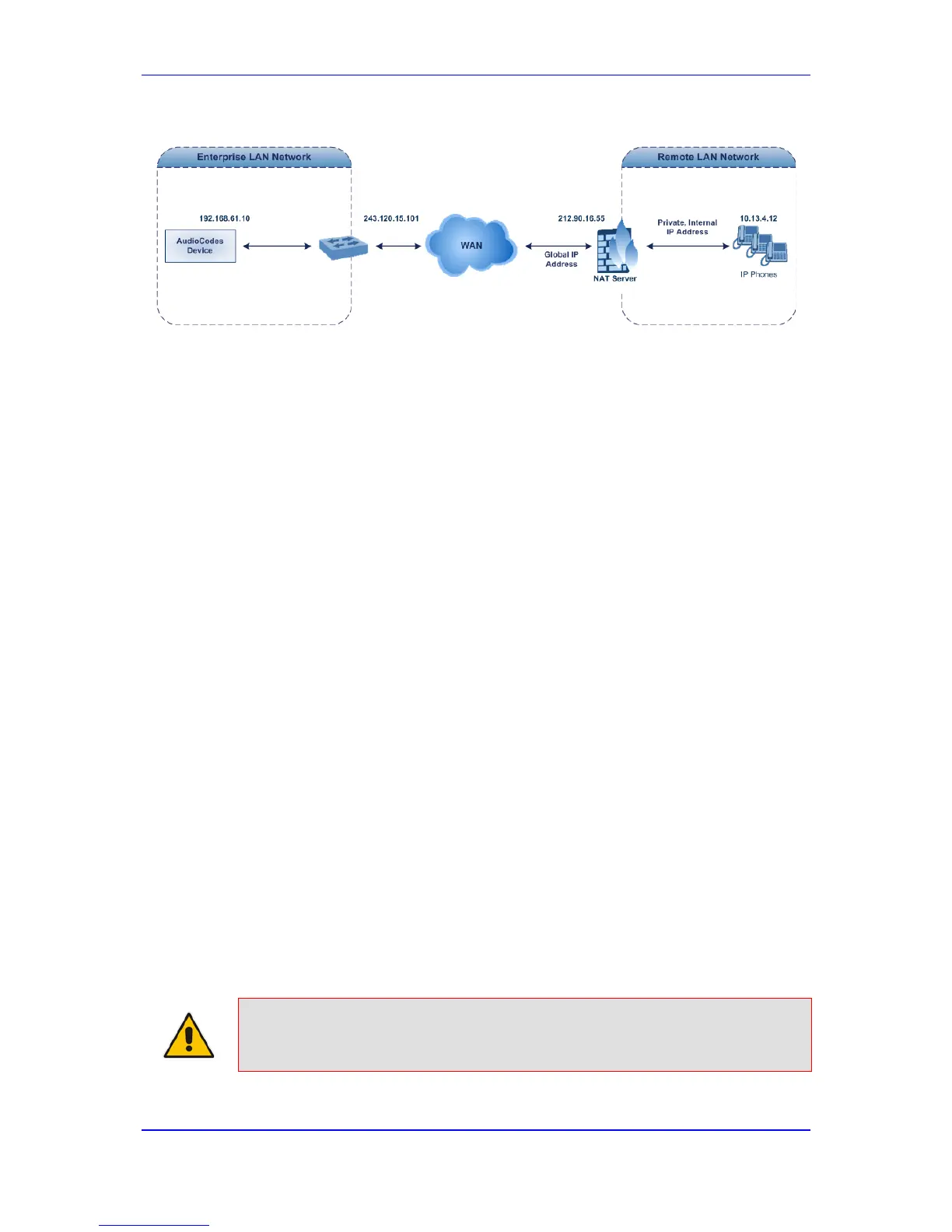
Figure 14-11: Remote UA behind NAT
14.6.2.1 First Incoming Packet Mechanism
If the remote device resides behind a NAT device, it’s possible that the device can activate
the RTP/RTCP/T.38 streams to an invalid IP address / UDP port. To avoid such cases, the
device automatically compares the source address of the first received incoming
RTP/RTCP/T.38 stream with the IP address and UDP port of the remote device when the
session was initially opened. If the two are not identical, then the destination IP address of
the outgoing RTP packets is set to the source IP address of the first incoming packet. The
RTP, RTCP and T.38 can thus have independent destination IP addresses and UDP ports.
To enable NAT resolution using the First Incoming Packet mechanism:
1. Open the General Media Settings page (Configuration tab > VoIP menu > Media >
General Media Settings).
2. Set the 'NAT Traversal' parameter to Enable.
3. Click Submit.
14.6.2.2 No-Op Packets
The device's No-Op packet support can be used to verify Real-Time Transport Protocol
(RTP) and T.38 connectivity, and to keep NAT bindings and Firewall pinholes open. The
No-Op packets are available for sending in RTP and T.38 formats.
You can control the activation of No-Op packets by using the ini file parameter
NoOpEnable. If No-Op packet transmission is activated, you can control the time interval in
which No-Op packets are sent in the case of silence (i.e., no RTP or T.38 traffic). This is
done using the ini file parameter NoOpInterval. For a description of the RTP No-Op ini file
parameters, see 'Networking Parameters' on page 755.
RTP No-Op: The RTP No-Op support complies with IETF Internet-Draft draft-wing-
avt-rtp-noop-03 ("A No-Op Payload Format for RTP"). This IETF document defines a
No-Op payload format for RTP. The draft defines the RTP payload type as dynamic.
You can control the payload type with which the No-Op packets are sent. This is
performed using the RTPNoOpPayloadType ini parameter (see 'Networking
Parameters' on page
755). The default payload type is 120.

 Loading...
Loading...