C
HAPTER
14
| Security Measures
Access Control Lists
– 311 –
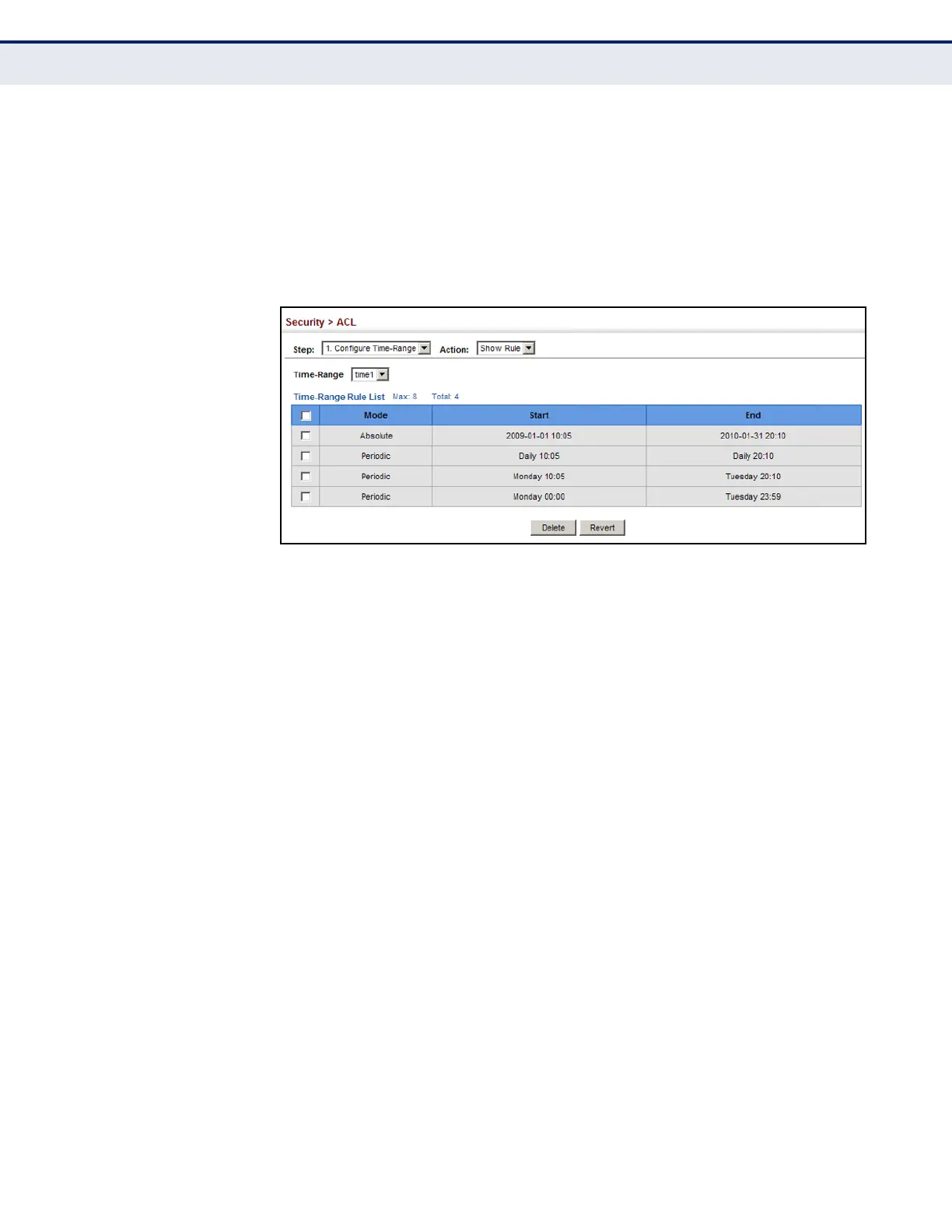
To show the rules configured for a time range:
1. Click Security, ACL.
2. Select Configure Time Range from the Step list.
3. Select Show Rule from the Action list.
Figure 172: Showing the Rules Configured for a Time Range
SHOWING TCAM
UTILIZATION
Use the Security > ACL (Configure ACL - Show TCAM) page to show
utilization parameters for TCAM (Ternary Content Addressable Memory),
including the number policy control entries in use, the number of free
entries, and the overall percentage of TCAM in use.
CLI REFERENCES
◆ "show access-list tcam-utilization" on page 518
COMMAND USAGE
Policy control entries (PCEs) are used by various system functions which
rely on rule-based searches, including Access Control Lists (ACLs), IP
Source Guard filter rules, Quality of Service (QoS) processes, or traps.
For example, when binding an ACL to a port, each rule in an ACL will use
two PCEs; and when setting an IP Source Guard filter rule for a port, the
system will also use two PCEs.
PARAMETERS
These parameters are displayed:
◆ Total Policy Control Entries – The number policy control entries in
use.
◆ Free Policy Control Entries – The number of policy control entries
available for use.
◆ Entries Used by System – The number of policy control entries used
by the operating system.

 Loading...
Loading...











