Page 98 of 237
Version: 5.1.6 – June 4
th
, 2019
As your client is to be authenticated by the client certificate, it also needs
the private key for this certificate. As shown in Figure 112, export the client certificate using export format
PKCS #12 with Certificate chain. When you click OK,
the client certificate will save to the location that you specified above. The client certificate then has the file
extension .p12.
You must use the PEM (file extension .crt) format when exporting the root certificate.
These certificates can then be imported to the mbNET router via the web interface (cf. section System –
Certificates).
For an explanation of how to set up these certificates for a Windows client, see Importing certificates in
Windows XP.
Generating CRL-Files (Certificate Revocation Lists)
If you wish to withdraw a team member’s rights to use the
VPN tunnel, please read this section and create a certificate
revocation list.
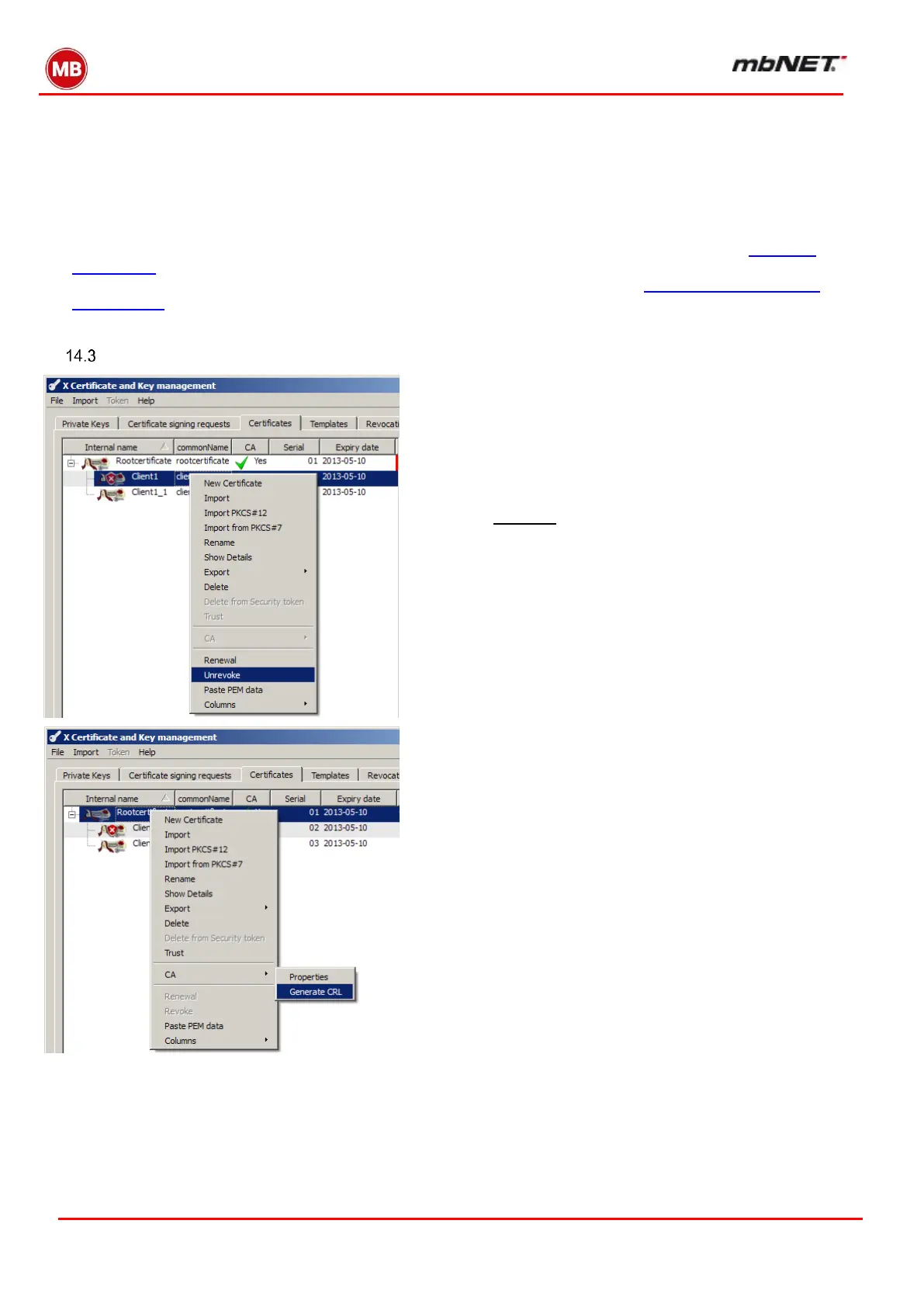
To do this, re-open XCA. Open the database containing
your team member’s certificate. To confirm a certificate as in-
valid, right-click on it and the dialog box below will appear:
Clicking on “Revoke” flags the relevant certificate with a red X,
and it is no longer valid. To remove the flag and make the certif-
icate entry valid again, click on “Unrevoke” as shown in the
screenshot.
Next, right-click on the associated root certificate.
The following dialog box will appear:
You can create a revocation list here using
“CA Generate CRL”,
as shown in the screenshot above. Please ensure that under
“hash algorithm”, you also select MD5. There are no check
boxes to enable for extensions. The CRL must now be ex-
ported, and then imported to the mbNET.

 Loading...
Loading...


