Managing Users, Authentication, and VPN Certificates
402
ProSecure Unified Threat Management (UTM) Appliance
3. Click the Generate table button. A new SCR is created and added to the Self Certificate
Requests table.
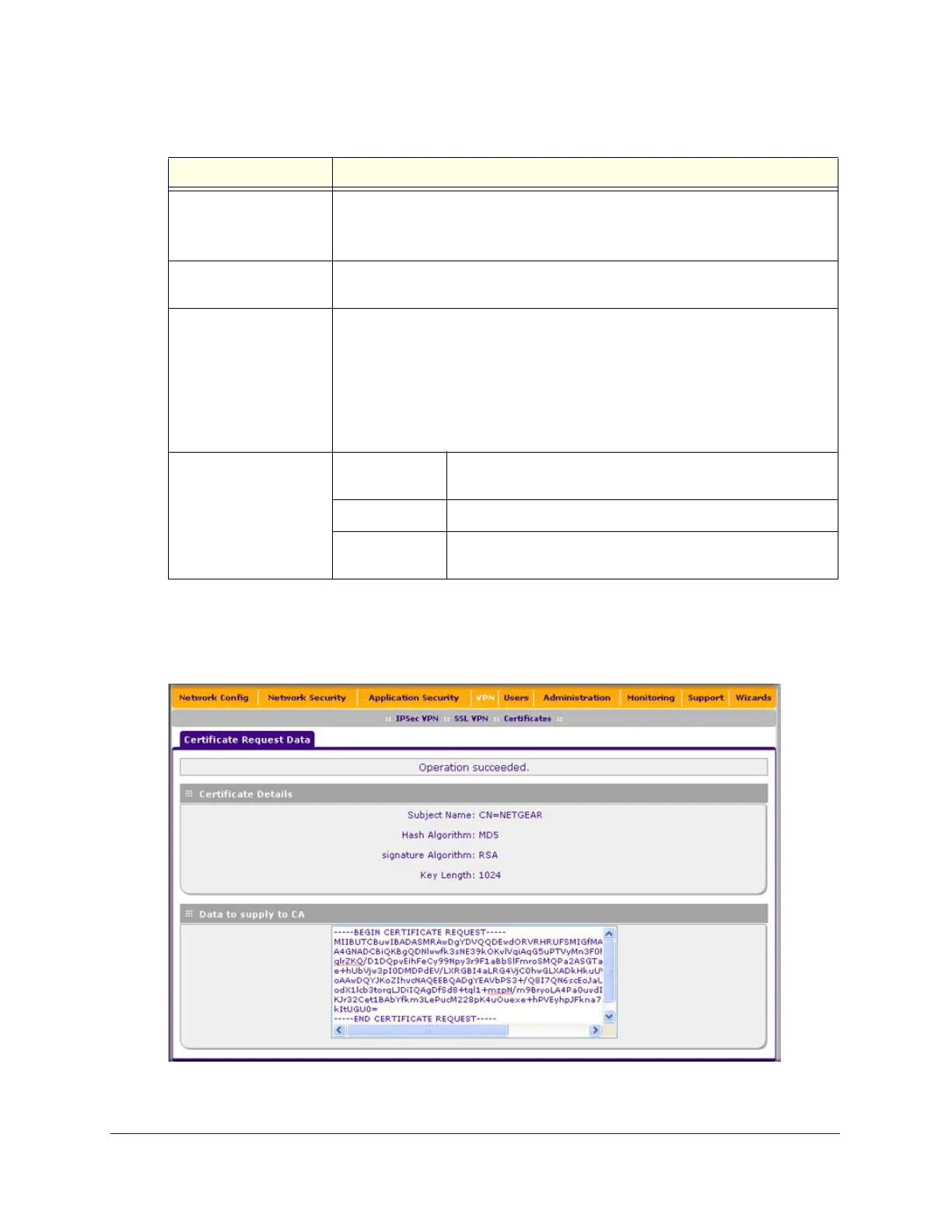
4. In the Self Certificate Requests table, click the View table button in the Action column to
view the new SCR. The Certificate Request Data screen displays:
Figure 246.
Hash Algorithm From the drop-down list, select one of the following hash algorithms:
• MD5. A 128-bit (16-byte) message digest, slightly faster than SHA-1.
• SHA-1. A 160-bit (20-byte) message digest, slightly stronger than MD5.
Signature Algorithm Although this seems to be a drop-down list, the only possible selection is RSA. In
other words, RSA is the default to generate a CSR.
Signature Key Length From the drop-down list, select one of the following signature key lengths in bits:
•512
• 1024
• 2048
Note: Larger key sizes might improve security, but might also decrease
performance.
Optional Fields IP Address Enter your fixed (static) IP address. If your IP address is
dynamic, leave this field blank.
Domain Name Enter your Internet domain name, or leave this field blank.
E-mail Address Enter the email address of a technical contact in your
company.
Table 102. Generate self-signed certificate request settings (continued)
Setting Description
 Loading...
Loading...











