Encryption Key Administration
The intercom can keep up to 4 valid encryption keys: 1 primary and up to 3 secondary
ones. A mobile device can use any of the 4 keys for communication encryption. The
encryption keys are fully controlled by the system administrator. It is recommended
that the encryption keys should be periodically updated for security reasons,
especially in the event of a mobile device loss or intercom configuration leak.
Poznámka
The encryption keys are generated automatically upon the intercom first
launch and saved into the intercom configuration file. We recommend
you to re-generate the encryption keys manually before the first use to
enhance security.
The primary key can be re-generated any time. Thus, the original primary key
becomes the first secondary key, the first secondary key becomes the second
secondary key and so on. Secondary keys can be deleted any time.
When a key is deleted, the users that still use this key will not be able 2N Mobile Key
®
to authenticate themselves unless they have updated the encryption keys in their
mobile devices before deletion. The mobile device keys are updated at every use of
the application.2N Mobile Key
®
List of Parameters
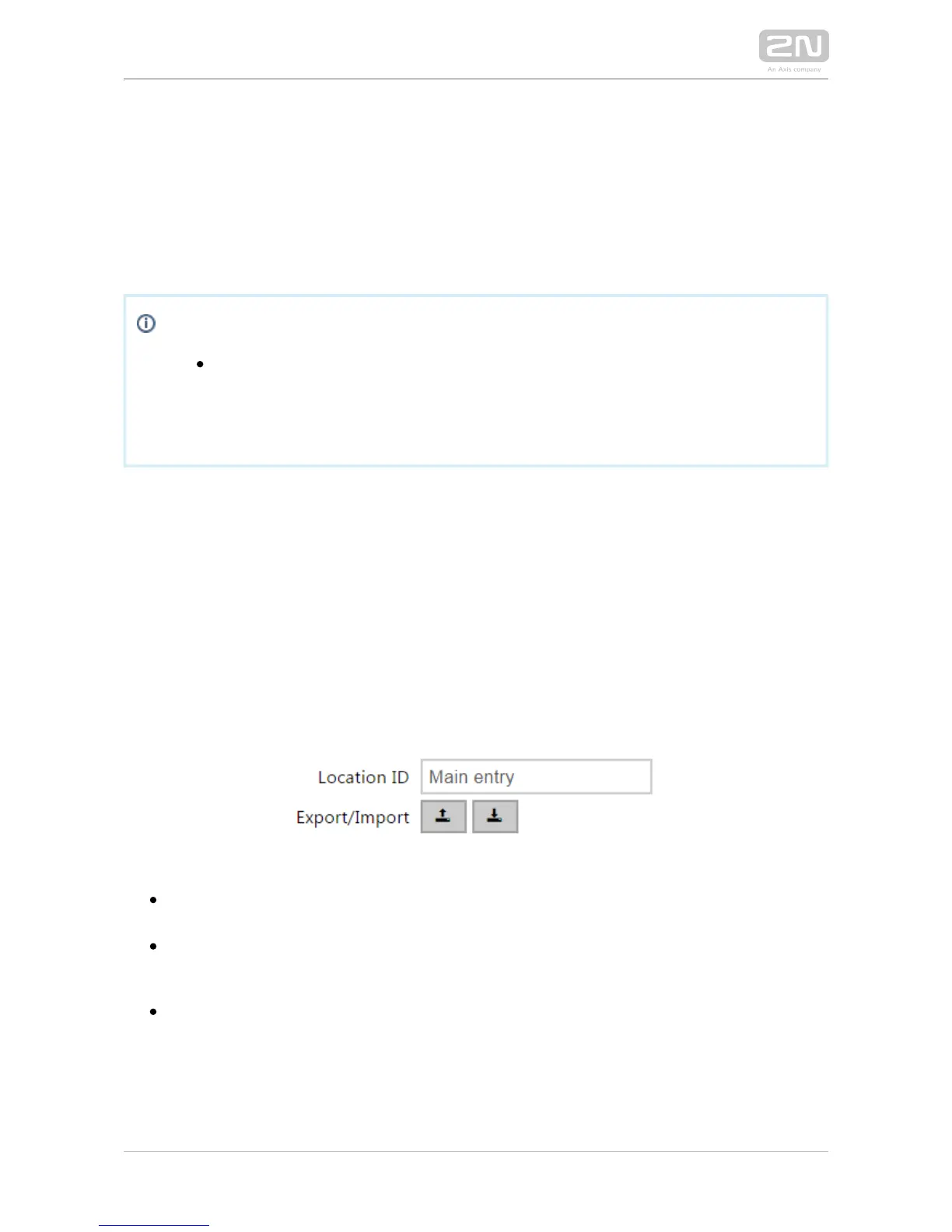
Location ID – set a unique identifier for the location in which the selected
encryption key set is valid.
Export – push the button to export the location ID and current encryption keys
into a file. Subsequently, the exported file can be imported to another device.
Devices with identical location IDs and encryption keys form a so-called location.
Import – push the button to import the location ID and current encryption keys
from a file exported from another intercom. Devices with identical location IDs
and encryption keys form a so-called location.
 Loading...
Loading...