3GS Technical Manual
7-4 Programming Overview
Issue 4.5 August 2005
Intruder
System
Overview
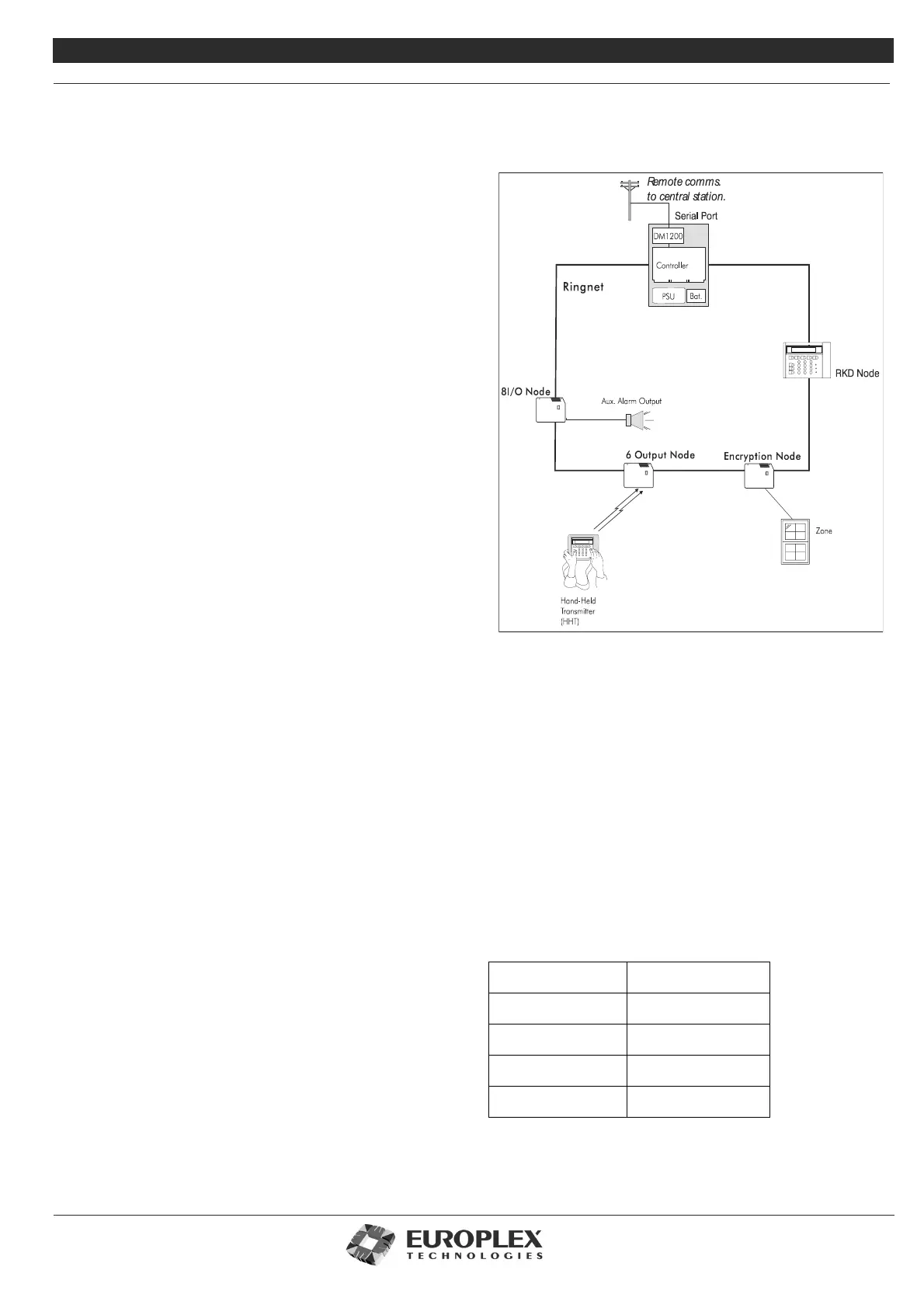
The main intruder system components are detailed below. The
diagram opposite shows an example of this configuration.
Users
The 3GS system supports up to 255 intruder system users.
Each user by default has a 6 digit long user code.
User 1, by default, is the engineer user, with default user code
001010 and a default set of engineering options, detailed in
the Menus chapter, which can not be altered.
User 2, by default, is the master user, with a default user code
of 001020 and a default set of master options, also detailed in
the Menus chapter, which can not be altered.
There are three special users, which are for logging purposes
only; user 37 is a timed user, user 38 is a remote user and user
39 is an access control user. These special users have no user
options and no user code. All other users can be given a subset
of the master user options.
Zones
The 3GS currently has the facility for up to two hundred alarm
zone inputs and sixty four alarm door zone inputs. Zones are
added to the system using end of line resistors (EOL’s). Each
node on the 3GS, except for the 6 or 8 Output node, has the
capacity for zones. A node input is assigned a zone number on
power up. All inputs on all nodes do not have to be used.
These zones are configured on the intruder system by
assigning zone types and attributes (detailed in the Menus
chapter), which determine the behaviour and actions of the
system in various modes.
Areas
The 3GS system can be sub divided into areas. These areas
may be set/armed and unset/disarmed individually. Users and
RKDs may be assigned to one or more areas and only users
with rights to these areas will be allowed to set/arm or unset/
disarm them. Area related messages can only be viewed at
RKDs assigned to the area. Zones and doors can also be
assigned to an area so that when an area is armed, both zones
and doors are also armed.
Outputs
The 3GS outputs can be configured to respond to intruder
alarm events. The system has a set of default outputs (detailed
in the Menus chapter), which are tripped under certain
conditions. The nodes must be configured to have node
outputs mapped to output types. More than one node output
may be assigned to the same output type.
Intruder Log
The intruder log stores one thousand log events, which are
date and time stamped. This log provides a record of all
intruder and system activity (keypad input, status alerts, alarm
activations, and so on). It can be viewed on the RKD nodes or
printed if a hard-copy is required. The detail and length of the
log provides an invaluable record of the system operation for
both fault finding and intrusion alarm analysis.
When the log reaches maximum capacity, further events will
cause the oldest events to be erased. Log events will be stored
for a minimum of 30 days if there is a power failure.
System Summary
Alarm Users 255
Alarm Outputs 255
Alarm Zones 200
Areas 30
Alarm Log 1000
 Loading...
Loading...