6-88 Motorola RF Switch System Reference Guide
4. If a Crypto Map with a manual security association requires revision, select it from amongst those
displayed and click the Edit button to revise its Seq #, IKE Peer, ACL ID and security protocol.
5. Select an existing table entry and click the Delete button to remove it from the list of those available to
the switch.
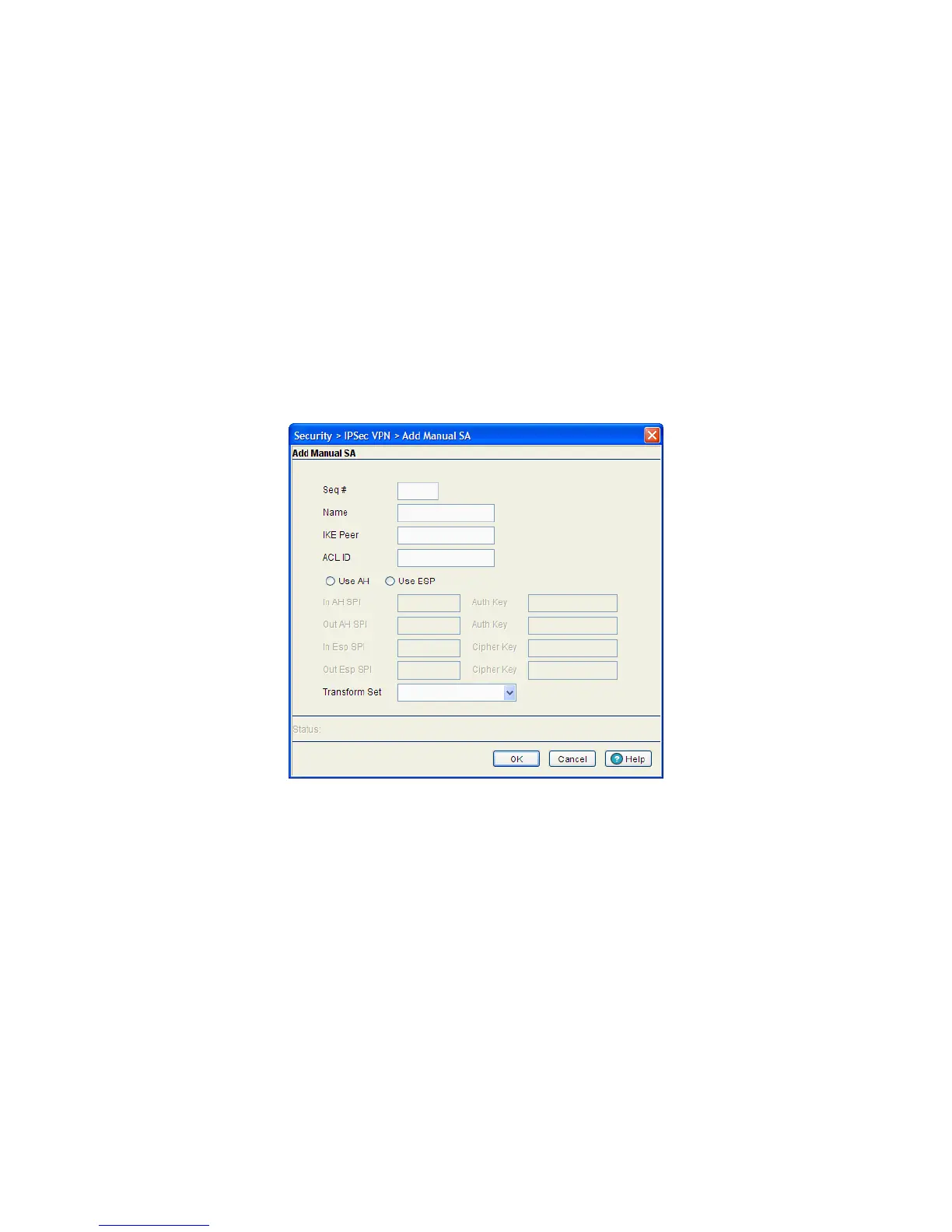
6. If a new Crypto Map manual security association requires creation, click the Add button.
a. Define the Seq #. The sequence number determines priority among Crypto Maps. The lower the
number, the higher the priority.
b. Provide a unique Name for this Crypto Map to differentiate it from others with similar
configurations.
c. Enter the name of the IKE Peer used to build an IPSec security association.
d. Use the ACL ID drop-down menu to permit a Crypto Map data flow using the unique permissions
within the selected ACL.
e. Select either the AH or ESP radio button to define whether the Crypto Map’s manual security
association is an AH Transform Authentication scheme or an ESP Encryption Transform scheme. The
AH SPI or ESP SPI fields become enabled depending on the radio button selected.
f. Define the In AH SPI and Auth Keys or In Esp and Cipher Keys depending on which option has
been selected.
g. Use the Transform Set drop-down menu to select the transform set representing a combination of
security protocols and algorithms. During the IPSec security association negotiation, peers agree to
IKE Peer Displays the IKE peer used with the Crypto Map to build an IPSec security
association.
ACL ID Displays the ACL ID the Crypto Map’s data flow uses to establish access
permissions.
Transform Set Displays the transform set representing a combination of security protocols and
algorithms. During the security association negotiation, peers agree to use a
particular transform set for protecting the data flow.

 Loading...
Loading...