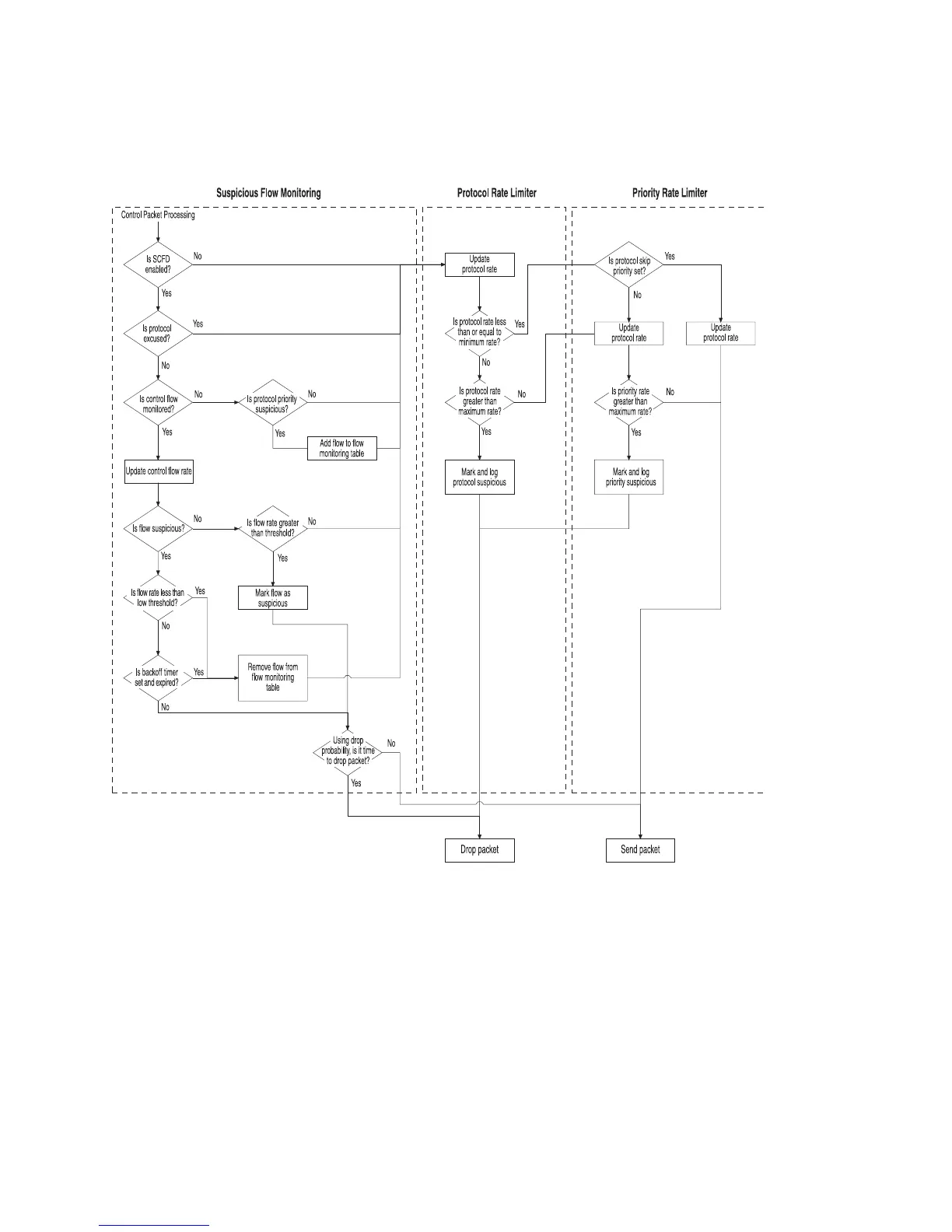
Figure 26: Typical Control Packet Processing
Suspicious Control Flow Detection
To reduce the chance of a successful denial of service (DoS) attack and to provide
diagnostic abilities while undergoing an attack, the system can detect suspicious
control flows and keep state on those flows. A flow is a specific control protocol on
a specific interface from a particular source. When the system determines that a
control flow is suspicious, it can take corrective action on that control flow.
Keeping full state on each control flow can use a large number of resources. Instead,
the system detects which flows have suspicious traffic. If a control flow is marked
as suspicious, every packet associated with the flow is considered suspicious. When
Denial of Service (DoS) Protection ■ 451
Chapter 7: Passwords and Security

 Loading...
Loading...