_____________________________________________________________________________
LB9 User’s Guide 1364/1523
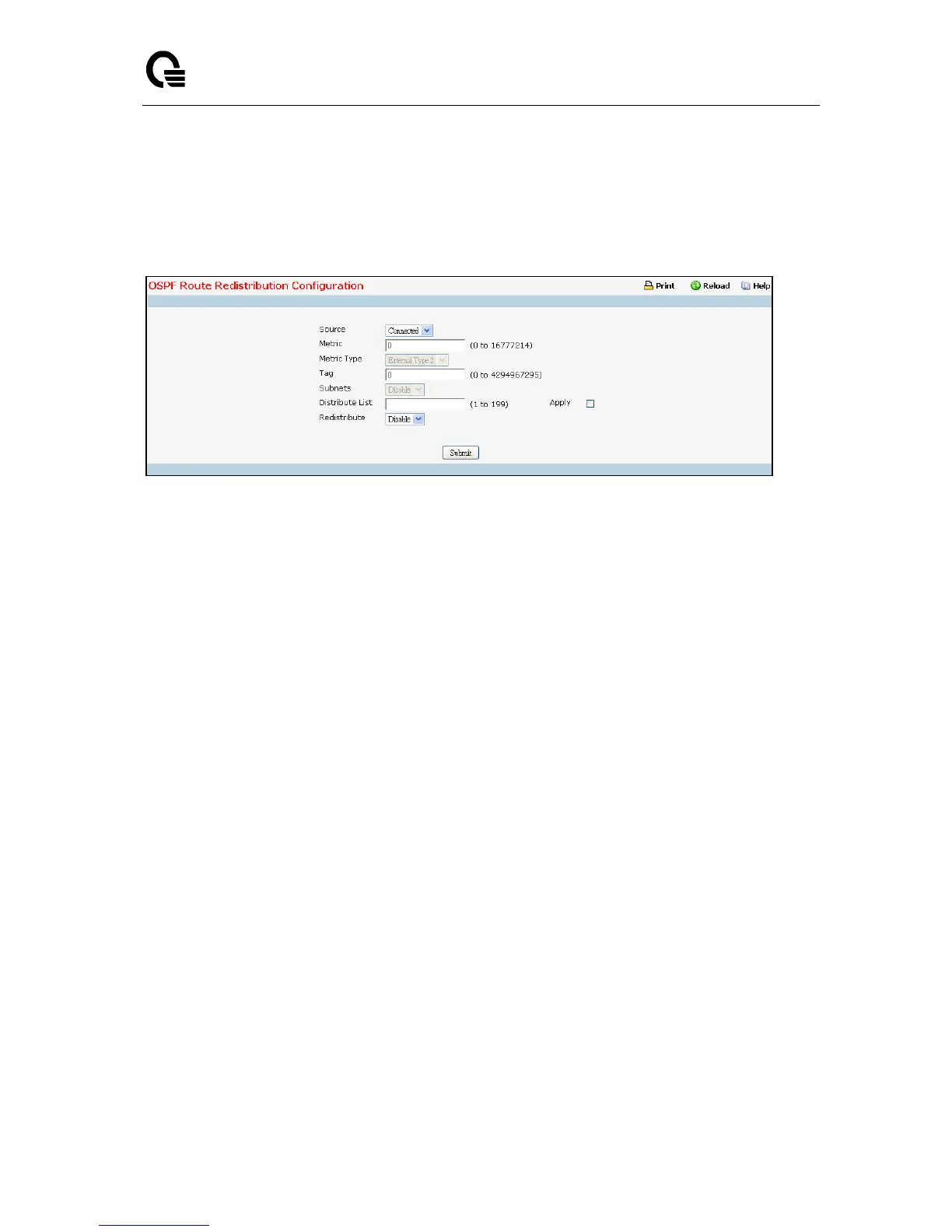
11.6.3.13 Configuring OSPF Route Redistribution
This screen can be used to configure the OSPF Route Redistribution parameters. The allowable values
for each fields are displayed next to the field. If any invalid values are entered, an alert message will be
displayed with the list of all the valid values.
Configurable Data
Source - This select box is a dynamic selector and would be populated by only those Source Routes
that have already been configured for redistribute by OSPF. However, the topmost option in the
select box would be "Create", and this allows the user to configure another, among the Available
Source Routes. The valid values are 'Static', 'Connected', 'RIP' and 'Create'.
Metric- Sets the metric value to be used as the metric of redistributed routes. This field displays the
metric if the source was pre-configured and can be modified. The valid values are (0 to 16777215)
Metric Type - Sets the OSPF metric type of redistributed routes.
Tag - Sets the tag field in routes redistributed. This field displays the tag if the source was
pre-configured, otherwise 0 and can be modified. The valid values are 0 to 4294967295. Default
value is 0.
Subnets - Sets whether the subnetted routes should be redistributed or not. Default value is Disable.
Distribute List - Sets the Access List that filters the routes to be redistributed by the destination
protocol. Only permitted routes are redistributed. If this command refers to a non-existent access list,
all routes are permitted. The valid values for Access List IDs are (1 to 199). When used for route
filtering, the only fields in an access list that get used are
Source IP Address and netmask
Destination IP Address and netmask
Action (permit or deny)
All other fields (source and destination port, precedence, tos, etc.) are ignored.
The source IP address is compared to the destination IP address of the route. The source IP
netmask in the access list rule is treated as a wildcard mask, indicating which bits in the source IP
address must match the destination address of the route. (Note that a 1 in the mask indicates a
"don’t care" in the corresponding address bit.)
When an access list rule includes a destination IP address and netmask (an extended access list),
the destination IP address is compared to the network mask of the destination of the route. The
destination netmask in the access list serves as a wildcard mask, indicating which bits in the route’s
destination mask are significant for the filtering operation.
 Loading...
Loading...