C
HAPTER
14
| Security Measures
Access Control Lists
– 297 –
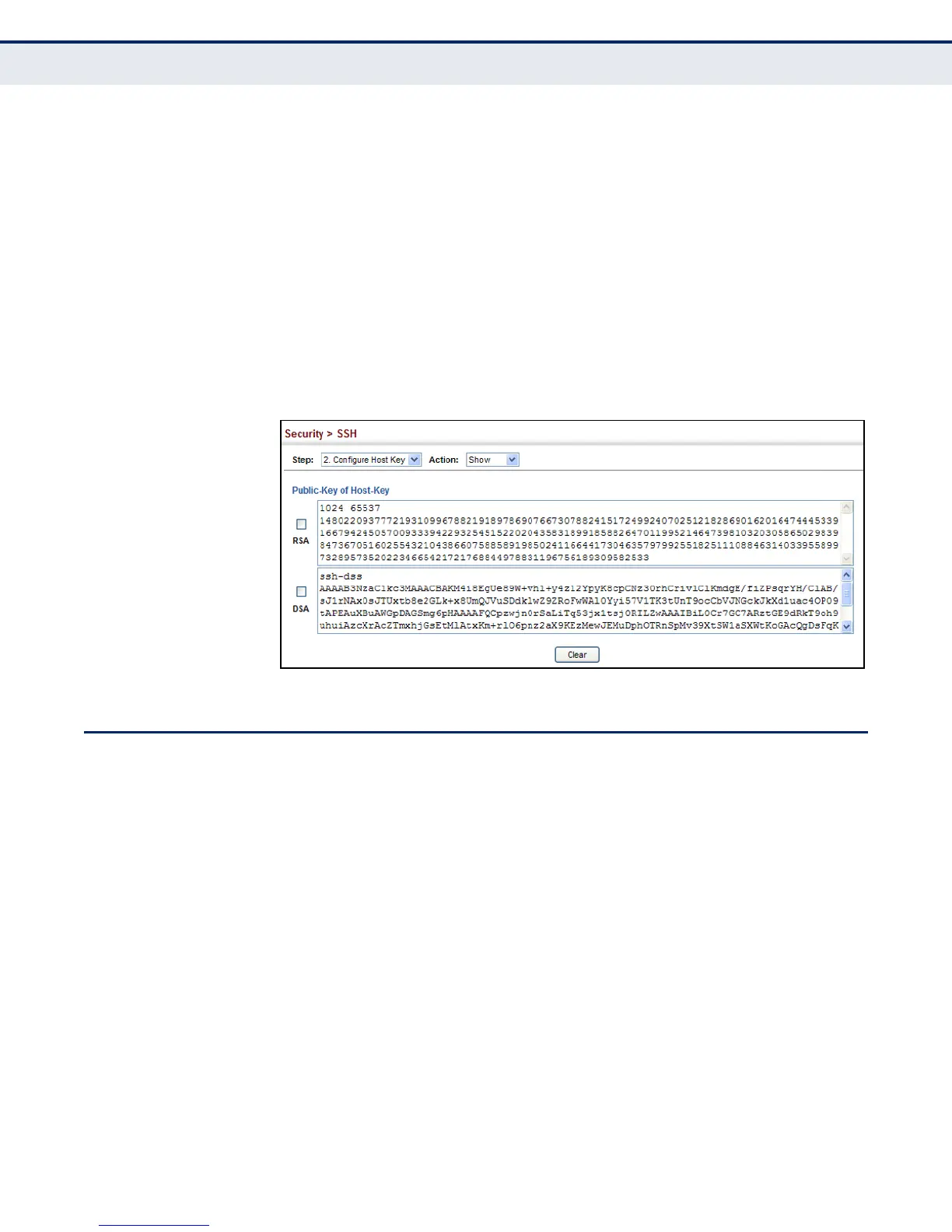
To display or clear the SSH user’s public key:
1. Click Security, SSH.
2. Select Configure User Key from the Step list.
3. Select Show from the Action list.
4. Select a user from the User Name list.
5. Select the host-key type to clear.
6. Click Clear.
Figure 166: Showing the SSH User’s Public Key
ACCESS CONTROL LISTS
Access Control Lists (ACL) provide packet filtering for IPv4 frames (based
on address, protocol, Layer 4 protocol port number or TCP control code), or
any frames (based on MAC address or Ethernet type). To filter incoming
packets, first create an access list, add the required rules, and then bind
the list to a specific port.
Configuring Access Control Lists –
An ACL is a sequential list of permit or deny conditions that apply to IP
addresses, MAC addresses, or other more specific criteria. This switch tests
ingress packets against the conditions in an ACL one by one. A packet will
be accepted as soon as it matches a permit rule, or dropped as soon as it
matches a deny rule. If no rules match, the packet is accepted.
COMMAND USAGE
The following restrictions apply to ACLs:
◆ The maximum number of ACLs is 64.
◆ The maximum number of rules per system is 512 rules.

 Loading...
Loading...











