160
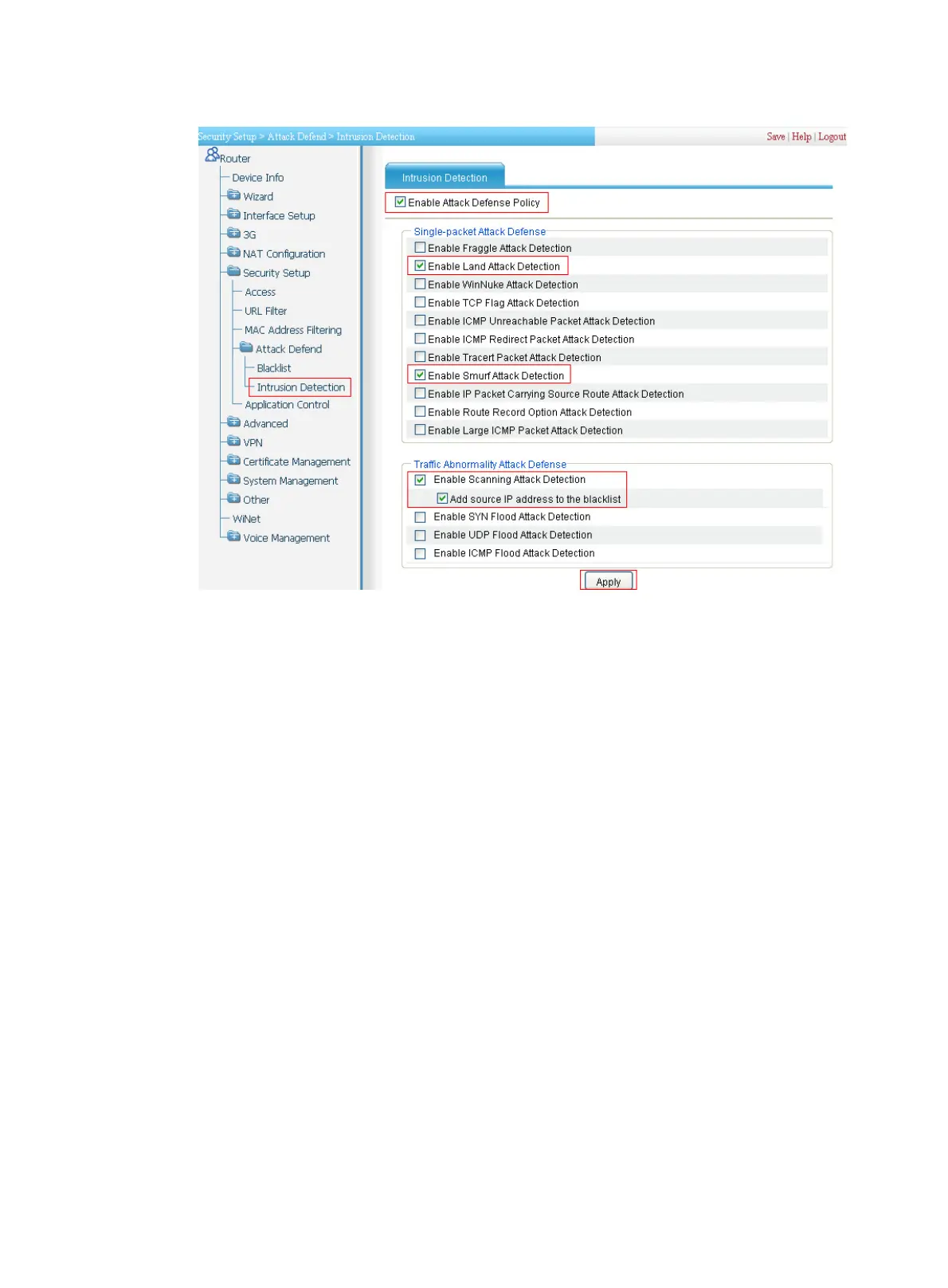
Figure 169 Configuring intrusion detection
• Select Enable Attack Defense Policy.
• Select Enable Land Attack Detection, Enable Smurf Attack Detection, Enable Scanning
Attack Detection, and Add Source IP Address to the Blacklist. Clear all other options.
• Click Apply.
Verifying the configuration
• Select Security Setup > Attack Defend > Blacklist. Host D and Host C are in the blacklist.
• Router drops all packets from Host D unless you remove Host D from the blacklist.
• Router drops packets from Host C within 50 minutes. Then, Router forwards packets from Host
C correctly.
• Upon detecting the scanning attack, Router outputs an alarm log and adds the IP address of the
attacker to the blacklist. You can view the added blacklist entry by selecting Security Setup >
Attack Defend > Blacklist.
• Upon detecting the Land or Smurf attack, Router outputs an alarm log and drops the attack
packet.
For MSR20/30/36/50/930 routers
Network requirements
As shown in Figure 170, internal users Host A, Host B, and Host C access the Internet through Router.
The network security requirements are as follows:
• Router always drops packets from Host D, an attacker.
• Router denies packets from Host C for 50 minutes for temporary access control of Host C.
• Router provides scanning attack protection and automatically adds detected attackers to the
blacklist on interface Ethernet 0/2, the interface connecting the Internet.
 Loading...
Loading...




