166
Table 96 Configuration items
Item Description
Application Name Specify the name for the custom application.
Protocol
Specify the protocol to be used for transferring packets, including
TCP
,
UDP
, and
All
.
All
means all IP carried protocols.
IP Address Specify the IP address of the server of the applications to be controlled.
Port
Match Rule
Specify the port numbers of the applications to be controlled.
When you select TCP or UDP for the
Protocol
parameter, the port configuration is
available:
• If you do not want to limit port numbers, do not select any option for the match
rule. In this case, you do not need to enter the start port and end port.
• If you want to limit a range of ports, select Range for the match rule, and then
enter the start port and end port to specify the port range.
• If you select other options of the match rule, you just need to enter the start
port.
Start Port
End Port
Enabling application control
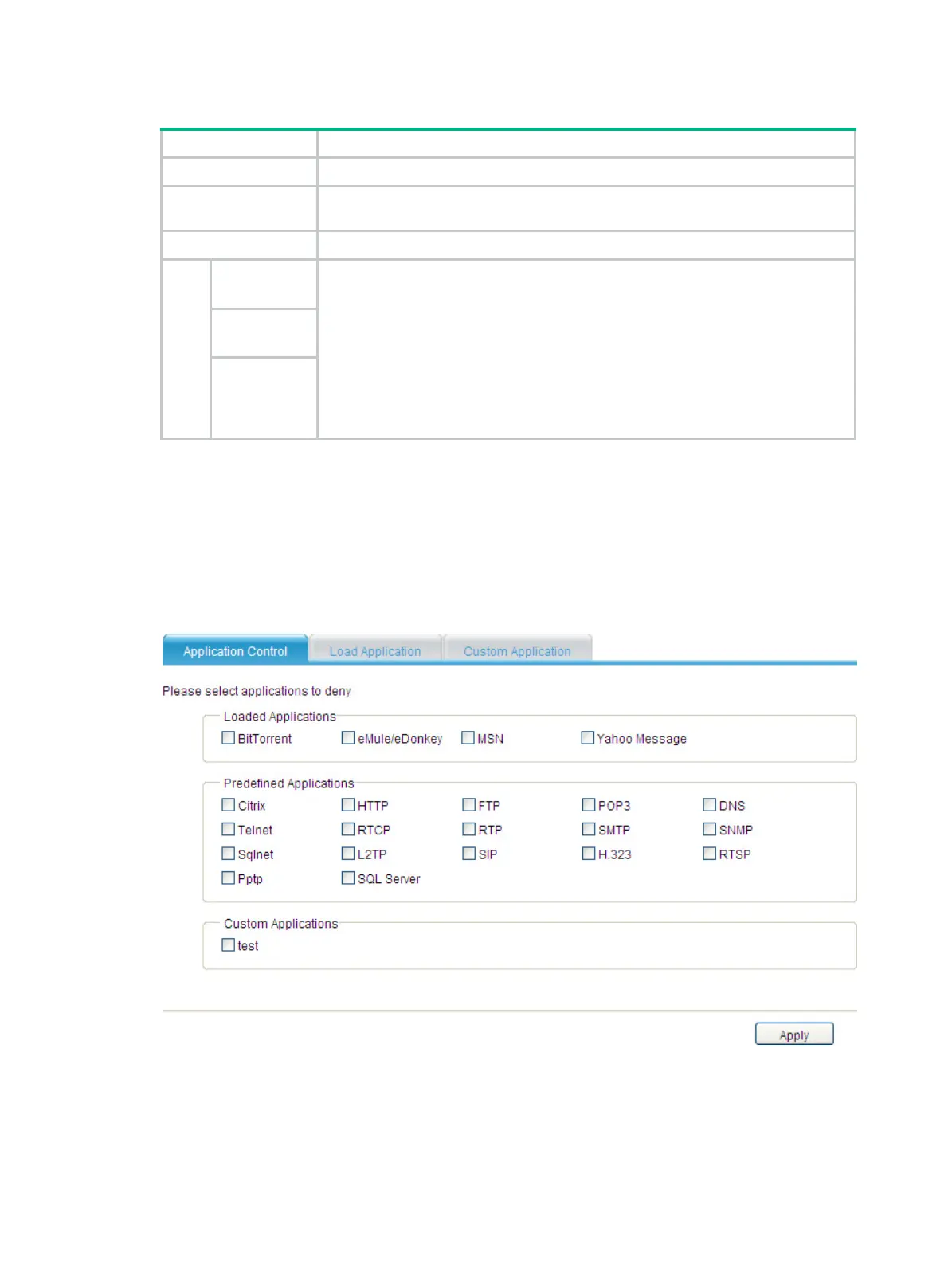
Select Security Setup > Application Control from the navigation tree and the page of the
Application Control tab is displayed by default, as shown in Figure 178. Select the applications and
proto
cols to be controlled from the Loaded Applications, Predefined Applications, and Custom
Applications areas as needed, and then click Apply.
Figure 178 Application Control

 Loading...
Loading...




