RM0440 Rev 4 1499/2126
RM0440 AES hardware accelerator (AES)
1538
34.4.5 AES decryption round key preparation
Internal key schedule is used to generate AES round keys. In AES encryption, the round 0
key is the one stored in the key registers. AES decryption must start using the last round
key. As the encryption key is stored in memory, a special key scheduling must be performed
to obtain the decryption key. This key scheduling is only required for AES decryption in ECB
and CBC modes.
Recommended method is to select the Mode 2 by setting to 01 the MODE[1:0] bitfield of the
AES_CR (key process only), then proceed with the decryption by setting MODE[1:0] to 10
(Mode 3, decryption only). Mode 2 usage is described below:
1. Disable the AES peripheral by clearing the EN bit of the AES_CR register.
2. Select Mode 2 by setting to 01 the MODE[1:0] bitfield of the AES_CR. The
CHMOD[2:0] bitfield is not significant in this case because this key derivation mode is
independent of the chaining algorithm selected.
3. Set key length to 128 or 256 bits, via KEYSIZE bit of AES_CR register.
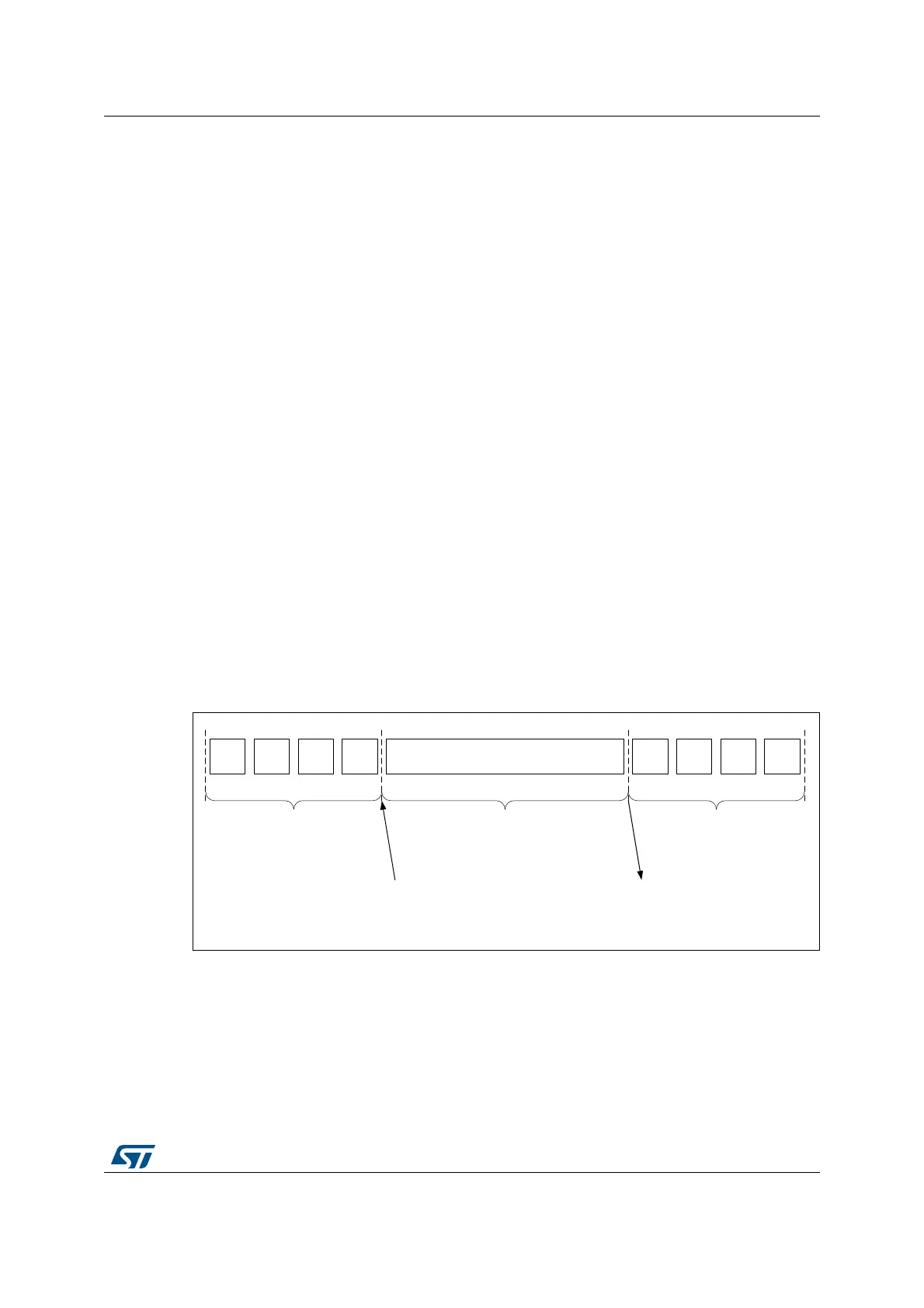
4. Write the AES_KEYRx registers (128 or 256 bits) with encryption key, as shown in
Figure 508. Writes to the AES_IVRx registers have no effect.
5. Enable the AES peripheral, by setting the EN bit of the AES_CR register.
6. Wait until the CCF flag is set in the AES_SR register.
7. Clear the CCF flag. Derived key is available in AES core, ready to use for decryption.
Application can also read the AES_KEYRx register to obtain the derived key if needed,
as shown in Figure 508 (the processed key is loaded automatically into the
AES_KEYRx registers).
Note: The AES is disabled by hardware when the derivation key is available.
To restart a derivation key computation, repeat steps 4, 5, 6, and 7.
Figure 508. Encryption key derivation for ECB/CBC decryption (Mode 2)
If the software stores the initial key prepared for decryption, it is enough to do the key
schedule operation only once for all the data to be decrypted with a given cipher key.
Note: The operation of the key preparation lasts 59 or 82 clock cycles, depending on the key size
(128- or 256-bit).
MS18937V2
WR
EK3
WR
EK2
WR
EK1
WR
EK0
Wait until flag CCF = 1
RD
DK3
RD
DK2
RD
DK1
RD
DK0
Input phase
4 write operations into
AES_KEYRx[31:0]
Computation phase
Output phase (optional)
4 read operations of
AES_KEYRx[31:0]
EK = encryption key = 4 words (EK3, … , EK0)
DK = decryption key = 4 words (DK3, … , DK0)
MSB LSB MSB LSB
EN = 1 into AES_CR
128-bit derivation key
stored into AES_KEYRx

 Loading...
Loading...