SCTP Security
The 5ESS
®
switch uses SCTP layer security according to the SCTP
standards. SCTP provides for protection against:
• flooding,
• blind masquerade,
• improper monopolization of services, and
• fraud and repudiation.
SCTP uses a cookie mechanism which is started during initialization
to provide protection against security attacks. This is an advantage
over TCP and UDP because they do not have this application
function.
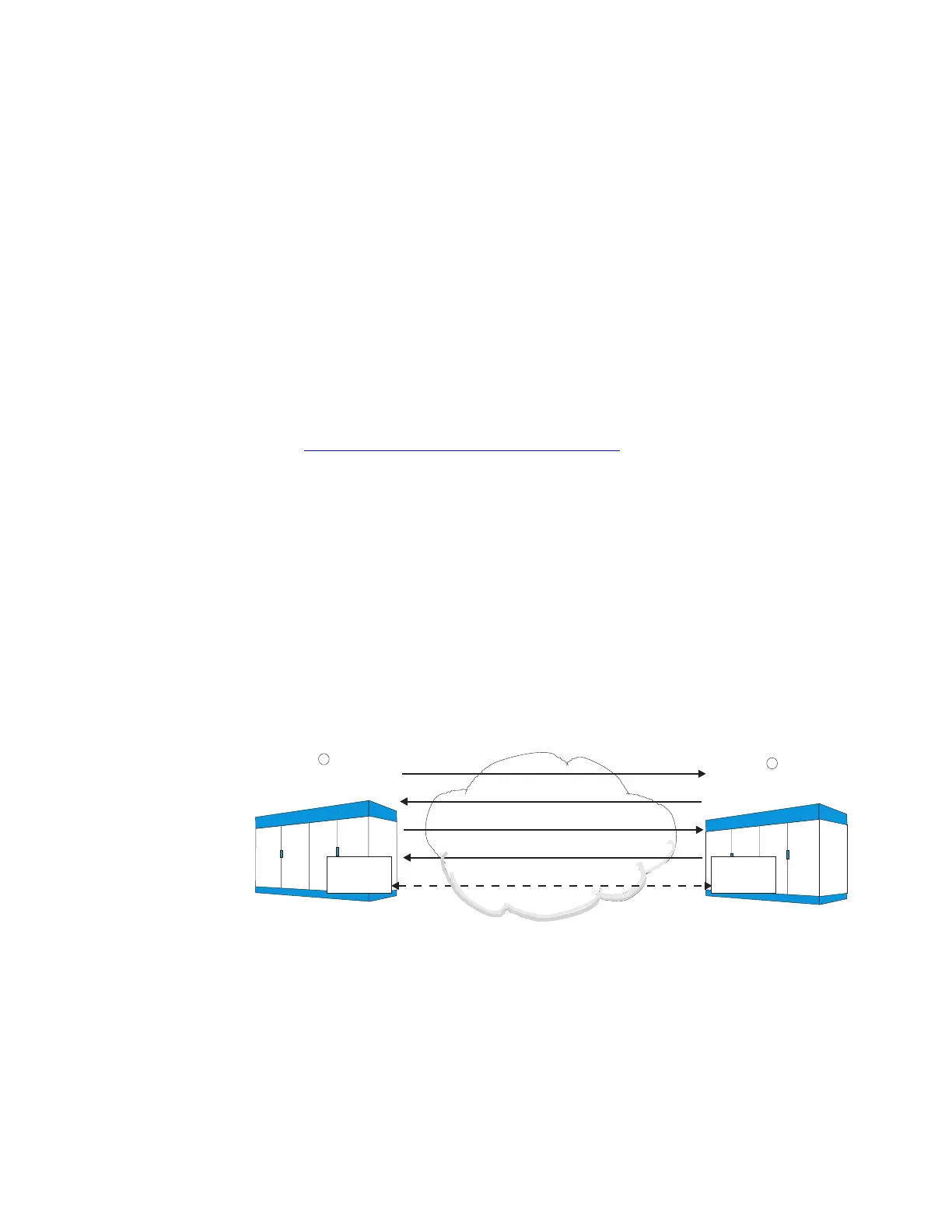
Cookie Mechanism
Figure 2-18, “Cookie Mechanism” (2-36) illustrates the cookie
mechanism.
1. The client, office A, sends a connection request (INIT) to the
server.
2. The server, office B, builds a cookie (INIT ACK) containing
TCB information and sends it to the client.
3. The client returns the TCB information to the server (COOKIE
ECHO).
4. The server validates the cookie and uses it to rebuild the TCB
that it returns to the client (COOKIE ACK).
The advantage of the cookie mechanism is that the server does not
reserve memory or resources until a COOKIE ECHO message is
received from the client. This protects the server from overload during
blind attacks.
Figure 2-18 Cookie Mechanism
5ESS Switch
R
5ESS Switch
R
Office A
Office B
IP Network
Association
Transmission
Control Block (TCB)
Created
Transmission
Control Block (TCB)
Created
INIT
INIT ACK
COOKIE ECHO
COOKIE ACK
SCTP
Endpoint
SCTP
Endpoint
Security View
Architecture
....................................................................................................................................................................................................................................
2-36
Lucent Technologies 235-200-118
Issue 3.02B, March 2007
 Loading...
Loading...