Operation Manual – AAA & RADIUS & HWTACACS & EAD
Quidway S3900 Series Ethernet Switches-Release 1510 Chapter 2 EAD Configuration
Huawei Technologies Proprietary
2-2
The security client (software installed on PC) checks the security status of a client that
just passes the authentication, and interacts with the security policy server. If the client
is not compliant with the security standard, the security policy server issues ACL control
packets to the switch, which then grants the client to access the virus patch server only.
After the client is patched and compliant with the required security standard, the
security policy server reissues an ACL to the switch to assign the access right to the
client.
2.3 EAD Configuration
The EAD configuration includes the following:
z Configuring the attributes, such as the user name, user type, and password for
access users. If local authentication is performed, you need to configure these
attributes on the switch; if remote authentication is performed, you need to
configure these attributes on AAA sever.
z Configuring RADIUS scheme.
z Configuring IP address for the security policy server.
z Associating domain with RADIUS scheme.
EAD is implemented typically in RADIUS scheme.
This section mainly describes configuration of IP address for the security policy server.
For other related information, refer to
Chapter 1 “AAA & RADIUS & HWTACACS
Configuration”.
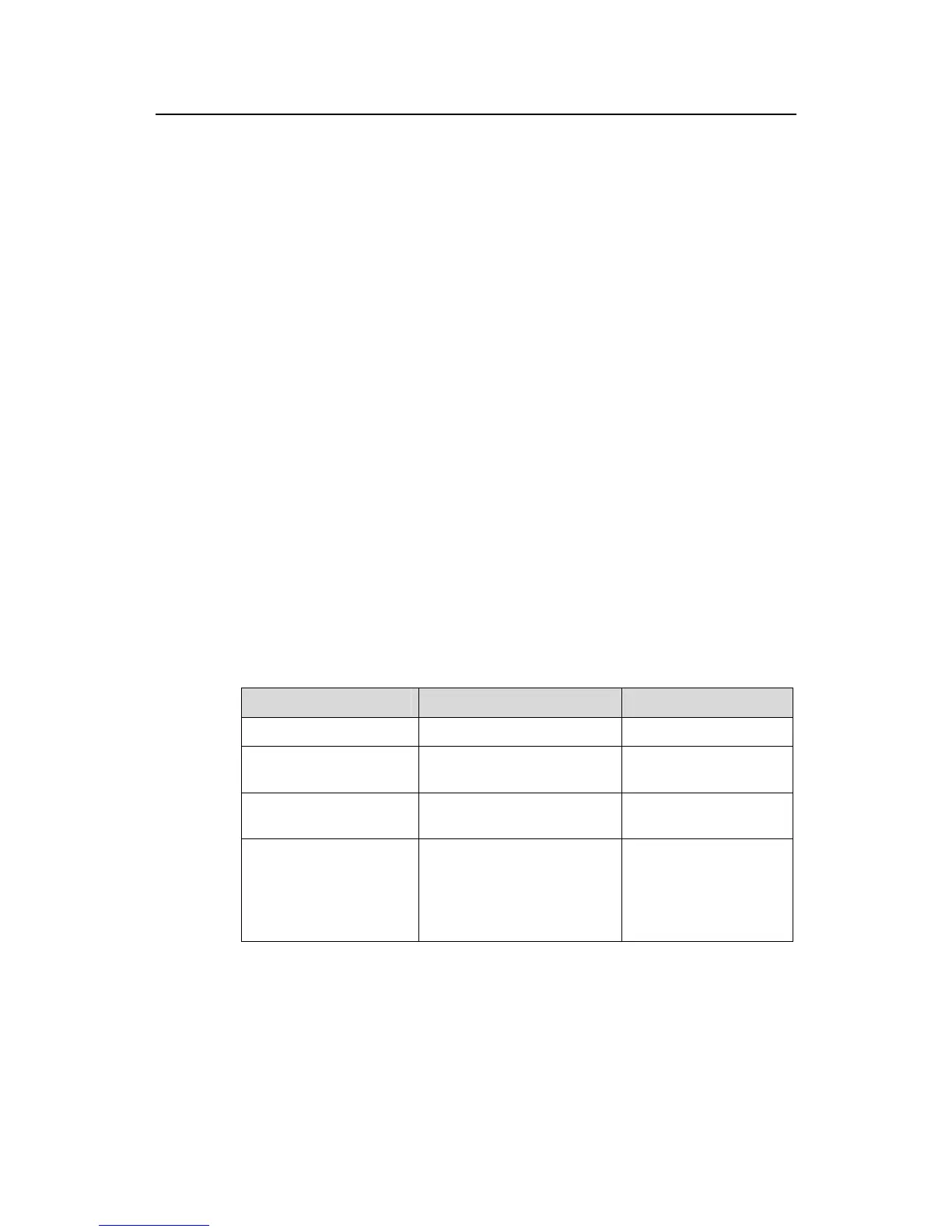
Table 2-1 EAD configuration
Operation Command Description
Enter system view
system-view
—
Enter RADIUS scheme
view
radius scheme
radius-scheme-name
—
Configure the RADIUS
server type to huawei
server-type huawei
Required
Configure the IP address
for the security policy
server
security-policy-server
ip-address
Required
Each RADIUS scheme
can support up to 8 IP
addresses of security
policy servers.
2.4 EAD Configuration Example
I. Network requirements
In Figure 2-2:

 Loading...
Loading...








