310
Configuring 802.1X
Overview
802.1X is a port-based network access control protocol that was initially proposed by the IEEE 802
LAN/WAN committee for WLAN security. However, it has been widely used on Ethernet for access
control.
802.1X controls network access by authenticating devices connected to the 802.1X-enabled LAN ports.
This chapter describes how to configure 802.1X on an HP device. You can also configure the port security
feature to perform 802.1X. Port security combines and extends 802.1X and MAC authentication. It
applies to a network that requires different authentication methods for different users on a port, such as
a WLAN. It is described in "Configuring port security."
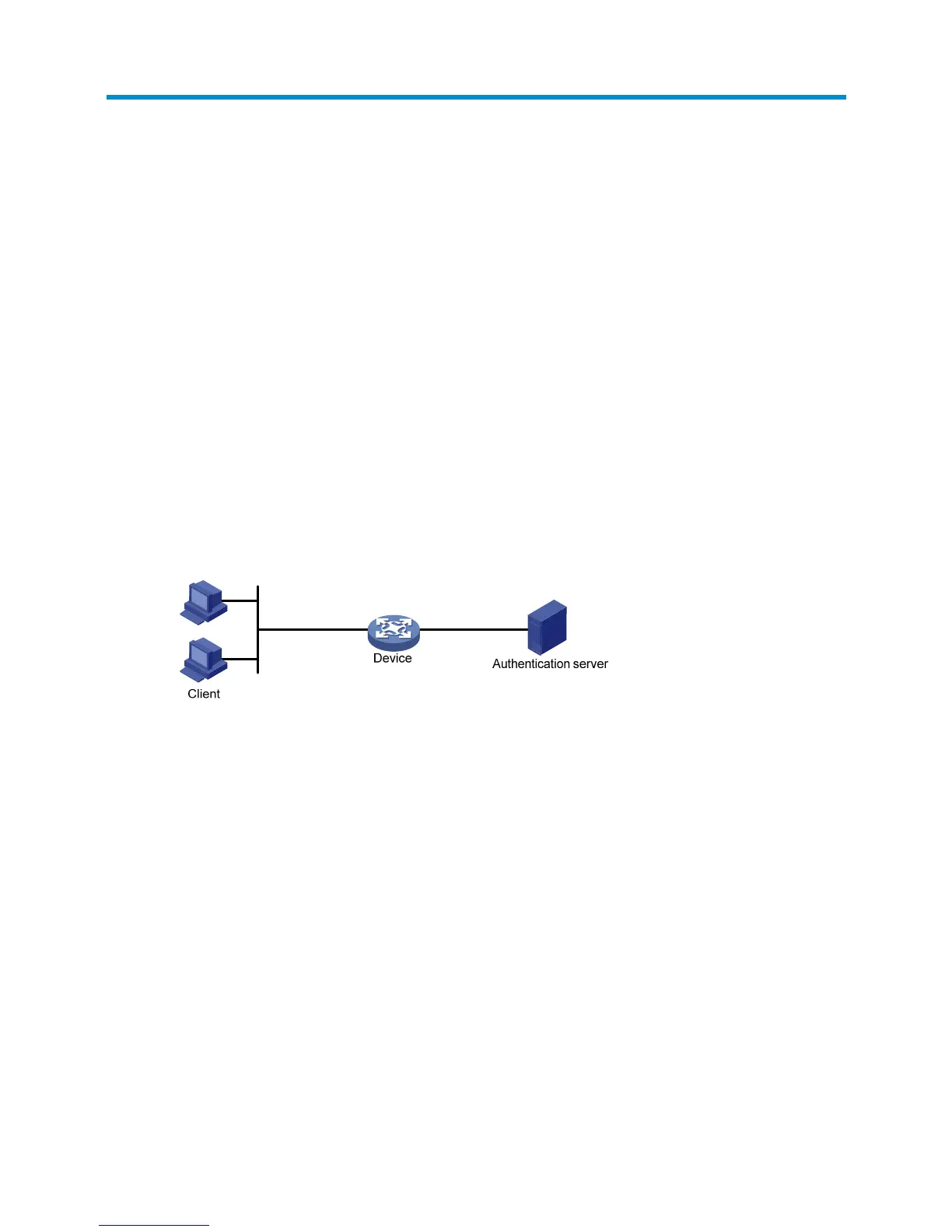
802.1X architecture
802.1X operates in the client/server model. It has the following entities: the client (supplicant), the
network access device (authenticator), and the authentication server.
Figure 302 802.1X architecture
• Client—A user terminal seeking access to the LAN. It must have 802.1X software to authenticate to
the network access device.
• Network access device—Authenticates the client to control access to the LAN. In a typical 802.1X
environment, the network access device uses an authentication server to perform authentication.
• Authentication server—Provides authentication services for the network access device. The
authentication server authenticates 802.1X clients by using the data sent from the network access
device. The server returns the authentication results to the network access device for the device to
make access decisions. The authentication server is typically a RADIUS server. In a small LAN, you
can also use the network access device as the authentication server.
Access control methods
HP implements port-based access control as defined in the 802.1X protocol, and extends the protocol to
support MAC-based access control.
• Port-based access control—Once an 802.1X user passes authentication on a port, any subsequent
user can access the network through the port without authentication. When the authenticated user
logs off, all other users are logged off.

 Loading...
Loading...











