Performance Impact of Encryption
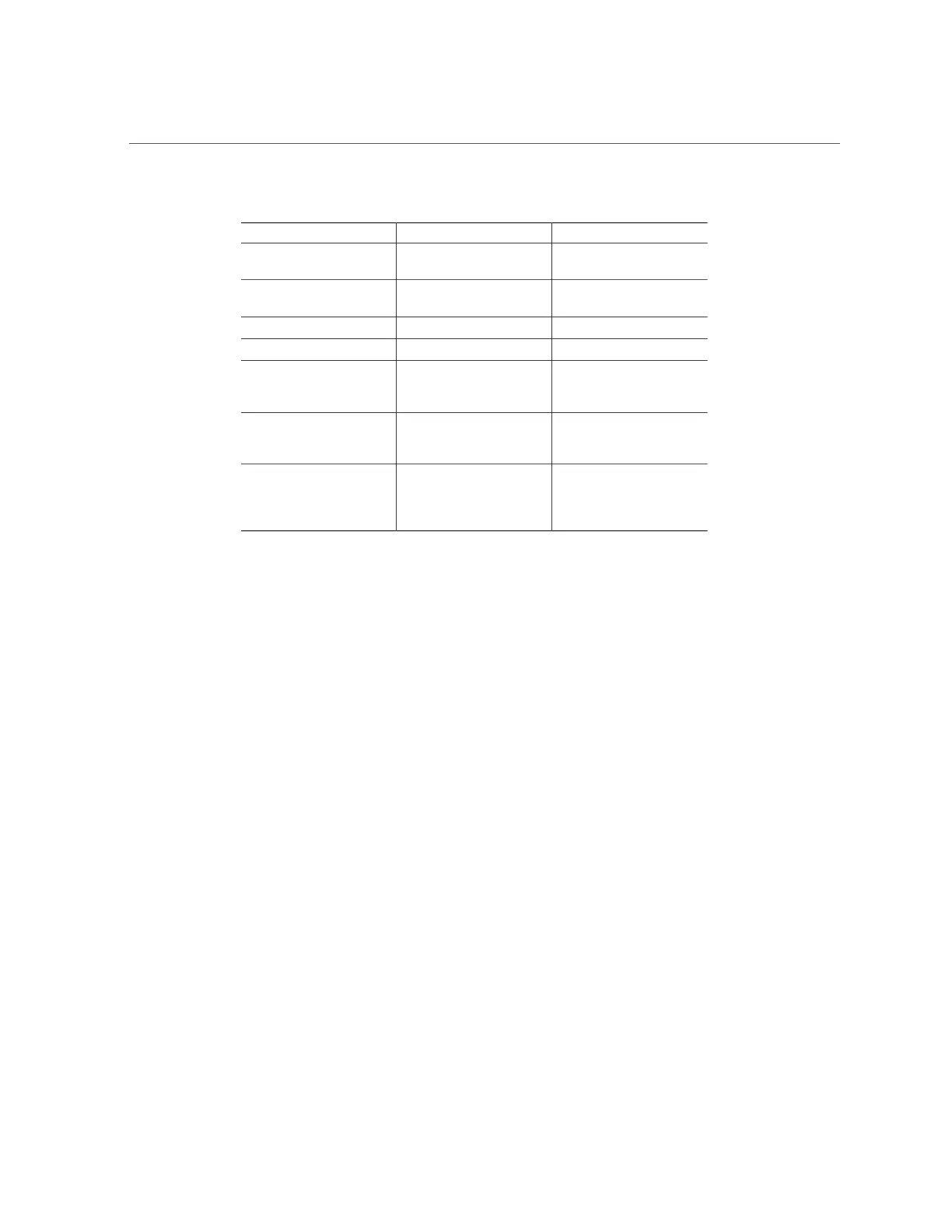
TABLE 124
Encryption Key Values
BUI Value CLI Value Description
Off off Share/Project is not
encrypted
AES-128-CCM aes-128-ccm Lowest CPU impact
encryption. Dedupable
AES-192-CCM aes-192-ccm Dedupable
AES-256-CCM aes-256-ccm Dedupable
AES-128-GCM aes-128-gcm NIST SP800-38D
recommended, Not-
Dedupable
AES-192-GCM aes-192-gcm NIST SP800-38D
recommended, Not-
Dedupable
AES-256-GCM aes-256-gcm Highest CPU impact
encryption, NIST SP800-
38D recommended, Not-
Dedupable
Performance Impact of Encryption
Using encryption with shares can have CPU performance impacts, as follows:
■
The AES-128-CCM mode has the lowest CPU performance impact and is recommended for
all workloads where there are no LOCAL security requirements.
■
When encrypted data is read, it is stored decrypted and decompressed in DRAM. For read-
dominate workloads that can be serviced read-dominant from the DRAM cache, the impact
of decrypting the data is minimal.
■
When SSD cache devices are used, data blocks evicted out of DRAM to the cache are
compressed and encrypted and must be decrypted and decompressed when retrieved back
into DRAM.
■
For workloads that are write-dominant and use larger block sizes, especially 128 kilobytes
and 1 megabyte, there can be a significant CPU impact resulting in lower throughput. This
is particularly likely if the filesystem record size or LUN volume block size is larger than
the application block size.
Related Topics
■
“Data Encryption Workflow” on page 560
■
“Encryption Properties” on page 581
■
“Managing Encryption Keys” on page 582
584 Oracle ZFS Storage Appliance Administration Guide, Release OS8.6.x • September 2016

 Loading...
Loading...








