Content Filtering and Optimizing Scans
223
ProSecure Unified Threat Management (UTM) Appliance
Specify Trusted Hosts
You can specify trusted hosts for which the UTM bypasses HTTPS traffic scanning and
security certificate authentication. The security certificate is sent directly to the client for
authentication, which means that the user does not receive a security alert for trusted hosts.
For more information about security alerts, see Manage Self-Signed Certificates on
page 400.
Note that certain sites contain elements from different HTTPS hosts. As an example, assume
that the https://example.com site contains HTTPS elements from the following three hosts:
• trustedhostserver1.example.com
• trustedhostserver2.example.com
• imageserver.example.com
To completely bypass the scanning of the https://example.com site, you need to add all three
hosts to the trusted hosts list because different files from these three hosts are also
downloaded when a user attempts to access the https://example.com site.
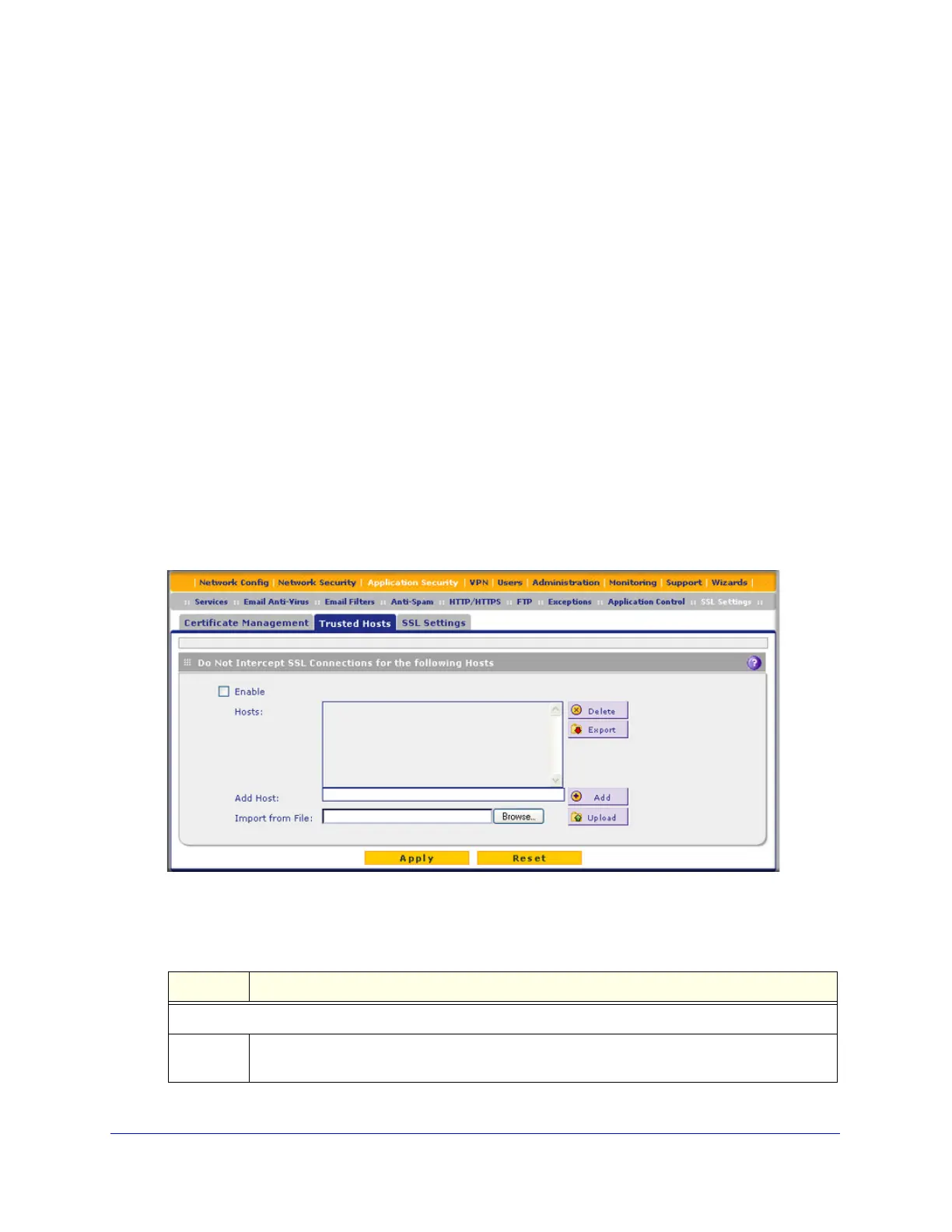
To specify trusted hosts:
1. Select Application Security > SSL Settings > Trusted Hosts. The Trusted Hosts
screen displays.
Figure 125.
2. Enter the settings as explained in the following table:
Table 50. Trusted Hosts screen settings
Setting Description
Do Not Intercept HTTPS Connections for the following Hosts
Enable Select this check box to bypass scanning of trusted hosts that are listed in the Hosts field.
Users do not receive a security alert for trusted hosts that are listed in the Hosts field.
 Loading...
Loading...











