Chapter 12
| Security Measures
Access Control Lists
– 324 –
For example, when binding an ACL to a port, each rule in an ACL will use two PCEs;
and when setting an IP Source Guard filter rule for a port, the system will also use
two PCEs.
Parameters
These parameters are displayed:
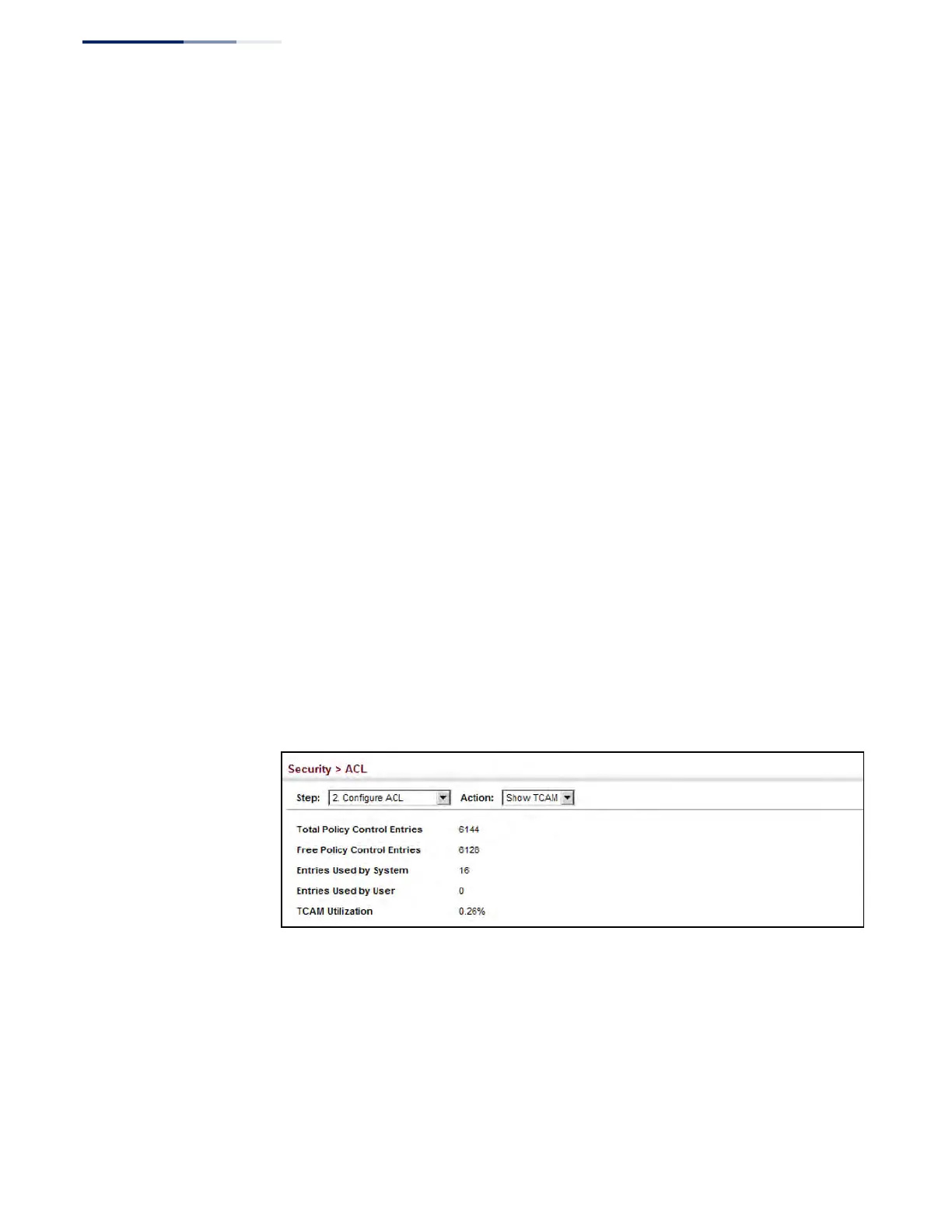
◆ Total Policy Control Entries – The number policy control entries in use.
◆ Free Policy Control Entries – The number of policy control entries available for
use.
◆ Entries Used by System – The number of policy control entries used by the
operating system.
◆ Entries Used by User – The number of policy control entries used by
configuration settings, such as access control lists.
◆ TCAM Utilization – The overall percentage of TCAM in use.
Web Interface
To show information on TCAM utilization:
1. Click Security, ACL.
2. Select Configure ACL from the Step list.
3. Select Show TCAM from the Action list.
Figure 197: Showing TCAM Utilization
Setting the
ACL Name and Type
Use the Security > ACL (Configure ACL - Add) page to create an ACL.
Parameters
These parameters are displayed:
◆ ACL Name – Name of the ACL. (Maximum length: 32 characters)

 Loading...
Loading...











