Working with VSCs
VSC configuration options
5-6
About access control and authentication
The availability of certain VSC features and their functionality is controlled by the settings of
two important parameters in the Global box. These parameters determine how
authentication and access control are handled by the VSC:
Use Controller for: Authentication
Determines if user authentication services (802.1X, WPA, WPA2, MAC-based) are provided by
the controller. When enabled, APs forward user login requests to the controller. The
controller resolves these requests using the local user accounts, or Active Directory, or acts
as a RADIUS proxy for a third-party RADIUS server.
Use Controller for: Access control
This option can only be enabled if the Authentication option is enabled first. When enabled,
this option creates an access-controlled VSC. This means that access to protected network
resources via this VSC are restricted by the access control features on the controller. Access
control features include the public/guest network access interface and access lists.
The following diagrams provide an overview of how user authentication and data traffic are
handled depending on how these options are configured.
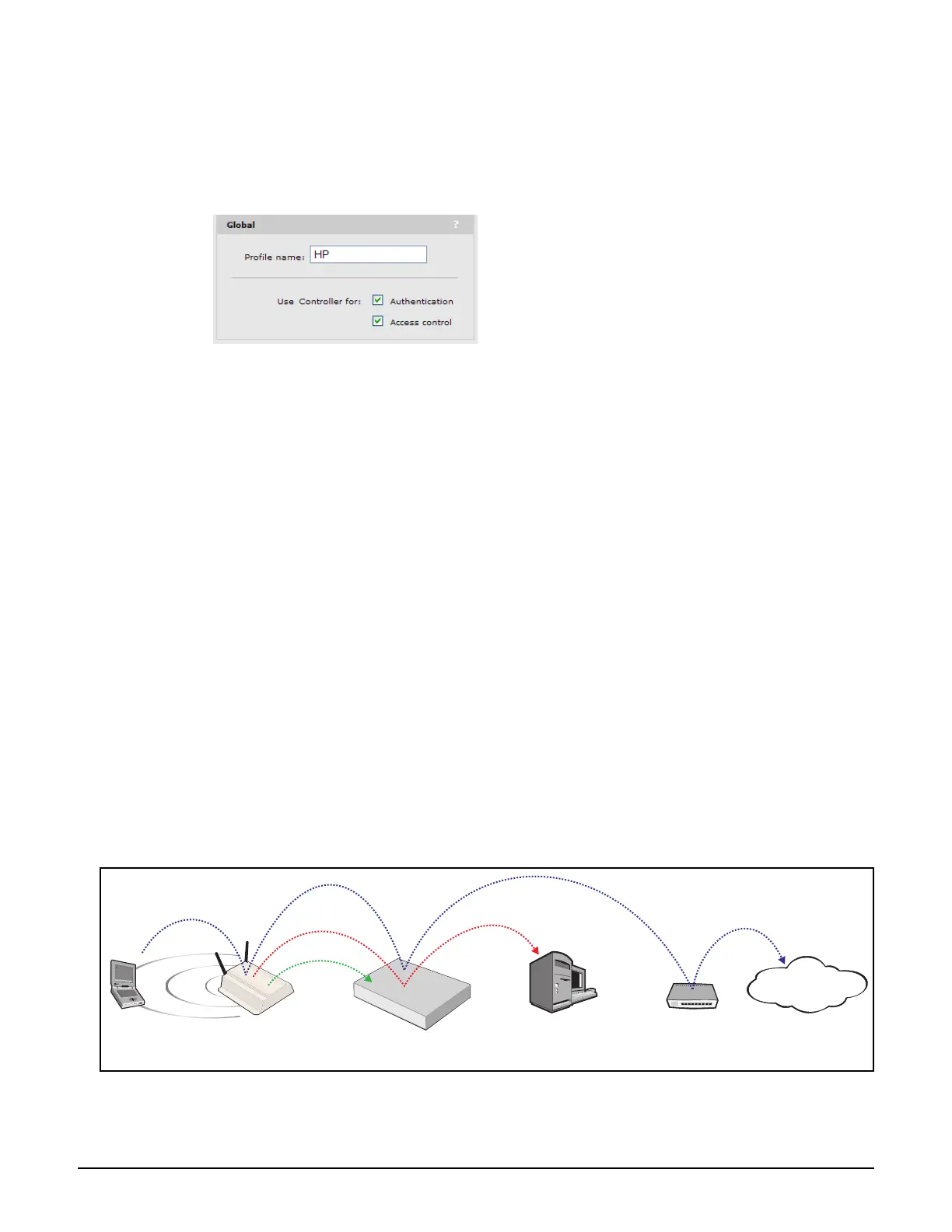
When both authentication and access control are enabled
In this configuration, the controlled AP forwards authentication requests from users on the
VSC to the controller. The controller resolves these requests using the local user list, or the
services of a third-party authentication server (Active Directory or RADIUS server). The
controller then manages access to the protected network using its access control features
(public access, interface, access lists, etc.).
ControllerControlled AP
User
Third-party
authentication
server
Protected network
A
u
t
h
e
n
t
i
c
a
t
i
o
n
t
r
a
f
f
i
c
U
s
e
r
t
r
a
f
f
i
c
Router
M
a
n
a
g
e
m
e
n
t
t
r
a
f
f
i
c

 Loading...
Loading...