D-Link DWC-1000 User Manual 248
Section 8 - Security
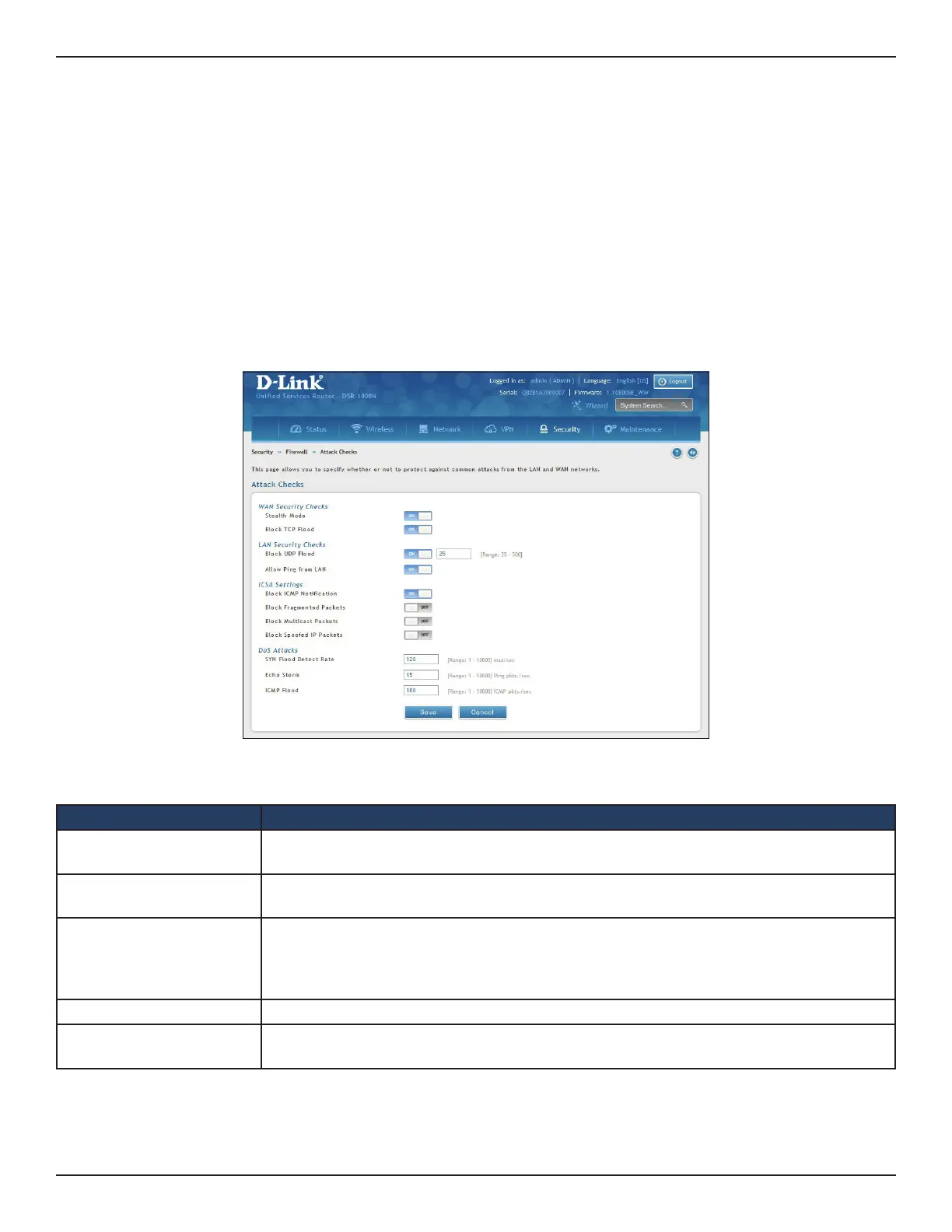
Attack Checks
Path: Security > Firewall > Attack Checks
Attacks can be malicious security breaches or unintentional network issues that render the controller unusable
Attack checks allow you to manage Option security threats such as continual ping requests and discovery via
ARP scans. TCP and UDP ood attack checks can be enabled to manage extreme usage of Option resources.
Additionally certain Denial-of-Service (DoS) attacks can be blocked. These attacks, if uninhibited, can use up
processing power and bandwidth and prevent regular network services from running normally. ICMP packet
ooding, SYN trac ooding, and Echo storm thresholds can be congured to temporarily suspect trac from
the oending source.
1. Click Security > Firewall > Attack Checks.
2. Complete the elds from the table below and click Save.
Field Description
Stealth Mode
If this option is toggled to ON, the controller will not respond to port scans from the WAN.
This makes it less susceptible to discovery and attacks.
Block TCP Flood
If this option is toggled to ON, the controller will drop all invalid TCP packets and be
protected from a SYN ood attack.
Block UDP Flood
If this option is toggled to ON, the controller will not accept more than 20 simultaneous,
active UDP connections from a single computer on the LAN. You can set the number of
simultaneous active UDP connections to be accepted from a single computer on the LAN;
the default is 25.
Allow Ping from LAN Toggle to ON to allow local computers to ping.
Block ICMP Notication
Toggle to ON to prevent ICMP packets from being identied as such. ICMP packets, if iden-
tied, can be captured and used in a Ping (ICMP) ood DoS attack.
 Loading...
Loading...



