Chapter 12
| Security Measures
ARP Inspection
– 341 –
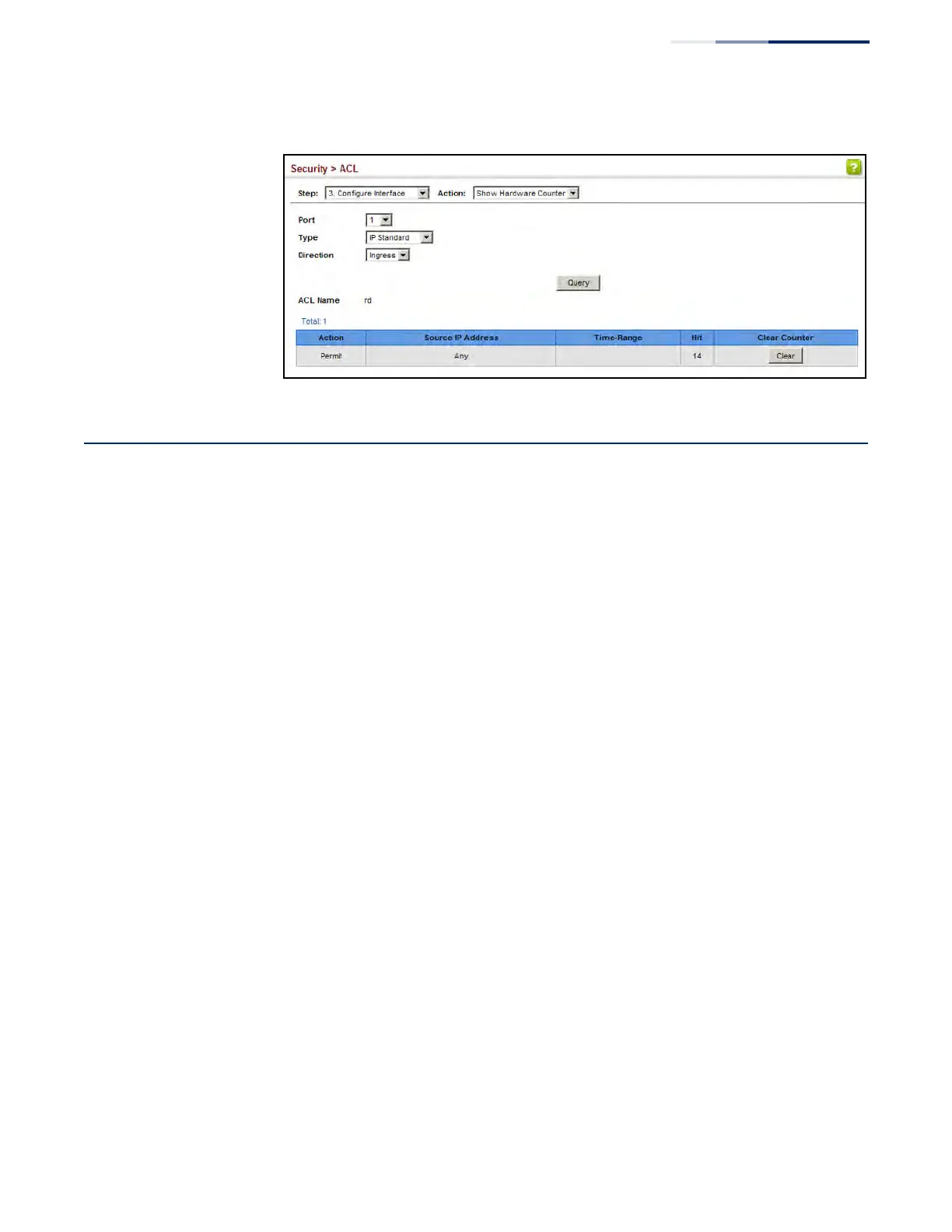
Figure 209: Showing ACL Statistics
ARP Inspection
ARP Inspection is a security feature that validates the MAC Address bindings for
Address Resolution Protocol packets. It provides protection against ARP traffic with
invalid MAC-to-IP address bindings, which forms the basis for certain “man-in-the-
middle” attacks. This is accomplished by intercepting all ARP requests and
responses and verifying each of these packets before the local ARP cache is
updated or the packet is forwarded to the appropriate destination. Invalid ARP
packets are dropped.
ARP Inspection determines the validity of an ARP packet based on valid IP-to-MAC
address bindings stored in a trusted database – the DHCP snooping binding
database (see “DHCP Snooping Configuration” on page 382). This database is built
by DHCP snooping if it is enabled on globally on the switch and on the required
VLANs. ARP Inspection can also validate ARP packets against user-configured ARP
access control lists (ACLs) for hosts with statically configured addresses (see
“Configuring an ARP ACL” on page 335).
Command Usage
Enabling & Disabling ARP Inspection
◆ ARP Inspection is controlled on a global and VLAN basis.
◆ By default, ARP Inspection is disabled both globally and on all VLANs.
■
If ARP Inspection is globally enabled, then it becomes active only on the
VLANs where it has been enabled.
■
When ARP Inspection is enabled globally, all ARP request and reply packets
on inspection-enabled VLANs are redirected to the CPU and their switching
behavior handled by the ARP Inspection engine.
■
If ARP Inspection is disabled globally, then it becomes inactive for all
VLANs, including those where inspection is enabled.

 Loading...
Loading...











