294
Diagnostic tools
Ping
The ping command allows you to verify whether a device with a specified address is reachable, and to
examine network connectivity.
The ping function is implemented through the Internet Control Message Protocol (ICMP):
1. The source device sends an ICMP echo request to the destination device.
2. The source device determines whether the destination is reachable based on whether it receives an
ICMP echo reply. If the destination is reachable, the source device determines the following:
The link quality, based on the numbers of ICMP echo requests sent and replies received.
The distance between the source and destination, based on the round trip time of ping packets.
Trace route
By using the trace route command, you can trace the Layer 3 devices involved in delivering an IP packet
from source to destination to check whether a network is available. This is useful for identification of
failed node(s) in the event of network failure.
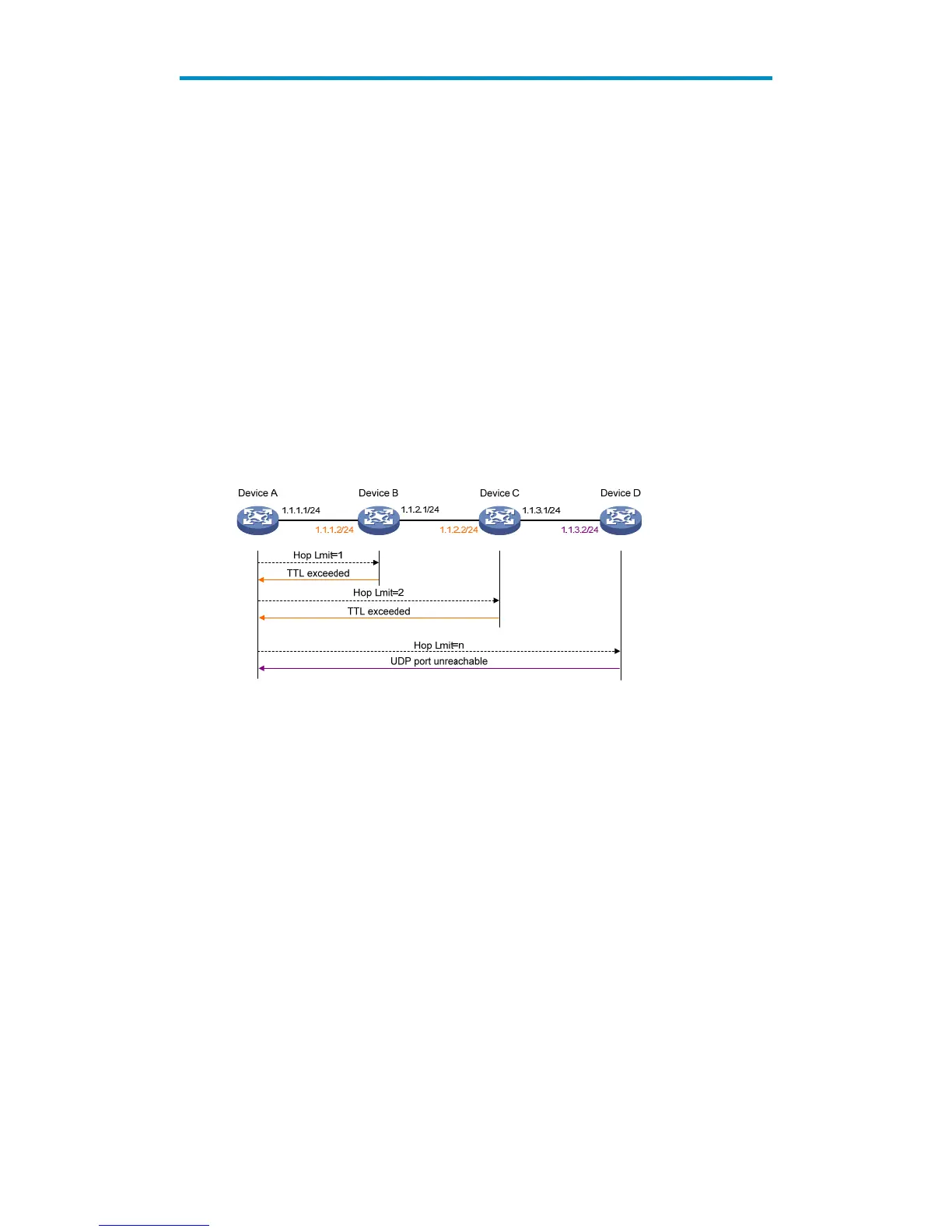
Figure 260 Trace route diagram
The trace route function is implemented through ICMP, as shown in Figure 260:
1. The source (Device A) sends a packet with a TTL value of 1 to the destination (Device D). The UDP
port of the packet is a port number that will not be used by any application of the destination.
2. The first hop (Device B) (the Layer 3 device that first receives the packet) responds by sending a
TTL-expired ICMP error message to the source, with its IP address 1.1.1.2 encapsulated. In this
way, the source device can get the address (1.1.1.2) of the first Layer 3 device.
3. The source device sends a packet with a TTL value of 2 to the destination device.
4. The second hop (Device C) responds with a TTL-expired ICMP error message, which gives the
source device the address (1.1.2.2) of the second Layer 3 device.
5. The process continues until the ultimate destination device is reached. No application of the
destination uses this UDP port. The destination replies a port unreachable ICMP error message
with the destination IP address 1.1.3.2.

 Loading...
Loading...











