6-90 Motorola RF Switch System Reference Guide
6.7.4.4 Crypto Map Transform Sets
A transform set is a combination of security protocols and algorithms defining how the switch protects data.
To review, revise or add a Crypto Map transform set:
1. Select Security > IPSec VPN from the main menu tree.
2. Click the Crypto Maps tab and select Transform Sets.
3. Refer to the read-only information displayed within the Transform Sets tab to determine whether a
Crypto Map transform set requires modification or a new one requires creation.
4. Select an existing Crypto Map and click the Edit button to revise its Seq #, Name and Transform Set.
5. Select an existing entry from the table and click the Delete button to remove it from the list.
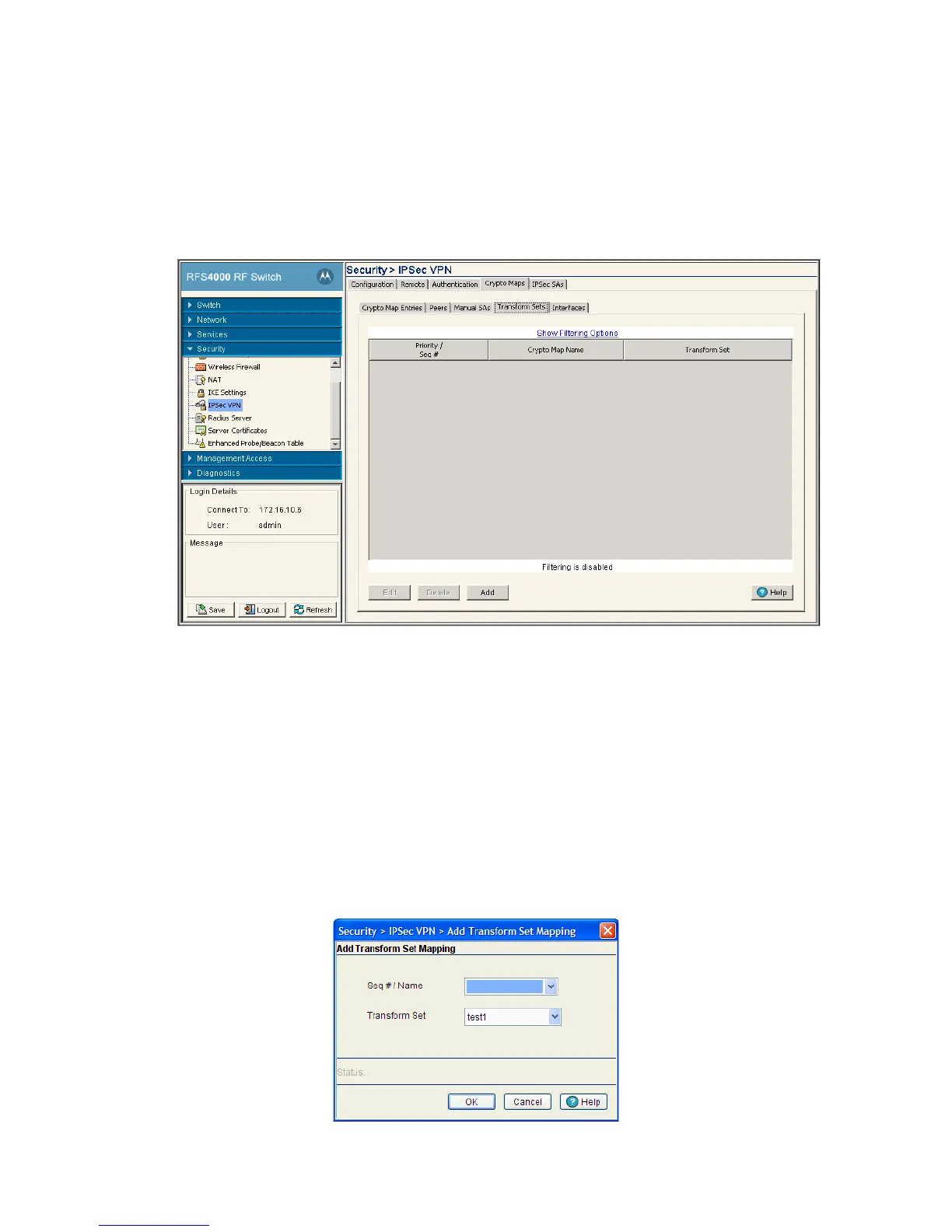
6. If a new Crypto Map transform set requires creation, click the Add button.
Priority / Seq # Displays the Seq # (sequence number) used to determine priority.
Name Displays the name assigned to the Crypto Map that’s using the transform set.
Transform Set Displays the transform set representing a combination of security protocols and
algorithms. During the IPSec security association negotiation, peers agree to use
the transform set for protecting the data flow.

 Loading...
Loading...