User's Manual
277
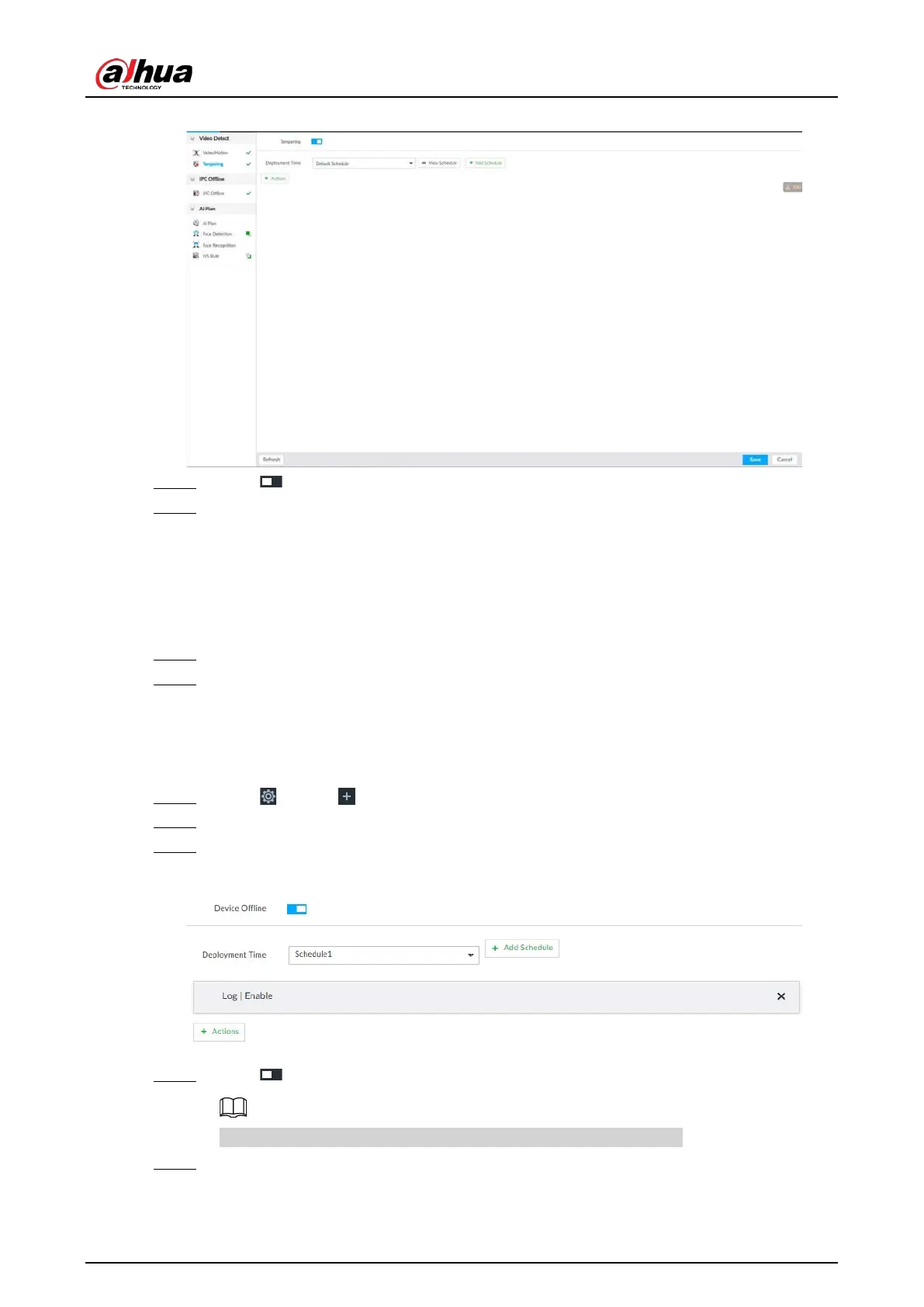
Figure 8-62 Tampering
Step 4 Click to enable tampering alarm.
Step 5 Click Deployment Time to select schedule from the drop-down list.
After setting deployment period, system triggers corresponding operations when there is
a motion detection alarm in the specified period.
●
Click
View Schedule to view detailed schedule settings.
●
If the schedule is not added or the added schedule does not meet actual needs, click
Add Schedule. See "8.8.4 Schedule" for detailed information.
Step 6 Click
Actions to set alarm actions. See "8.4.1 Alarm Actions" for detailed information.
Step 7 Click Save.
8.4.3.2 Offline Alarm
When the remote device and the IVSS are disconnected, system can trigger an alarm.
Step 1 Click , or click on the configuration page, and then select
EVENT.
Step 2 Select a remote device in the device tree on the left.
Step 3 Select Device Offline > Device Offline.
Figure 8-63 IPC offline
Step 4 Click to enable offline alarm.
The device offline alarm is enabled by default. You can skip this step.
Step 5 Click
Deployment Time to select schedule from the drop-down list.
After setting deployment period, system triggers corresponding operations when there is
 Loading...
Loading...











