Monitoring System Access and Performance
491
ProSecure Unified Threat Management (UTM) Appliance
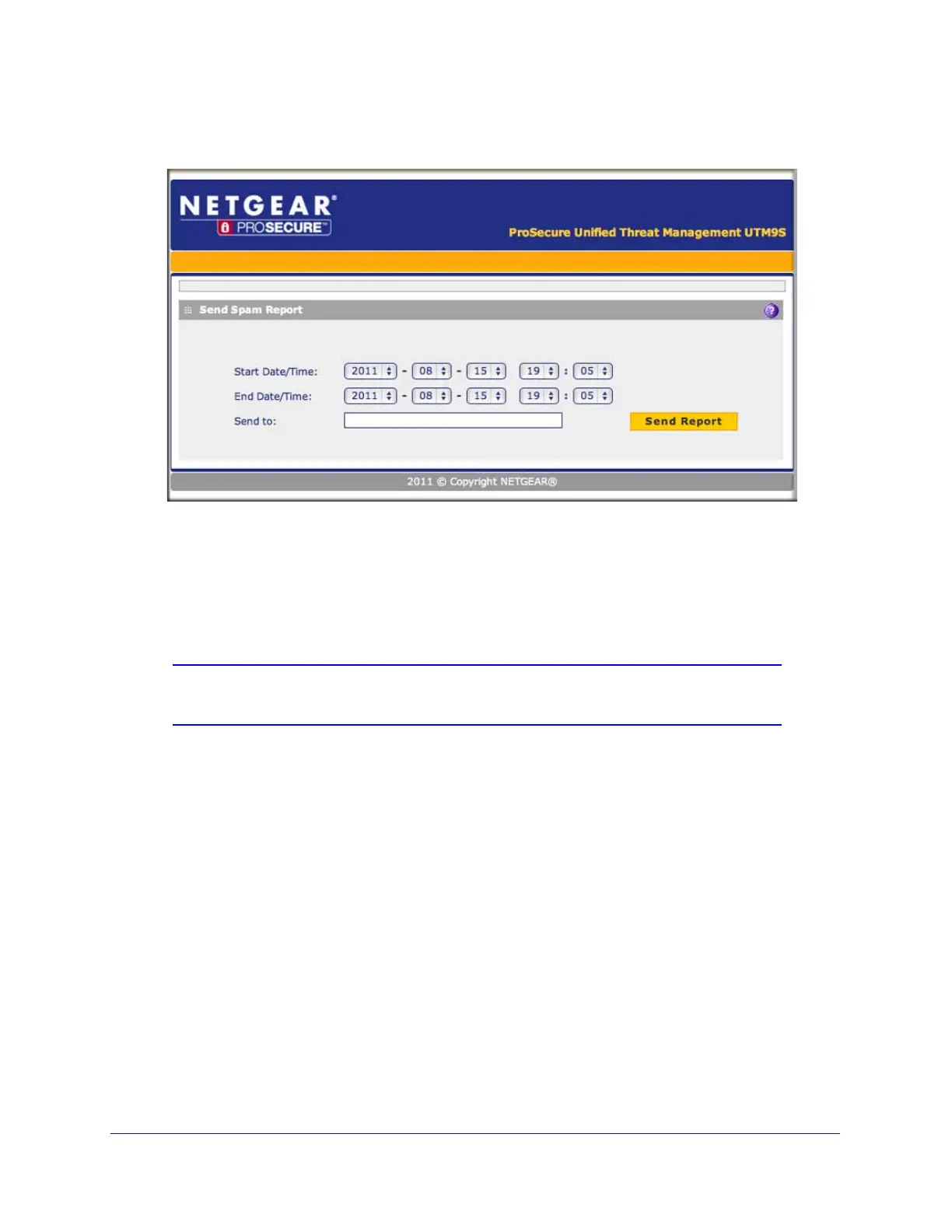
2. Click the here link in the Check your quarantined mail here section. The following screen
displays:
Figure 293.
3. From the drop-down lists, specify the start date, start time, end date, and end time for the
spam report.
4. In the Send to field, enter an email address.
5. Click Send Report.
Note: The spam report contains only spam messages that were sent to the
email address that is specified in the Send to field.
View, Schedule, and Generate Reports
The reporting functions of the UTM let you perform the following tasks that help you to
monitor the protection of the network and the performance of the UTM:
• Generating, viewing, and downloading web activity, IPS and application, email activity,
and system reports
• Scheduling automatic web activity, IPS and application, email activity, and system
reports, and emailing these reports to specified recipients
You can view the reports onscreen, download them to your computer, and configure the UTM
to send them to one or more email addresses.
 Loading...
Loading...











