802.1X configuration example
Network requirements
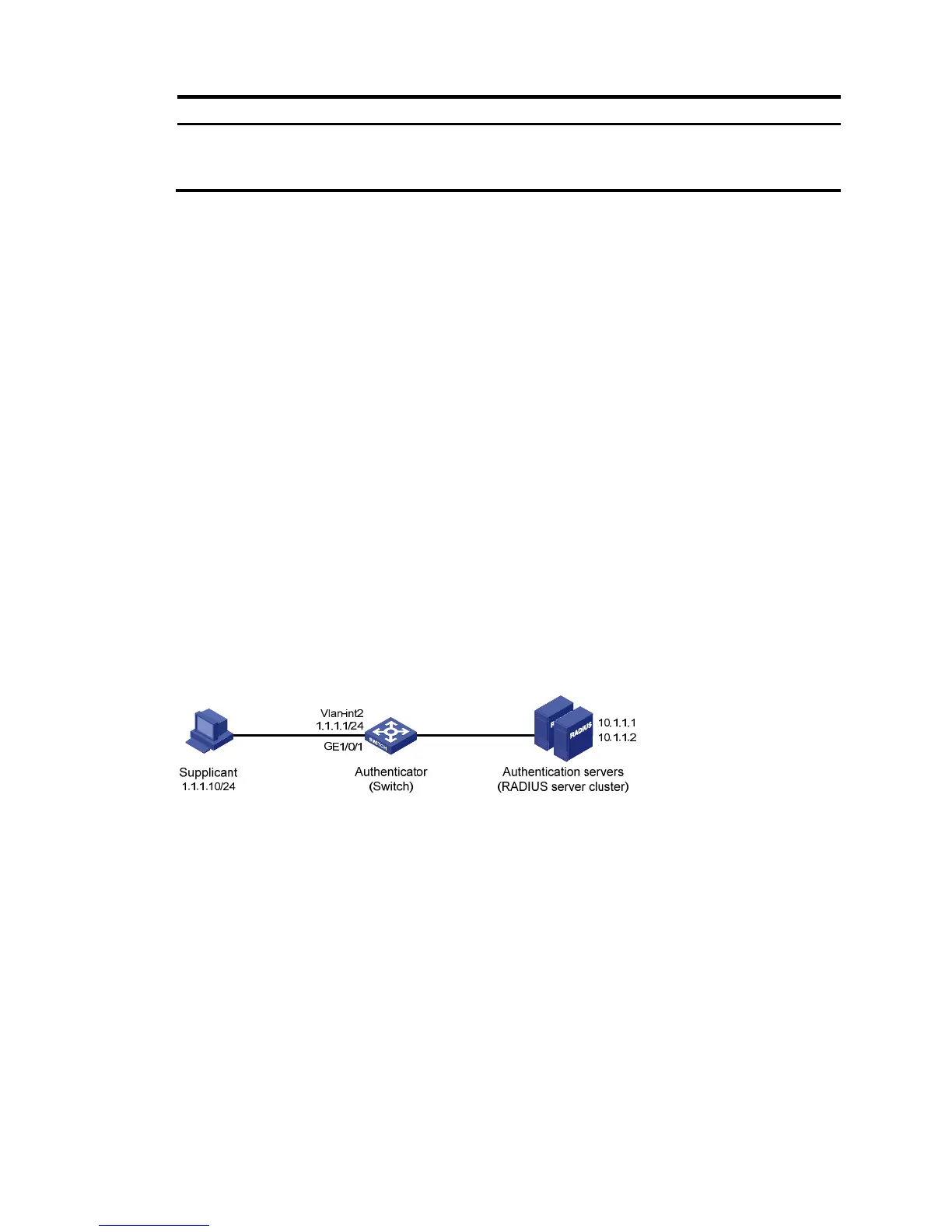
As shown in Figure 306, the access device performs 802.1X authentication for users who connect to port
GigabitEthernet 1/0/1. Implement MAC-based access control on the port, so when one user logs off, it
does not affect other online 802.1X users. Enable periodic re-authentication of online users on the port,
so that the server can periodically update the users' authorization information.
• Use RADIUS servers to perform authentication, authorization, and accounting for the 802.1X users.
If RADIUS accounting fails, the access device logs off the user. The RADIUS servers run on IMC.
• C o n f i g u r e t h e h o s t a t 10 .1.1.1 a s t h e p r i m a r y a u t h entication and secondary accounting servers, and
the host at 10.1.1.2 as the secondary authentication and primary accounting servers. Assign all
users to the ISP domain test.
• Configure the shared key as name for packets between the access device and the authentication
server, and the shared key as money for packets between the access device and the accounting
server.
• Exclude the ISP domain name from the username sent to the RADIUS servers.
• Specify the device to try up to five times at an interval of 5 seconds in transmitting a packet to the
RADIUS server until it receives a response from the server, and to send real time accounting packets
to the accounting server every 15 minutes.
Figure 306 Network diagram
The following configuration procedure applies to RADIUS client configuration on the switch.
Configurations on the RADIUS servers are not shown. For more information about RADIUS configuration,
see "Configuring RADIUS."
Configuration prerequisites
Configure the IP addresses of the interfaces. (Details not shown.)
Configuring 802.1X
1. From the navigation tree, select Authentication > 802.1X.
2. Select the Enable 802.1X box, select the authentication method as CHAP, and click Apply.

 Loading...
Loading...











