355
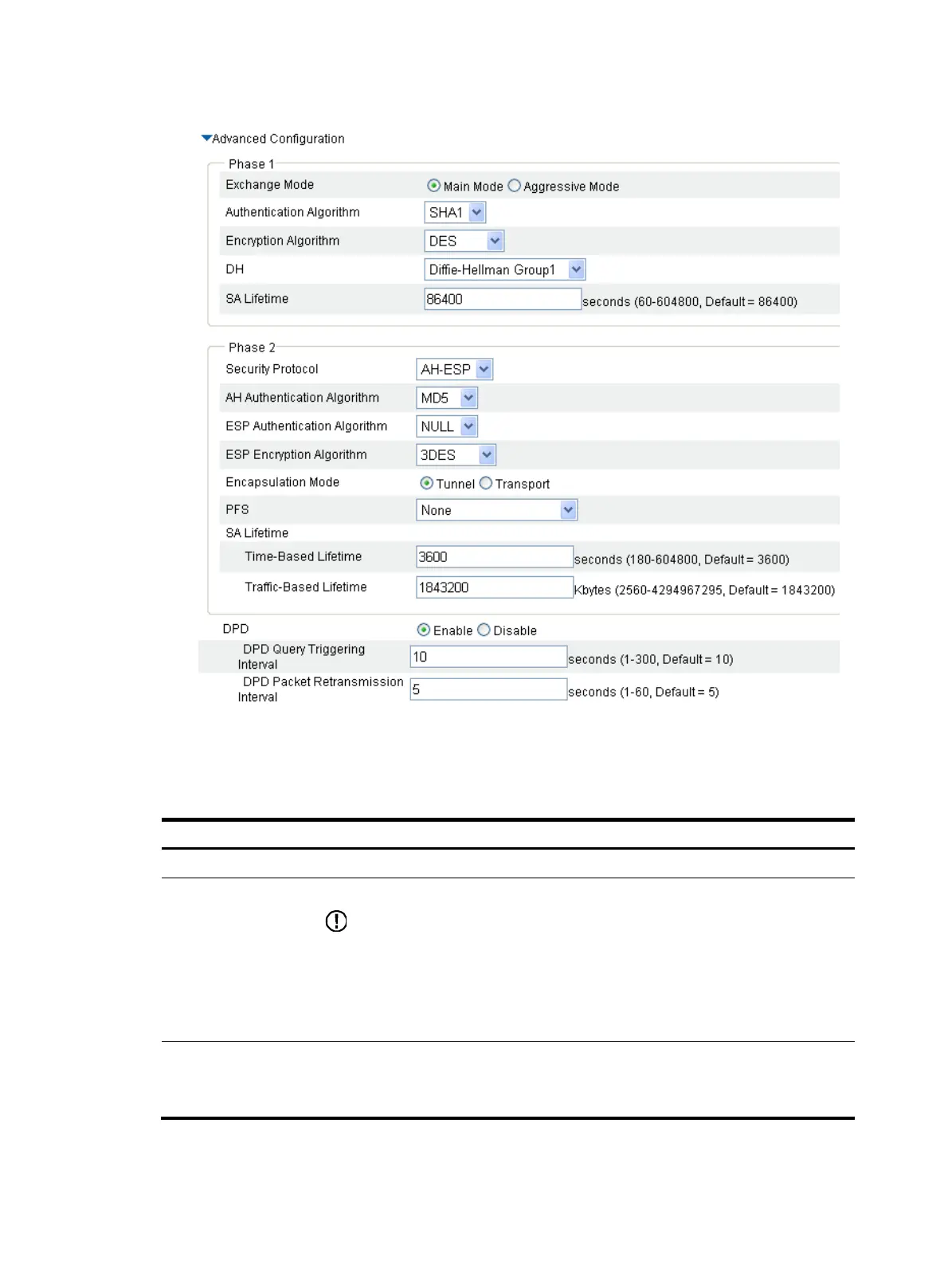
Figure 357 Advanced configuration
5. Perform advanced connection configuration as described in Table 156.
6. Click Apply.
Table 156 Configuration items
Item Descri
tion
Phase 1
Exchange Mode
Select the IKE negotiation mode in phase 1, which can be main or aggressive.
IMPORTANT:
• If the IP address of one end of an IPsec tunnel is obtained dynamically, the IKE
negotiation mode must be aggressive. In this case, SAs can be established as long
as the username and password are correct.
• An IKE peer uses its configured IKE negotiation mode when it is the negotiation
initiator. A negotiation responder uses the IKE negotiation mode of the initiator.
Authentication
Algorithm
Select the authentication algorithm to be used in IKE negotiation. Options include:
• SHA1—Uses HMAC-SHA1.
• MD5—Uses HMAC-MD5.

 Loading...
Loading...