6-22 Motorola RF Switch System Reference Guide
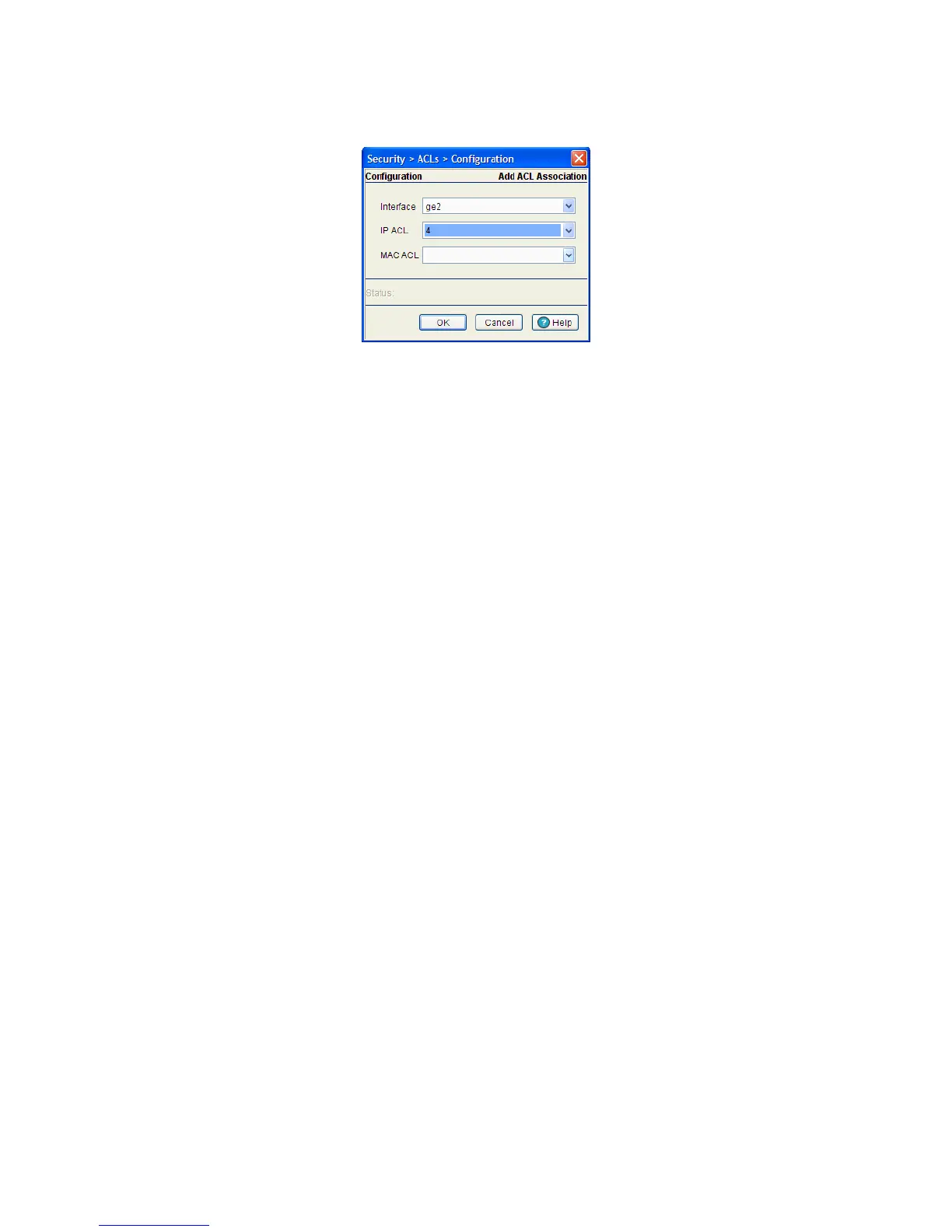
4. Click the Add button.
5. Use the Interface drop-down menu to select the interface to configure on the switch. Available options
include – ge 1-8, up 1, VLAN 1 (plus those VLANs created thus far) and Tunnel n (where n equals the
name(s) of those tunnels created thus far).
6. Use the IP ACL drop-down menu to select an IP ACL used as the inbound IP for the layer 2 or layer 3
interface.
7. Use the MAC ACL drop-down menu to select an MAC ACL used as the MAC IP for the layer 2 interface.
8. Refer to the Status field for the state of the requests made from applet. This field displays error
messages if something goes wrong in the transaction between the applet and the switch.
9. Click OK to use the changes to the running configuration and close the dialog.
10.Click Cancel to close the dialog without committing updates to the running configuration.
6.4.4 Configuring the Role Based Firewall
Use the Attach Role screen to view and assign an ACL to a role.
To attach a role:
1. Select Security > Wireless Firewall from the main menu tree.
2. Click the Security Policy tab.

 Loading...
Loading...