Monitoring System Access and Performance
486
ProSecure Unified Threat Management (UTM) Appliance
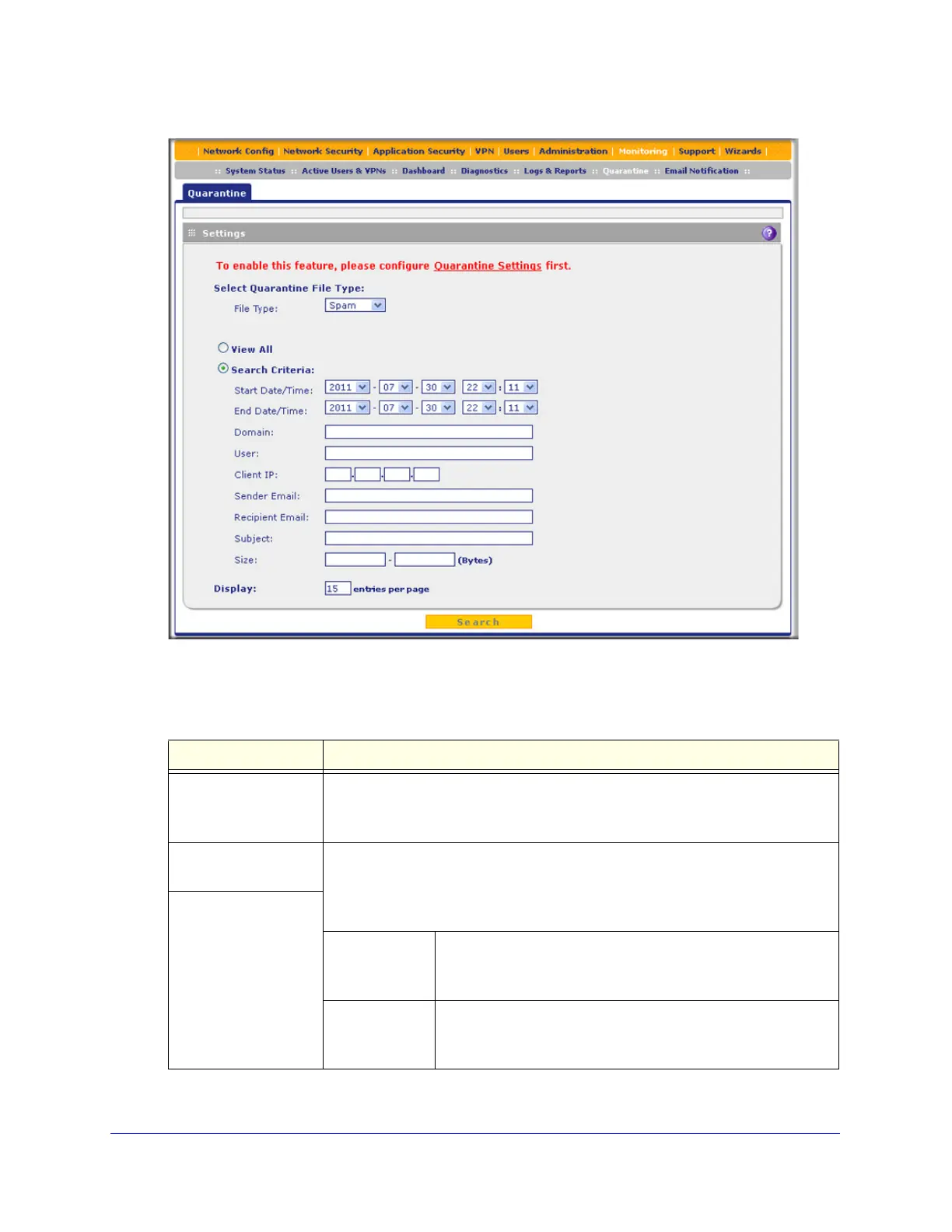
Figure 289.
2. Enter the settings as explained in the following table:
Table 129. Quarantine screen settings
Setting Description
File Type Select one of the following file types from the drop-down list:
• Spam. All intercepted spam.
• Malware. All intercepted viruses, spyware, and other malware threats.
View All Select one of the following radio buttons:
• View All. Display or download the entire selected log.
• Search Criteria. Query the selected log by configuring the search criteria that
are available for the selected log.
Search Criteria
Start Date/Time From the drop-down lists, select the year, month, day, hours,
and minutes for the start date and time.
This field is available for both the Spam and Malware logs.
End Date/Time From the drop-down lists, select the year, month, day, hours,
and minutes for the end date and time.
This field is available for both the Spam and Malware logs.
 Loading...
Loading...











