Working with controlled APs
Key controlled-mode events
6-4
AP authentication
The controller can be configured to authenticate APs by their MAC address before they are
managed. The authentication can be defined locally on the controller, via a third-party
RADIUS server, or using a remote text-based control file.
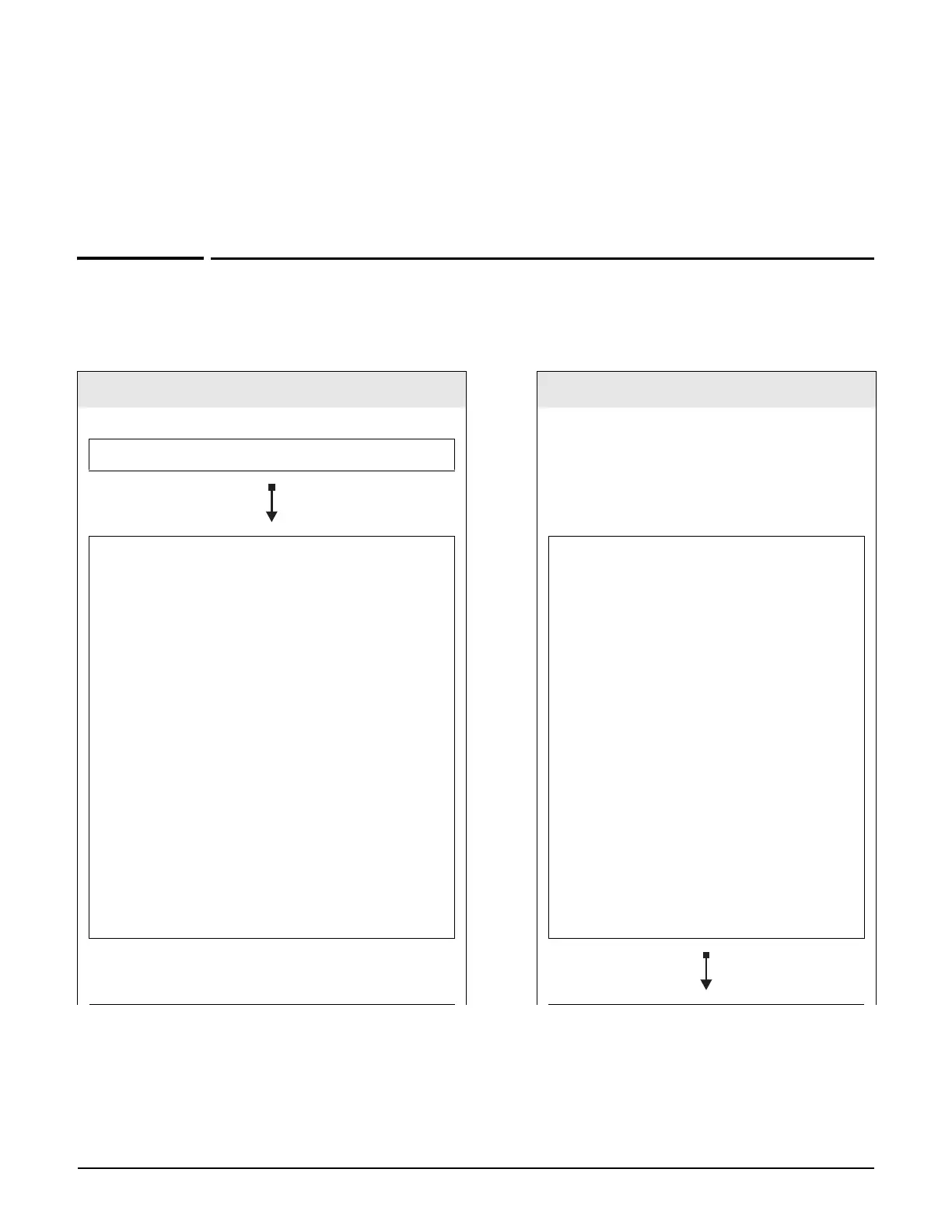
Key controlled-mode events
The following diagram provides an overview of key events that occur when working with APs
in controlled mode.
Controller AP
Deploy the controller.
Configure AP authentication. For security
purposes, the controller can require that APs be
authenticated before they can be managed.
See Authentication of controlled APs on
page 6-19.
Set up groups. Groups allow you to apply the
same configuration settings to many APs at the
same time. You can create multiple groups,
allowing you to maintain distinct settings for
different types of APs. If no groups are created,
all APs are assigned to a default group.
See Configuring APs on page 6-22.
Deploy an AP with its default
configuration OR manually provision
initial AP configuration.
On most network topologies, if you
deploy an AP with factory default settings
it will automatically find and connect
with a controller on the network.
In some cases, it may be necessary or
desirable to provision an AP before it is
deployed to ensure that discovery is
successful, or to force a specific
discovery option.
The AP does not offer wireless services
until it discovers and connects with a
controller.
See Provisioning APs on page 6-31.

 Loading...
Loading...