Firewall Protection
148
ProSecure Unified Threat Management (UTM) Appliance
Attack Checks, VPN Pass-through, and Multicast Pass-through
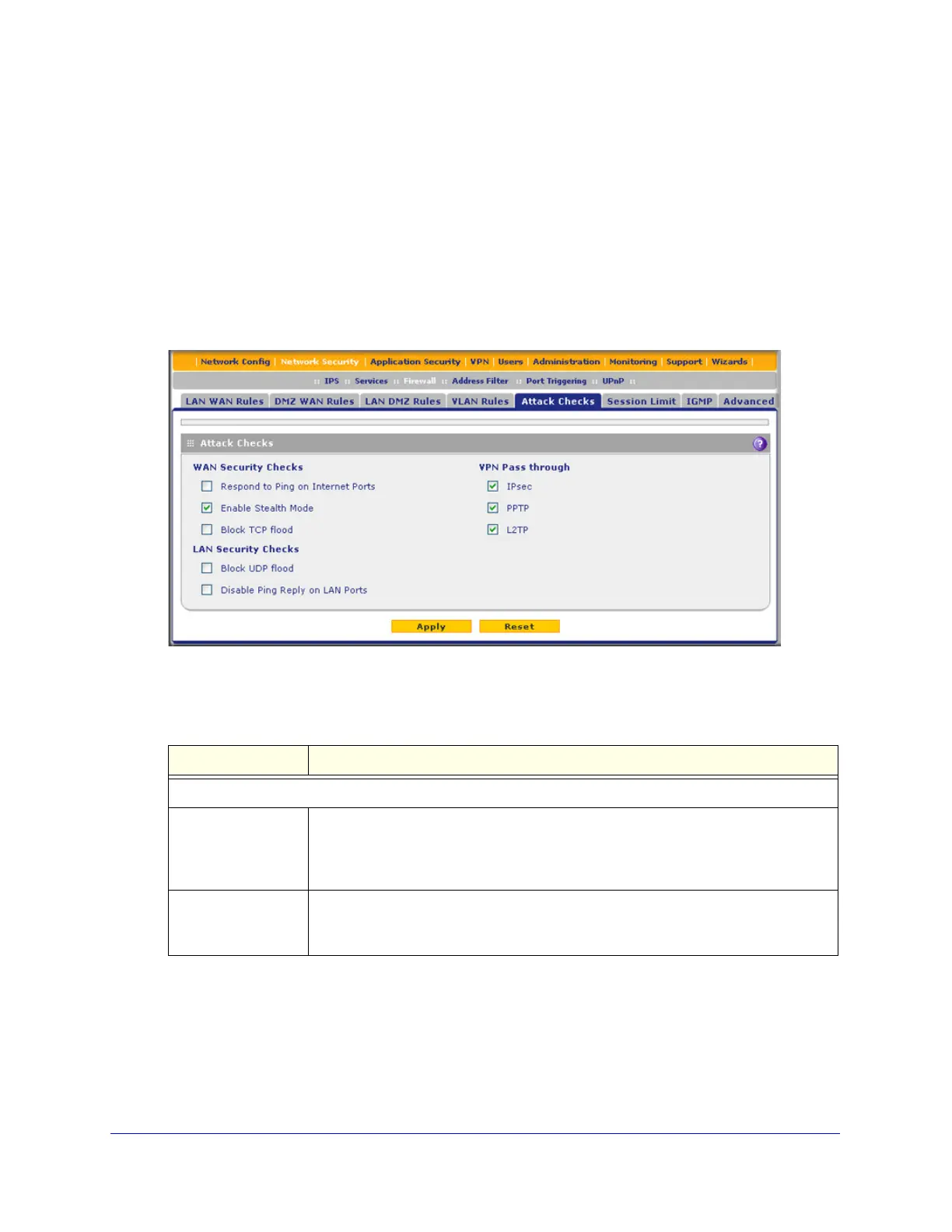
The Attack Checks screen allows you to specify whether or not the UTM should be protected
against common attacks in the DMZ, LAN, and WAN networks, and lets you configure VPN
pass-through and multicast pass-through. The various types of attack checks are listed on
the Attack Checks screen and defined in Table 30 on page 148.
To enable the appropriate attack checks for your network environment:
1. Select Network Security > Firewall > Attack Checks. The Attack Checks screen
displays:
Figure 81.
2. Enter the settings as explained in the following table:
Table 30. Attack Checks screen settings
Setting Description
WAN Security Checks
Respond to Ping on
Internet Ports
Select the Respond to Ping on Internet Ports check box to enable the UTM to
respond to a ping from the Internet. A ping can be used as a diagnostic tool. Keep
this check box cleared unless you have a specific reason to enable the UTM to
respond to a ping from the Internet.
Enable Stealth Mode Select the Enable Stealth Mode check box (which is the default setting) to prevent
the UTM from responding to port scans from the WAN, thus making it less
susceptible to discovery and attacks.
 Loading...
Loading...











