Monitoring System Access and Performance
489
ProSecure Unified Threat Management (UTM) Appliance
After you have selected one or more table entries, take one of the following actions (or click
the return link to return to the previous screen):
• Send as Spam. The selected spam email files are tagged as spam for distributed spam
analysis, and are sent to the intended recipients.
• Send as Ham. The selected spam email files are not tagged as spam for distributed
spam analysis, are removed from quarantine, and are sent to the intended recipients.
• Delete. The selected spam email files are removed from quarantine and deleted.
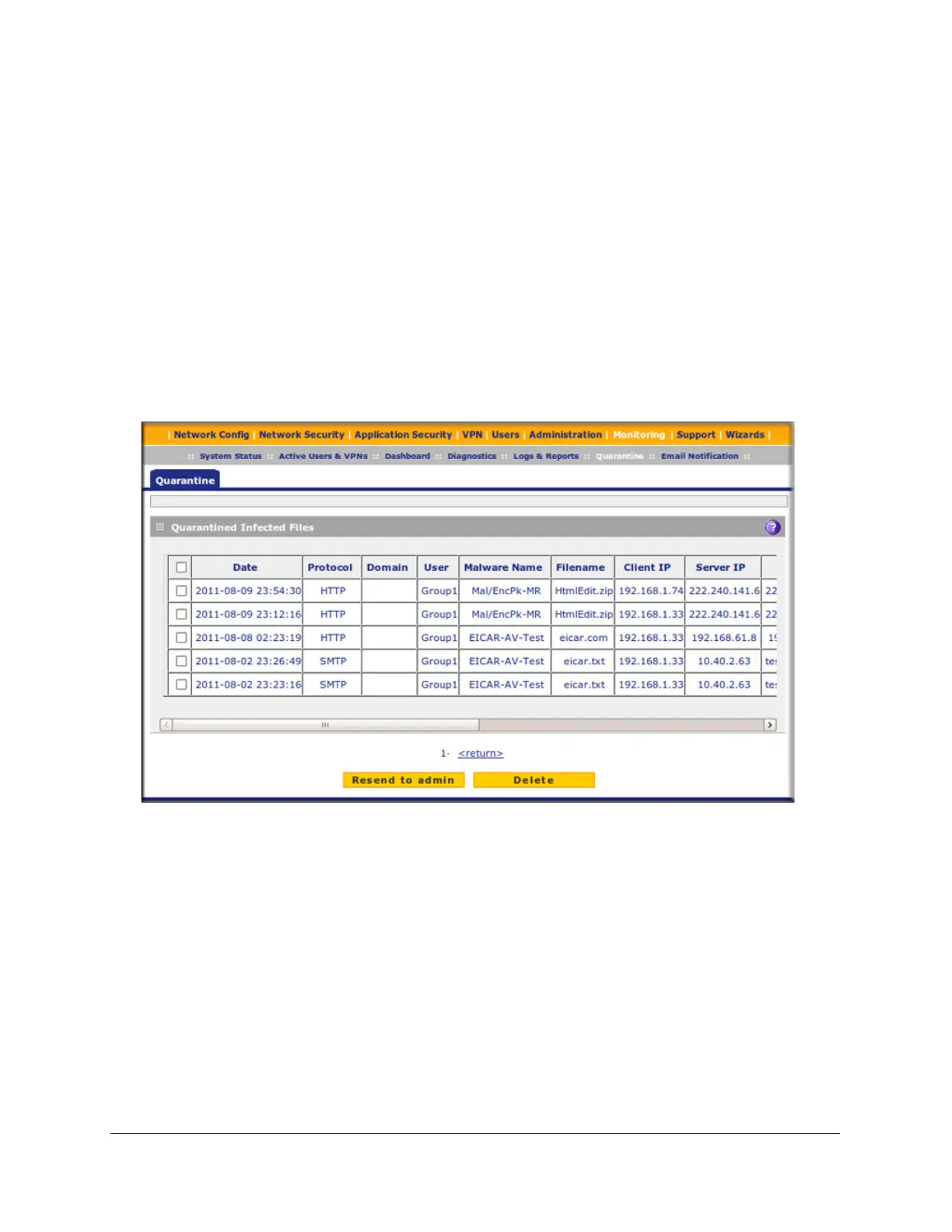
View and Manage the Quarantined Infected Files Table
When you query the malware quarantine file, the Quarantine screen with the Quarantined
Infected Files table displays:
Figure 291.
The Quarantined Infected Files table has the following columns (not all columns are shown in
the previous figure):
• Check box. Lets you select the table entry.
• Date. The date that the file was received.
• Protocol. The protocol (SMTP, POP3, IMAP, HTTP, FTP, HTTPS) in which the spyware
or virus was found.
• Domain. The domain name that was used to log in to the UTM.
• User. The user name that was used to log in to the UTM.
• Malware Name. The name of the spyware or virus.
• Filename. The name of the file in which the spyware or virus was found.
 Loading...
Loading...











