DocID018909 Rev 11 765/1731
RM0090 Hash processor (HASH)
788
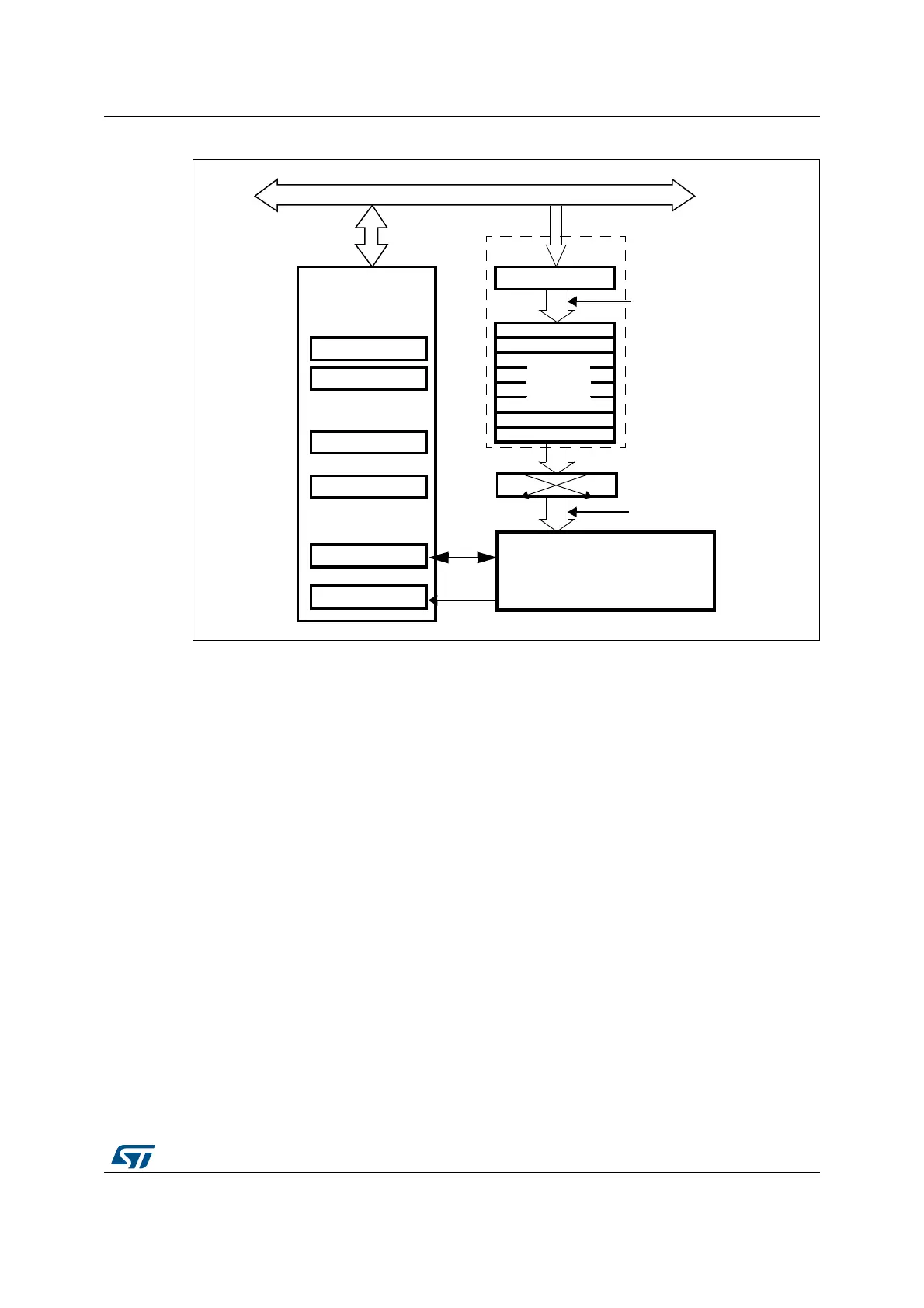
Figure 234. Block diagram for STM32F43xxx
The FIPS PUB 180-2 standard and the IETF RFC 1321 publication specify the SHA-1, SHA-
224 and SHA-256 and MD5 secure hash algorithms, respectively, for computing a
condensed representation of a message or data file. When a message of any length below
2
64
bits is provided on input, the SHA-1, SHA-224 and SHA-256 and MD5 produce
respective a 160-bit, 224 bit, 256 bit and 128-bit output string, respectively, called a
message digest. The message digest can then be processed with a digital signature
algorithm in order to generate or verify the signature for the message. Signing the message
digest rather than the message often improves the efficiency of the process because the
message digest is usually much smaller in size than the message. The verifier of a digital
signature has to use the same hash algorithm as the one used by the creator of the digital
signature.
The SHA-1, SHA-224 and SHA-256 and MD5 are qualified as “secure” because it is
computationally infeasible to find a message that corresponds to a given message digest, or
to find two different messages that produce the same message digest. Any change to a
message in transit will, with very high probability, result in a different message digest, and
the signature will fail to verify. For more detail on the SHA-1 or SHA-224 and SHA-256
algorithm, please refer to the FIPS PUB 180-2 (Federal Information Processing Standards
Publication 180-2), 2002 august 1.
The current implementation of this standard works with little-endian input data convention.
For example, the C string “abc” must be represented in memory as the 24-bit hexadecimal
value 0x434241.
A message or data file to be processed by the hash processor should be considered a bit
string. The length of the message is the number of bits in the message (the empty message
BIT!("BUS
(ASH(-!#
3(!3(!3(!AND-$
(!3(?$).
SWA PPIN G
§BIT
).&)&/
(!3(?#2
(!3(?((
(!3(?#32
CONTEXT
DIGEST
(!3(?)-2
(!3(?32
)NTERRUPTREGISTERS
#ONTROLREGISTER
#ONTEXTSWAPPING
-ESSAGEDIGEST
PROCESSOR CORE
(!3(?34 2
3TARTREGISTER
).&)&/FULL
WRITEINTO(!3(?$).
#ONTROLANDSTATUS
REGISTERS
$ATA
REGISTER
ORWRITE$#!,BITTO
ORCOMPLETEBLOCK
OR$#!,WRITTENTO
).BUFFER
TRANSFERREDBYTHE$-!
-36

 Loading...
Loading...