Content Filtering and Optimizing Scans
222
ProSecure Unified Threat Management (UTM) Appliance
To view details of a trusted certificate:
1. From the Trusted Certificates table, select the certificate.
2. Click View Details. A new screen opens that displays the details of the certificate.
To delete a trusted certificate:
1. From the Trusted Certificates table, select the certificate.
2. Click Delete Selected.
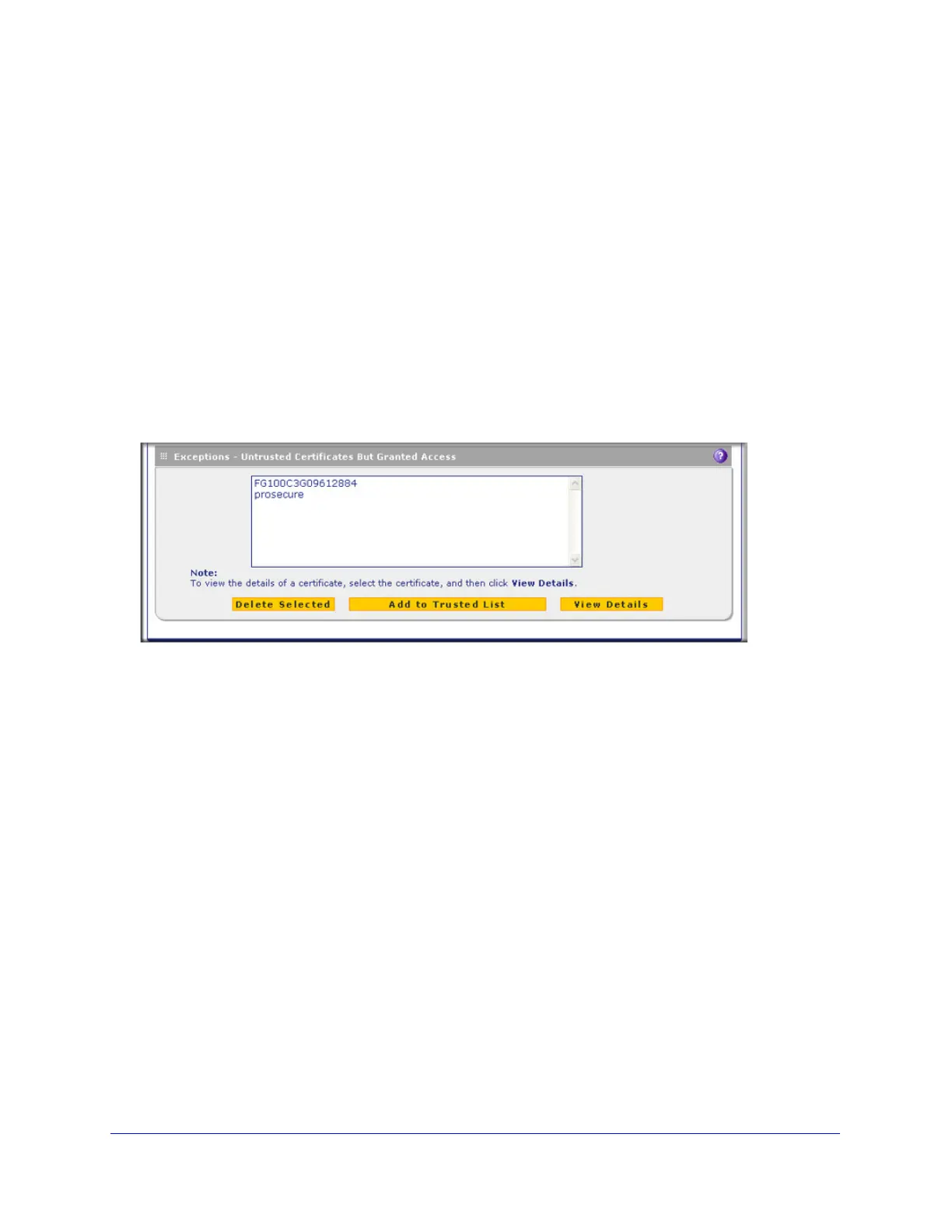
Manage Untrusted HTTPS Certificates
To manage untrusted certificates, select Web Security > Certificate Management. The
Certificate Management screen displays. The following figure shows only the Exceptions -
Untrusted Certificates But Granted Access section of the screen:
Figure 124. Certificate management, screen 3 of 3
When the UTM detects an untrusted or invalid certificate, it automatically places the
certificate in the Exceptions - Untrusted Certificates But Granted Access table.
To view details of an untrusted certificate:
1. From the Exceptions - Untrusted Certificates But Granted Access table, select the
certificate.
2. Click View Details. A new screen opens that displays the details of the certificate.
To delete an untrusted certificate:
1. From the Exceptions - Untrusted Certificates But Granted Access table, select the
certificate.
2. Click Delete Selected.
To move an untrusted certificate to the Trusted Certificate Authorities table:
1. From the Exceptions - Untrusted Certificates But Granted Access table, select the
certificate.
2. Click Add to Trusted List. The previously untrusted certificate is added to the Trusted
Certificates table.
 Loading...
Loading...











