Introduction Introduction
Software Reference for SwitchBlade x3100 Series Switches (Access and Security)
6-136
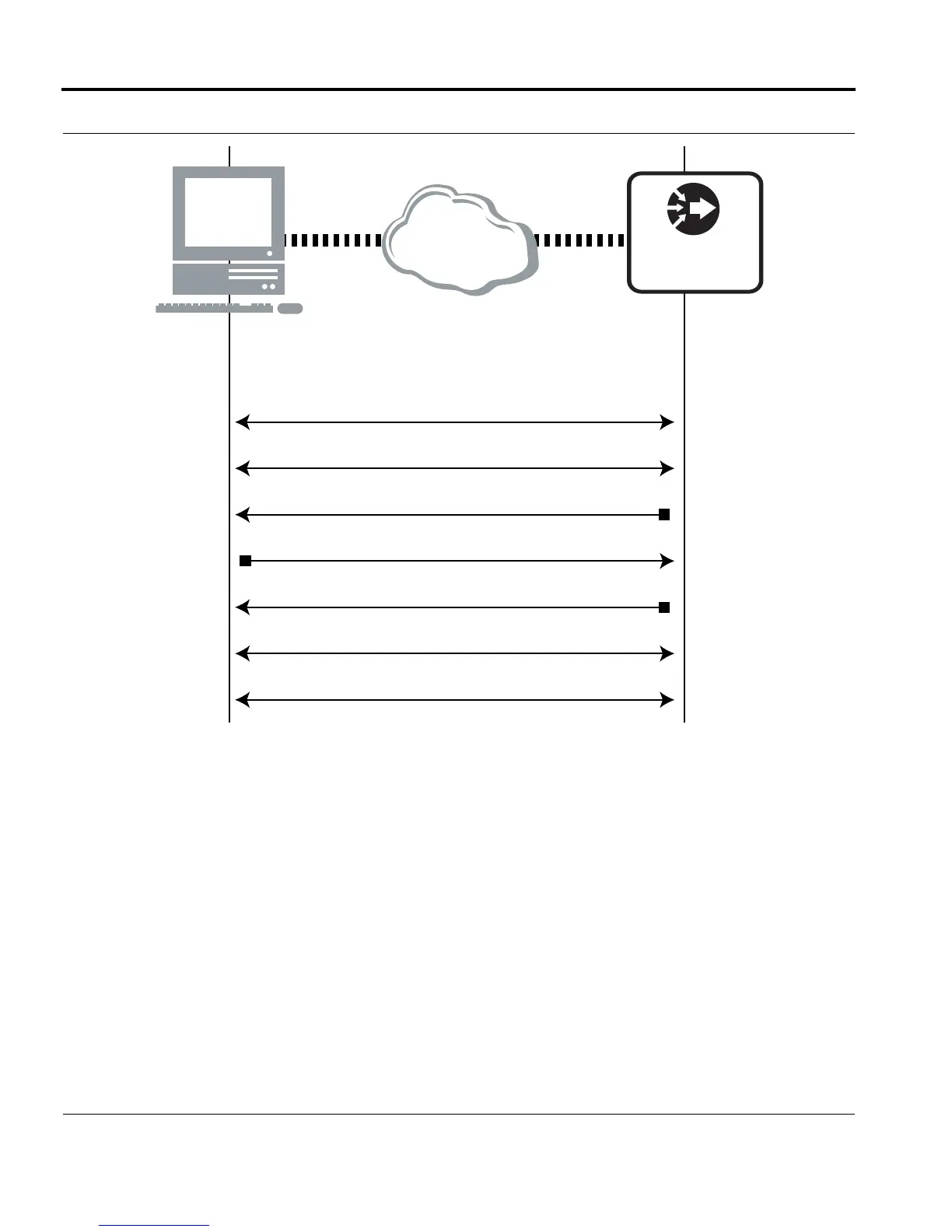
FIGURE 6-4 Typical Secure Shell Connection
Public key cryptography and digital signatures provide authentication and confidentiality in SSH, while checksum
values ensure data integrity. User authentication can be achieved through the use of a public key and/or a pass-
word.
Several texts exist that describe SSH in detail, such as the “SSH, The Secure Shell: The Definitive Guide” by
O’Reilly. For more information on SSH, refer to these texts.
The SBx3112 does not support the following SSH features:
• Remote, non interactive command execution
• Compression of SSH traffic
• File transfer over SSH
SSH Host
SSH Client
encrypted encrypted
Authentication Process
Connect
Algorithm negotiation
Host public key exchange
Service request
Service response
User authentication
Session established
SSH_Components
SBx3100

 Loading...
Loading...











