427
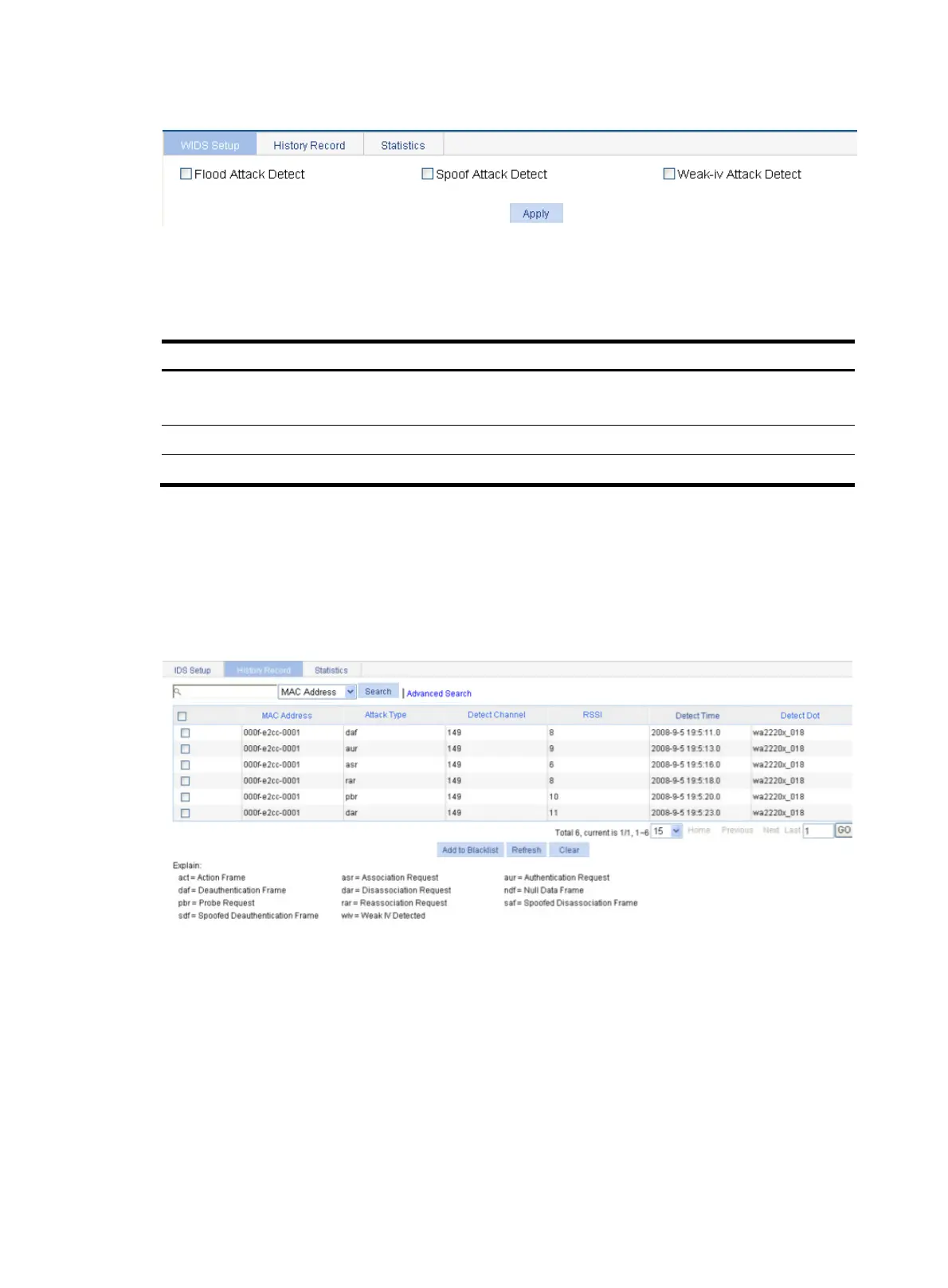
Figure 460 Configuring WIDS
2. Configure WIDS as described in Table 143.
3. Click Apply.
Table 143 Configuration items
Item Descri
tion
Flood Attack Detect
If you select the box, flood attack detection is enabled.
It is disabled by default.
Spoof Attack Detect If you select the box, spoofing attack detection is enabled. It is disabled by default.
Weak-iv Attack Detect If you select the box, Weak IV attack detection is enabled. It is disabled by default.
Displaying history record
1. Select Security > WIDS from the navigation tree.
2. Click the History Record tab.
Figure 461 Displaying history information
Displaying statistics information
1. Select Security > WIDS from the navigation tree.
2. Click the Statistics tab.

 Loading...
Loading...