Manage Security Profiles and Profile Groups
140
ProSAFE Wireless Controller
Manage Authentication Servers and Authentication
Server Groups
You can set up internal and external authentication servers and server groups that the
wireless controller can use for authentication.
Authentication Server Concepts
You can specify three types of authentication servers: internal, external RADIUS, and
external LDAP:
• Internal authentication server. The wireless controller handles authentication. If you
use this setting, set up WiFi clients on the User Management page (see Manage Users,
Accounts, and Passwords on page 236.)
• External RADIUS server. You can define a basic external RADIUS server that you would
typically use in the profiles of a basic profile group of a small-scale network. You must
specify its configuration on the basic Authentication Server page (see Configure Basic
Authentication Server Settings on page 142) so that you can select this authentication
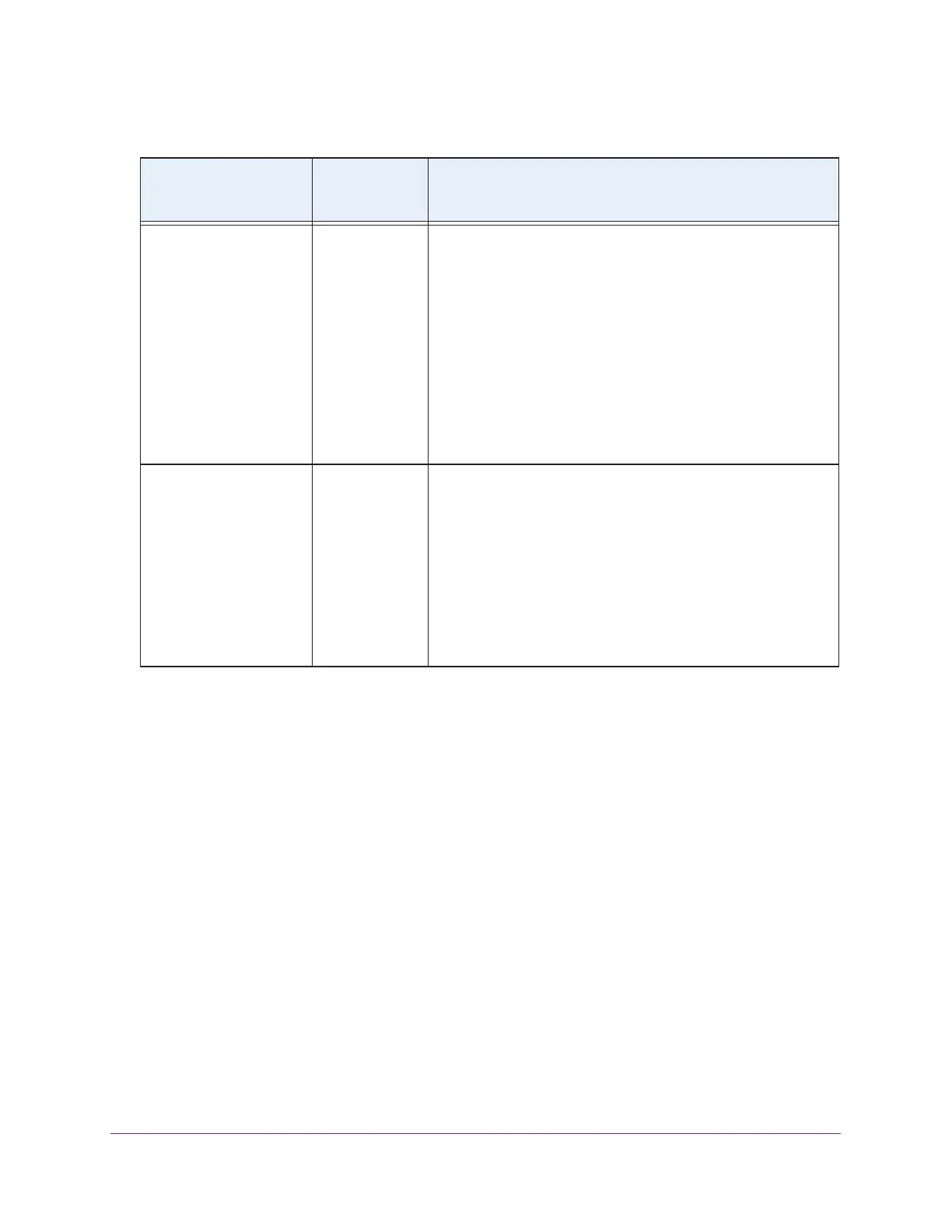
WPA2-PSK AES
TKIP + AES
To configure WPA2-PSK authentication:
1. From the Data Encryption menu, select the type of
encryption:
- AES. Supports AES only.
- TKIP + AES. Supports both TKIP and AES.
2. To display the characters in the WPA Passphrase (Network
Key) field, select the Show Passphrase check box.
3. Type a passphrase of at least eight characters in the WPA
Passphrase (Network Key) field.
Note: For information about requirements for a WPA
passphrase, see Table 15 on page 389.
WPA-PSK & WPA2-PSK
Note: Use this option if
the network includes both
WPA and WPA2 clients.
TKIP + AES To configure WPA-PSK & WPA2-PSK authentication:
1. To display the characters in the WPA Passphrase (Network
Key) field, select the Show Passphrase check box.
2. Type a passphrase of at least eight characters in the WPA
Passphrase (Network Key) field.
Note: The Data Encryption menu displays TKIP + AES, which
is the only available option. Both TKIP and AES are supported.
Note: For information about requirements for a WPA
passphrase, see Table 15 on page 389.
Table 10. Network authentication and data encryption settings (continued)
Network Authentication
Selection
Data
Encryption
Options
Configuration Steps

 Loading...
Loading...