Monitoring System Access and Performance
448
ProSecure Unified Threat Management (UTM) Appliance
Configure and Activate Firewall Logs
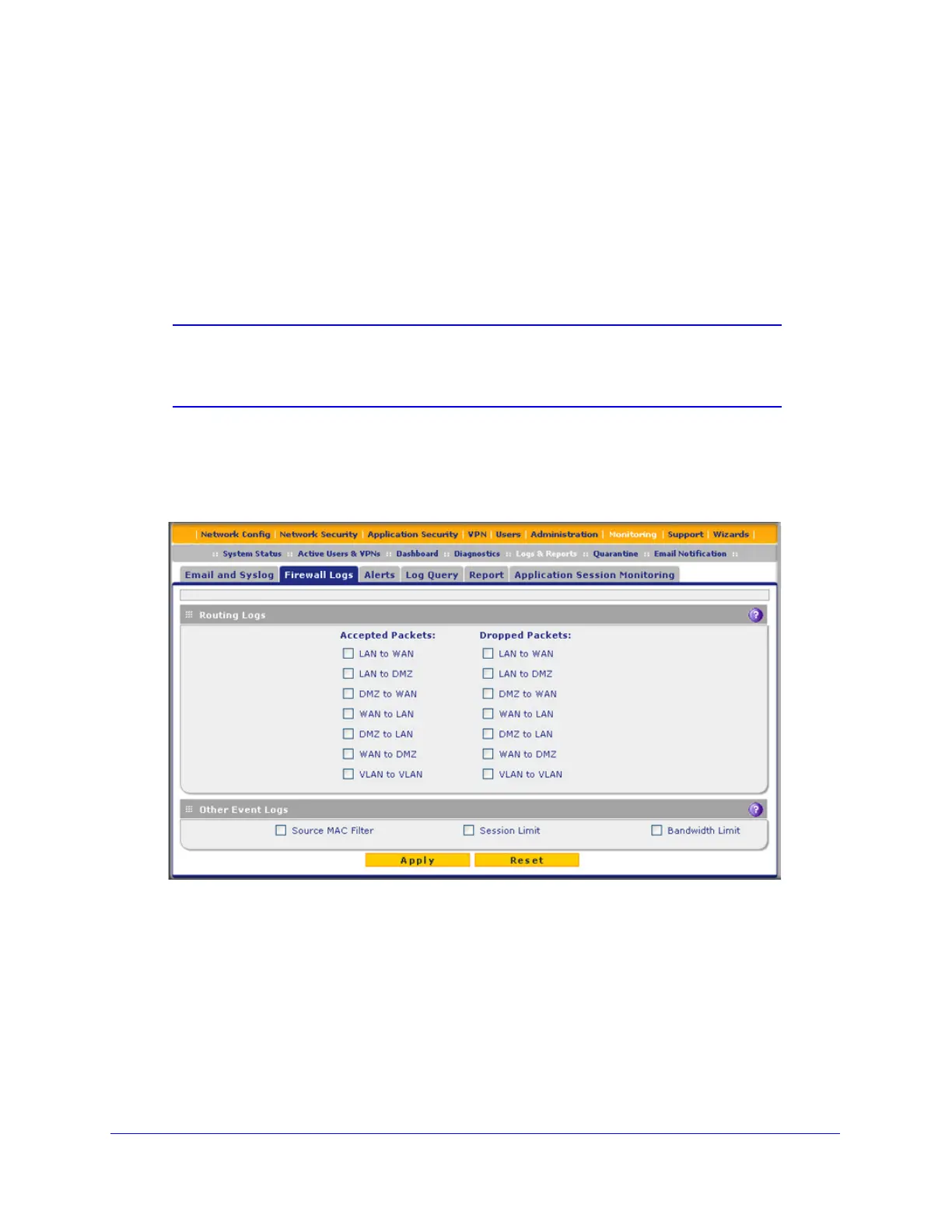
You can configure the logging options for each network segment. For example, the UTM can
log accepted packets for LAN-to-WAN traffic, dropped packets for WAN-to-DMZ traffic, and
so on. You can also configure logging of packets from MAC addresses that match the source
MAC address filter settings (see Enable Source MAC Filtering on page 170), and packets
that are dropped because the session limit (see Set Session Limits on page 151), bandwidth
limit (see Create Bandwidth Profiles on page 162), or both, have been exceeded.
Note: Enabling firewall logs might generate a significant volume of log
messages. NETGEAR recommends that you enable firewall logs for
debugging purposes only.
To configure and activate firewall logs:
1. Select Monitoring > Logs & Reports > Firewall Logs. The Firewall Logs screen
displays:
Figure 265.
2. Enter the settings as explained in the following table:
 Loading...
Loading...











