User's Manual 16. Security
Version 6.8 177 Mediant 500L MSBR
If the severity level is raised, the alarm of the former severity is cleared and the
device sends a new alarm with the new severity. The alarm is cleared after a
user-defined period (configured by the ini file parameter, IDSAlarmClearPeriod)
during which no thresholds have been crossed. However, this "quiet" period must
be at least twice the 'Threshold Window' value (configured in ''Configuring IDS
Policies'' on page 171). For example, if you set IDSAlarmClearPeriod to 20 sec
and 'Threshold Window' to 15 sec, the IDSAlarmClearPeriod parameter is
ignored and the alarm is cleared only after 30 seconds (2 x 15 sec).
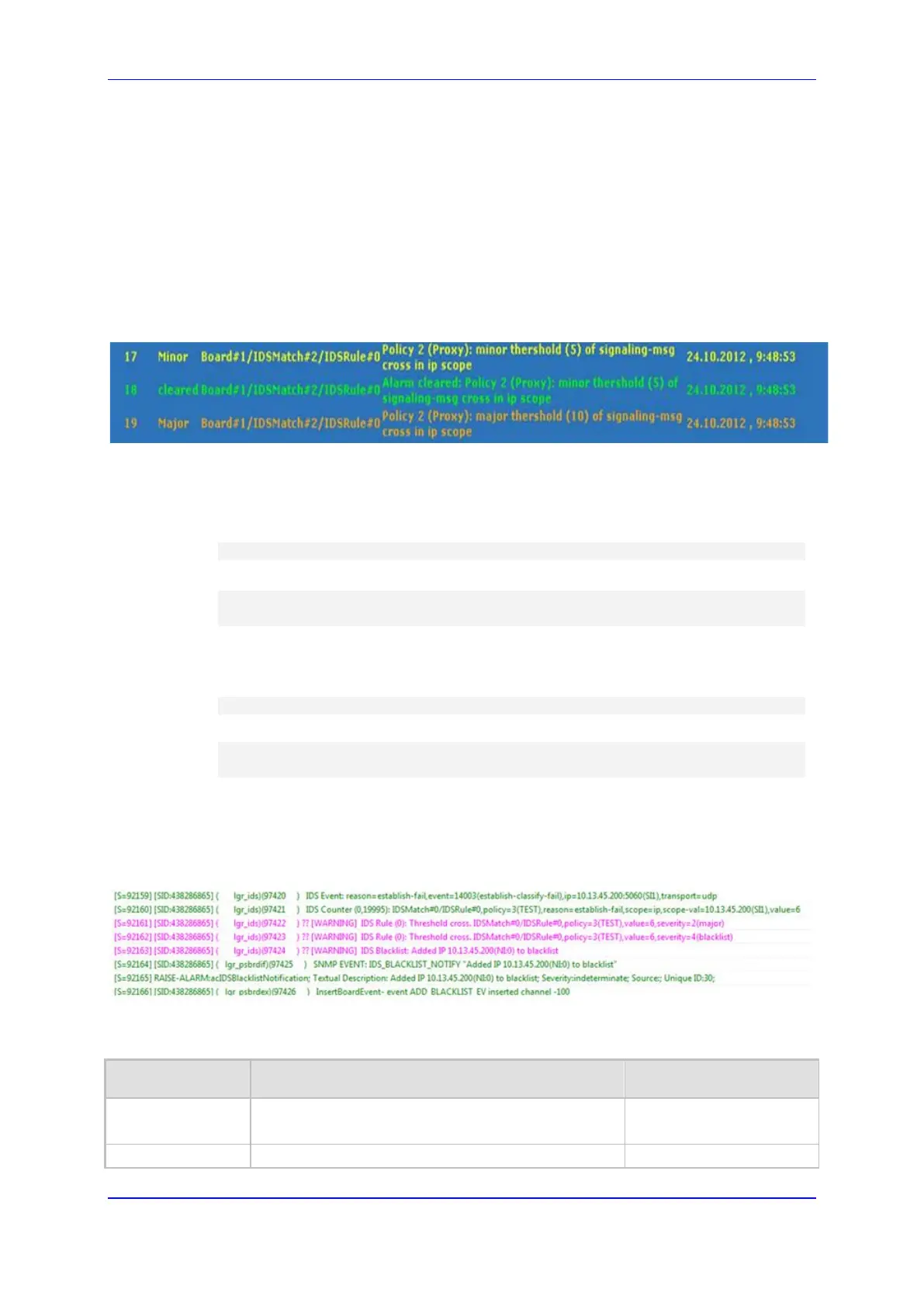
The figure below displays an example of IDS alarms in the Active Alarms table
(''Viewing Active Alarms'' on page 681). In this example, a Minor threshold alarm
is cleared and replaced by a Major threshold alarm:
Figure 16-8: IDS Alarms in Active Alarms Table
acIDSBlacklistNotification event: The device sends this event whenever an attacker
(remote host at IP address and/or port) is added to or removed from the blacklist.
You can also view IDS alarms in the CLI, using the following commands:
To view all active IDS alarms:
# show voip security ids active-alarm all
To view all IP addresses that have crossed the threshold for an active IDS alarm:
# show voip security ids active-alarm match <IDS Match Policy ID> rule <IDS Rule
ID>
The IP address is displayed only if the 'Threshold Scope' parameter is set to IP or
IP+Port; otherwise, only the alarm is displayed.
To view the blacklist:
# show voip security ids blacklist active
For example:
Active blacklist entries:
10.33.5.110(NI:0) remaining 00h:00m:10s in blacklist
Where SI is the SIP Interface and NI is the network interface.
The device also sends IDS notifications and alarms in Syslog messages to a Syslog
server. This occurs only if you have configured Syslog (see ''Enabling Syslog'' on page
737). An example of a Syslog message with IDS alarms and notifications is shown below:
Figure 16-9: Syslog Message Example with IDS Alarms and Notifications
The table below lists the Syslog text messages per malicious event:
Table 16-6: Types of Malicious Events and Syslog Text String
Type Description Syslog String
Connection
Abuse
TLS authentication failure abuse-tls-auth-fail
Message exceeds a user-defined maximum

 Loading...
Loading...



