User's Manual 67. Configuration Parameters Reference
Version 6.8 1011 Mediant 500L MSBR
Parameter Description
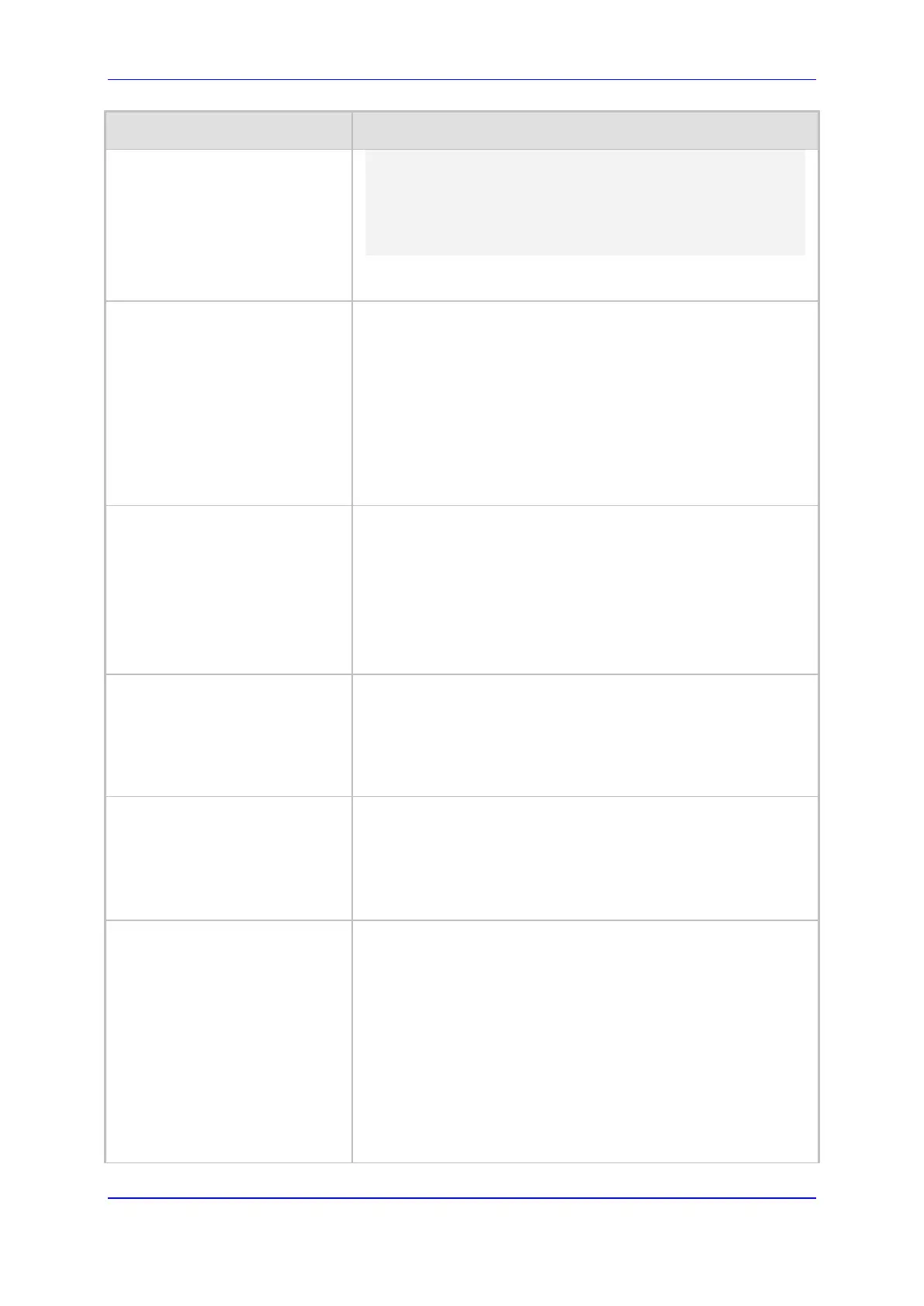
s=
c=IN IP4 host.example.com
t=0 0
m=audio 0 RTP/AVP 0
m=image 12345 udptl t38
If this parameter is disabled, the only ‘m=’ line included in the
SDP is the newly negotiated media (i.e., image).
Web: SBC Diversion URI Type
CLI: sbc-diversion-uri-type
(configure voip > sbc general-
setting)
[SBCDiversionUriType]
Defines the URI type to use in the SIP Diversion header of the
outgoing SIP message.
[0] Transparent = (Default) The device does not change the
URI and leaves it as is.
[1] Sip = The "sip" URI is used.
[2] Tel = The "tel" URI is used.
Note: The parameter is applicable only if the Diversion header is
used. The SBCDiversionMode and SBCHistoryInfoMode
parameters in the IP Profile table determine the call redirection
(diversion) SIP header to use - History-Info or Diversion.
Web: SBC Server Auth Mode
CLI: sbc-server-auth-mode
[SBCServerAuthMode]
Defines whether authentication of the SIP client is done locally
(by the device) or by a RADIUS server.
[0] (default) = Authentication is done by the device (locally).
[1] = Authentication is done by the RFC 5090 compliant
RADIUS server
[2] = Authentication is done according to the Draft Sterman-
aaa-sip-01 method.
Note: Currently, option [1] is not supported.
Web: Lifetime of the nonce in
seconds
CLI: lifetime-of-nonce
[AuthNonceDuration]
Defines the lifetime (in seconds) that the current nonce is valid for
server-based authentication. The device challenges a message
that attempts to use a server nonce beyond this period. This
parameter is used to provide replay protection (i.e., ensures that
old communication streams are not used in replay attacks).
The valid value range is 30 to 600. The default is 300.
Web: Authentication Challenge
Method
CLI: auth-chlng-mthd
[AuthChallengeMethod]
Defines the type of server-based authentication challenge.
[0] 0 = (Default) Send SIP 401 "Unauthorized" with a WWW-
Authenticate header as
the authentication challenge response.
[1] 1 = Send SIP 407 "Proxy Authentication Required" with a
Proxy-Authenticate header as the authentication challenge
response.
Web: Authentication Quality of
Protection
CLI: auth-qop
[AuthQOP]
Defines the authentication and integrity level of quality of
protection (QoP) for digest authentication offered to the client.
When the device challenges a SIP request (e.g., INVITE), it
sends a SIP 401 response with the Proxy-Authenticate header or
WWW-Authenticate header containing the 'qop' parameter. The
QoP offered in the 401 response can be 'auth', 'auth-int', both
'auth' and 'auth-int', or the 'qop' parameter can be omitted from
the 401 response. In response to the 401, the client needs to
send the device another INVITE with the MD5 hash of the INVITE
message and indicate the selected auth type.
[0] 0 = The device sends 'qop=auth' in the SIP response,
requesting authentication (i.e., validates user by checking user
name and password). This option does not authenticate the

 Loading...
Loading...



