Port Monitoring | 793
Flow-based Monitoring
Flow-based Monitoring is supported only on platform e
Flow-based monitoring conserves bandwidth by monitoring only specified traffic instead all traffic on the
interface. This feature is particularly useful when looking for malicious traffic. It is available for Layer 2
and Layer 3 ingress and egress traffic. You may specify traffic using standard or extended access-lists.
To configure flow-based monitoring:
View an access-list that you applied to an interface using the command
show ip accounting access-list from
EXEC Privilege mode, as shown in Figure 36-8.
Step Task Command Syntax Command Mode
4 Enable flow-based monitoring for a monitoring session.
flow-based enable
MONITOR SESSION
5 Define in an access-list rules that include the keyword
monitor. FTOS only considers for port monitoring traffic
matching rules with the keyword monitor.
See Chapter 7, Access Control Lists (ACLs).
ip access-list
CONFIGURATION
6 Apply the ACL to the monitored port. See Chapter 7,
Access Control Lists (ACLs).
ip access-group
access-list
INTERFACE
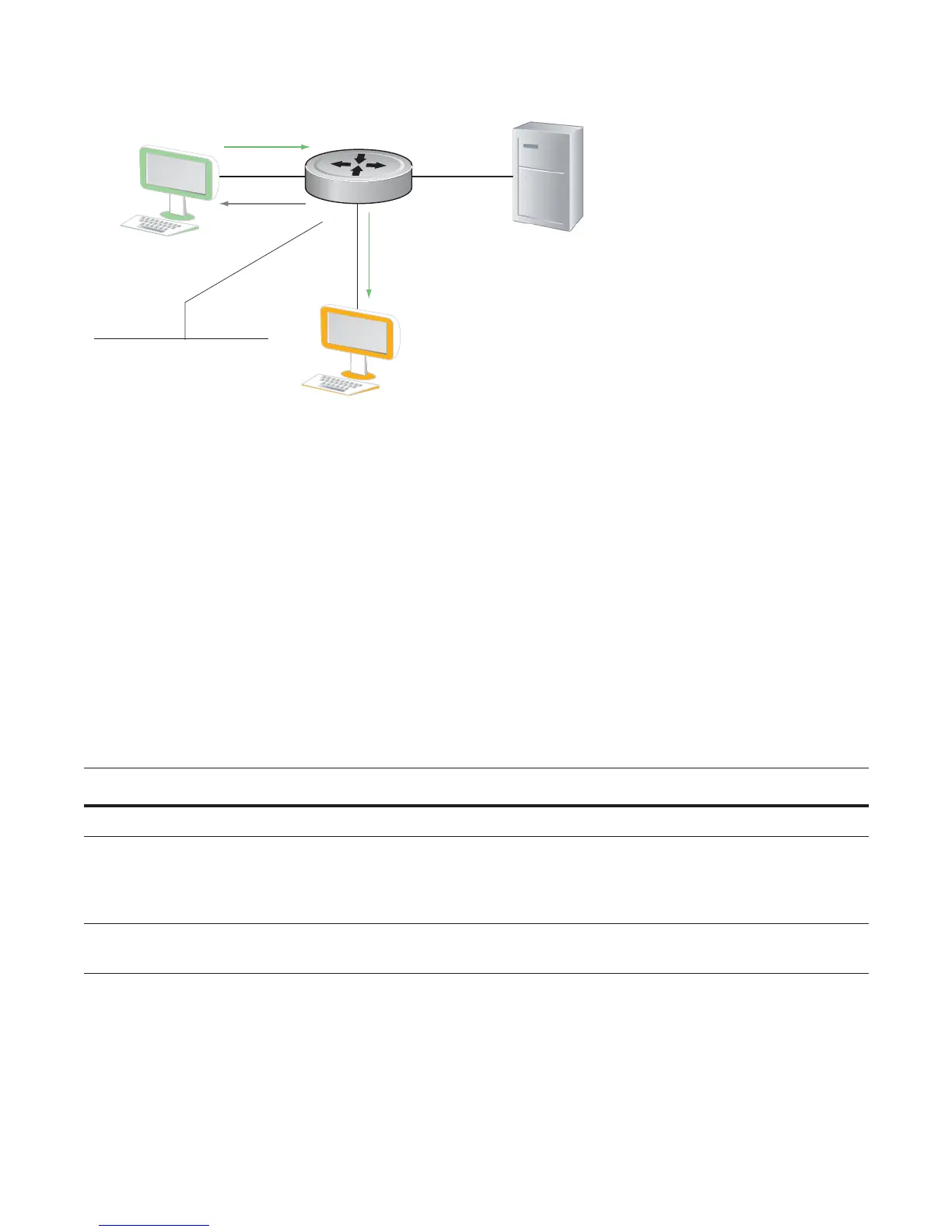
1/2
1/1
Host
Sniffer
Server
1/3
TOS(conf-if-gi-1/2)#show config
nterface GigabitEthernet 1/2
no ip address
no shutdown
TOS(conf)#monitor session 0
TOS(conf-mon-sess-0)#source gig 1/1 destination gig 1/2 direction rx
Server Traffic
Host Traffic
Port Monitoring 001

 Loading...
Loading...











