Content Filtering and Optimizing Scans
184
ProSecure Unified Threat Management (UTM) Appliance
Note: For information about how to monitor blocked content and malware
threats in real time, see Monitor Real-Time Traffic, Security, and
Statistics on page 449. For information about how to view blocked
content and malware threats in the logs, see Query the Logs on
page 478.
Note: The UTM can quarantine spam and malware only if you have
integrated a ReadyNAS (see Connect to a ReadyNAS on page 431)
and configured the quarantine settings (see Configure the
Quarantine Settings on page 432).
Default Email and Web Scan Settings
For most network environments, the default scan settings and actions that are shown in the
following table work well, but you can adjust these to the needs of your specific environment.
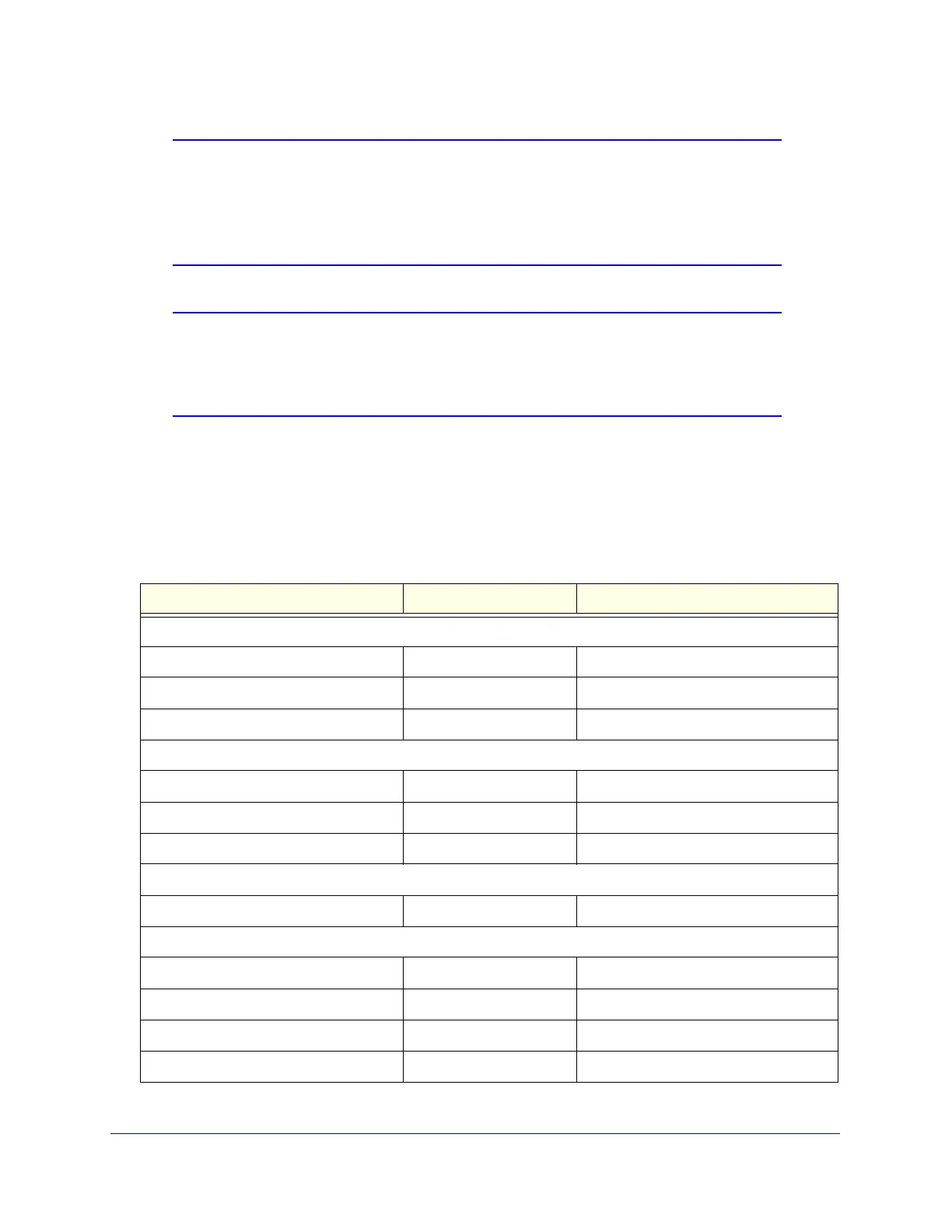
Table 41. Default email and web scan settings
Scan type Default scan setting Default action (if applicable)
Email server protocols
SMTP Enabled Block infected email
POP3 Enabled Delete attachment if infected
IMAP Enabled Delete attachment if infected
Web server protocols
a
HTTP Enabled Delete file if malware threat detected
HTTPS Disabled No action (scan disabled)
FTP Enabled Delete file if malware threat detected
Applications
All applications Allowed
Web objects
Embedded Objects (ActiveX/Java/Flash Allowed
Javascript Allowed
Proxy Allowed
Cookies Allowed
 Loading...
Loading...











