30. Tunnelling
ROX™ v2.2 User Guide 311 RuggedBackbone™ RX5000
Figure 30.12. ESP table
If data is configured, the path to the ESP table will be tunnel/ipsec/connection/{line module}/esp.
Figure 30.13. ESP Key Settings
If data is configured, the path to the ESP Key Settings form will be to click on esp/{line module}.
ESP pertains to the Phase 2 encryption/authentication algorithm to be used for the connection.
Cipher Algorithm
Synopsis: string - one of the following keywords { any, aes128, aes192, aes256, aes, 3des }
Cipher algorithm.
Hash Method
Synopsis: string - one of the following keywords { any, md5, sha1 }
Hash method.
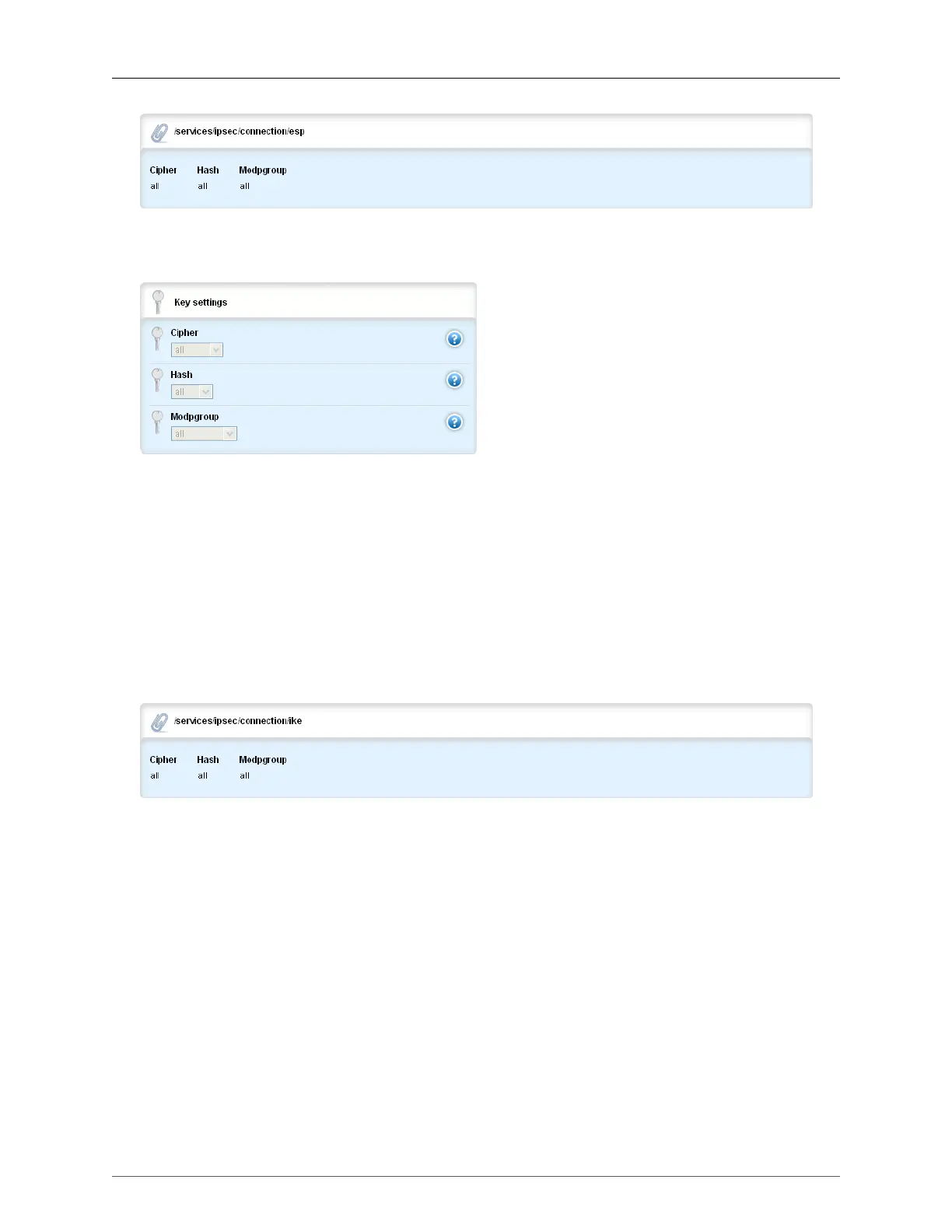
Figure 30.14. IKE table
If data is configured, the path to the IKE table will be tunnel/ipsec/connection/{line module}/ike.
IKE pertains to the Phase 1 encryption/authentication algorithm to be used for the connection. A Key
Settings Form like the ESP Key Settings Form is also used for IKE.
Cipher Algorithm
Synopsis: string - one of the following keywords { any, aes128, aes192, aes256, aes, 3des }
Cipher algorithm.
Hash Method
Synopsis: string - one of the following keywords { any, md5, sha1 }
Hash method.
Modpgroup
Synopsis: string - one of the following keywords { any, modp8192, modp6144, modp4096,
modp3072, modp2048, modp1536, modp1024 }
 Loading...
Loading...