Using the Setup Wizard to Provision the UTM in Your Network
53
ProSecure Unified Threat Management (UTM) Appliance
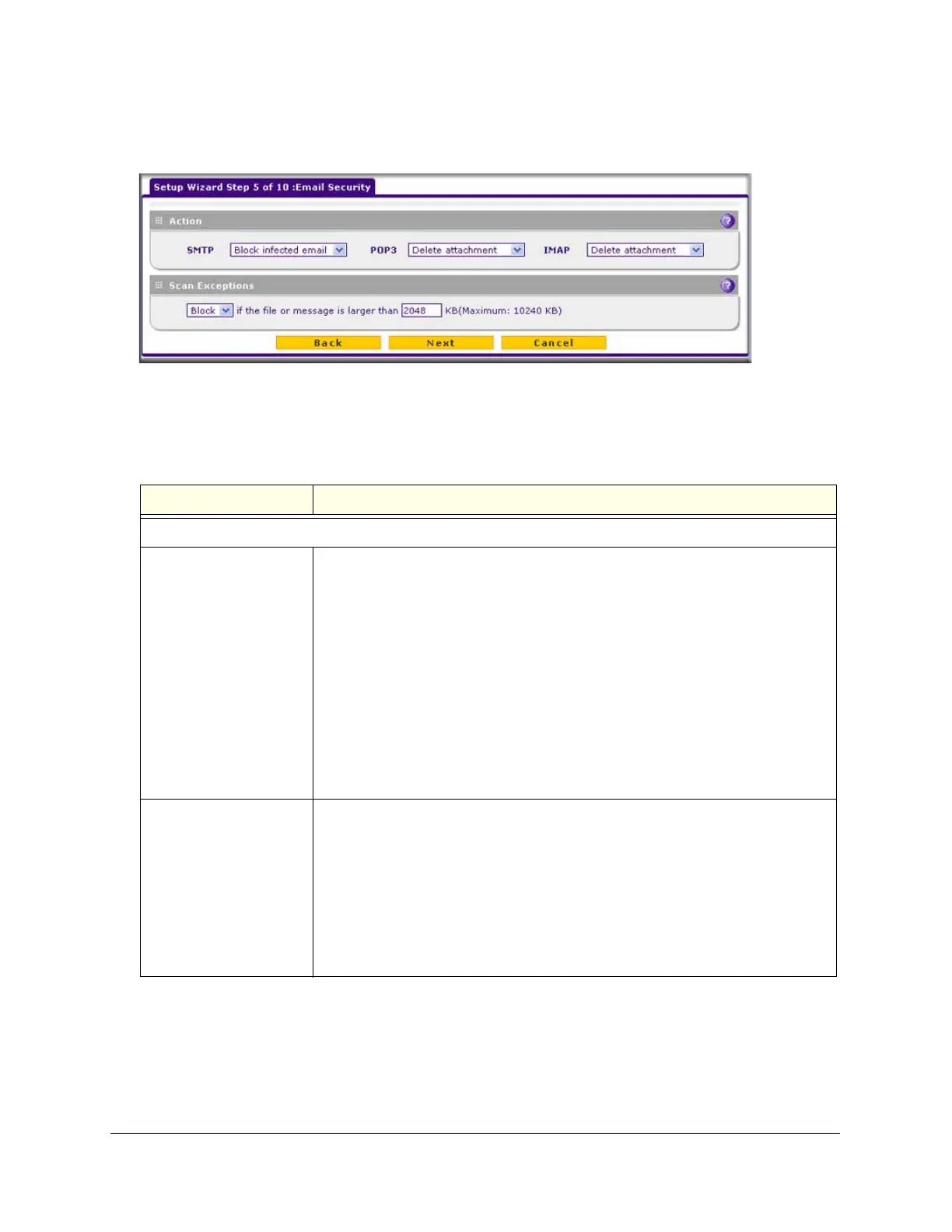
Setup Wizard Step 5 of 10: Email Security
Figure 29.
Enter the settings as explained in the following table, and then click Next to go the following
screen.
Table 8. Setup Wizard Step 5: Email Security screen settings
Setting Description
Action
SMTP From the SMTP drop-down list, select one of the following actions to be taken when
an infected email is detected:
• Block infected email. This is the default setting. The email is blocked, and a
log entry is created.
• Delete attachment. The email is not blocked, but the attachment is deleted,
and a log entry is created.
• Log only. Only a log entry is created. The email is not blocked, and the
attachment is not deleted.
• Quarantine attachment. The email is not blocked, but the attachment is
quarantined on a ReadyNAS, and a log entry is created (see the Note on page
184).
• Quarantine infected email. The email is quarantined on a ReadyNAS, and a
log entry is created (see the Note on page 184).
POP3 From the POP3 drop-down list, select one of the following actions to be taken when
an infected email is detected:
• Delete attachment. This is the default setting. The email is not blocked, but
the attachment is deleted, and a log entry is created.
• Log only. Only a log entry is created. The email is not blocked, and the
attachment is not deleted.
• Quarantine attachment. The email is not blocked, but the attachment is
quarantined on a ReadyNAS, and a log entry is created (see the Note on
page 184).
 Loading...
Loading...











