Virtual Private Networking Using IPSec Connections
275
ProSecure Unified Threat Management (UTM) Appliance
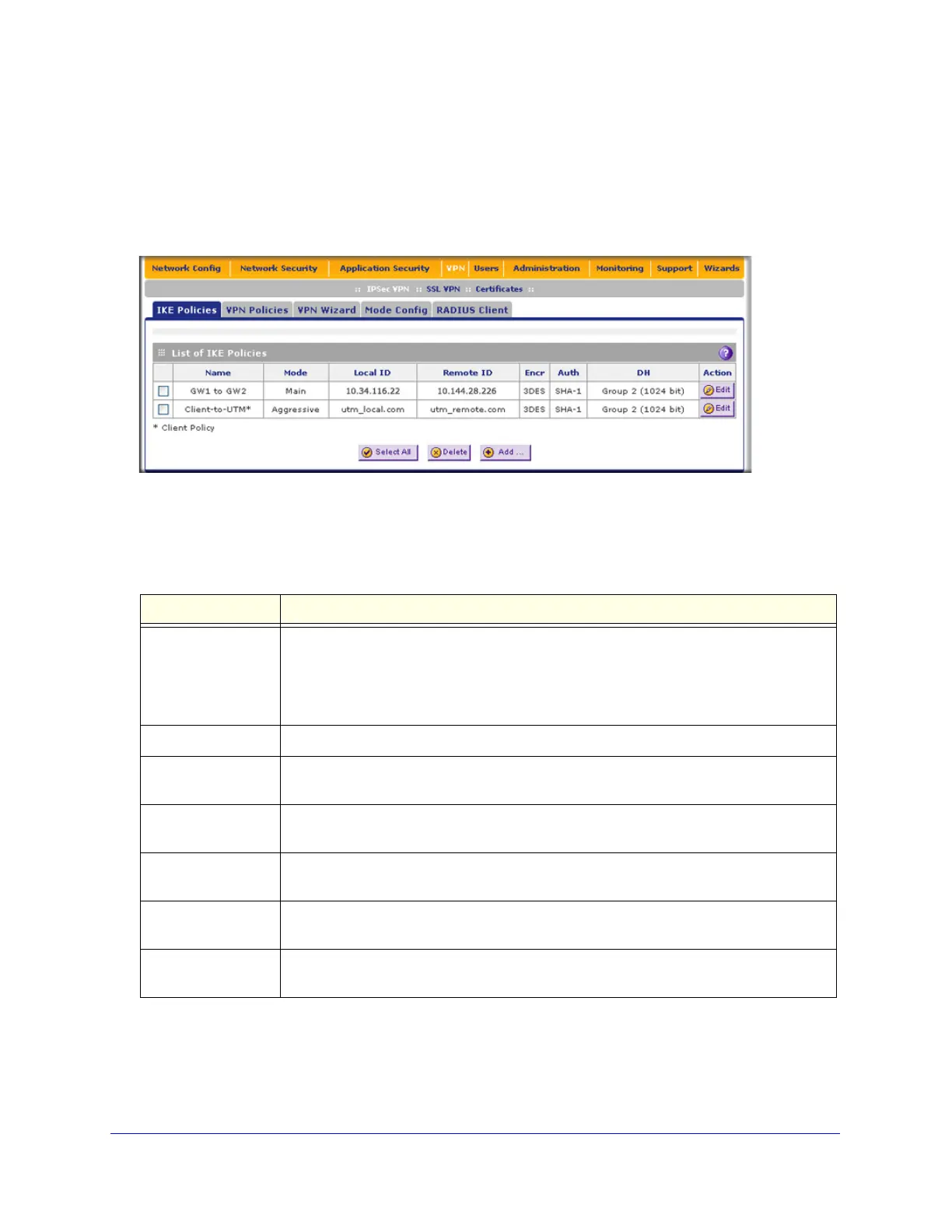
IKE Policies Screen
To access the IKE Policies screen:
Select VPN > IPSec VPN. The IPSec VPN submenu tabs display with the IKE Policies
screen in view. (The following figure shows some examples.)
Figure 171.
Each policy contains the data that are explained in the following table. These fields are
explained in more detail in Table 67 on page 278.
Table 66. List of IKE Policies table information
Setting Description
Name The name that identifies the IKE policy. When you use the VPN Wizard to set up a VPN
policy, an accompanying IKE policy is automatically created with the same name that you
select for the VPN policy.
Note: The name is not supplied to the remote VPN endpoint.
Mode The exchange mode: Main or Aggressive.
Local ID The IKE/ISAKMP identifier of the UTM. The remote endpoint needs to have this value as
its remote ID.
Remote ID The IKE/ISAKMP identifier of the remote endpoint, which needs to have this value as its
local ID.
Encr The encryption algorithm that is used for the IKE security association (SA). This setting
needs to match the setting on the remote endpoint.
Auth The authentication algorithm that is used for the IKE SA. This setting needs to match the
setting on the remote endpoint.
DH The Diffie-Hellman (DH) group that is used when keys are exchanged. This setting needs
to match the setting on the remote endpoint.
 Loading...
Loading...











