Working with VPNs
Additional IPSec configuration
16-11
Additional IPSec configuration
The page Controller >> VPN > IPSec provides some additional configuration options and
information. For information about IPsec certificates see IPSec certificates on page 12-11.
IPSec VLAN mapping
Use these settings to define how IPSec traffic is routed on the LAN and Internet ports. You
can assign traffic to the untagged interface (no VLAN) or to any defined VLAN.
Local group list
When using IPSec aggressive mode, groups can be used to authenticate IPSec connections
from clients (peers). The client must supply the group name matching one of the groups
defined here to establish a security association with the controller.
Create all needed groups, providing information as follows:
Group name: Group names are case-sensitive and should be in the format
user@FQDN.com or FQDN.com. For example, fred@mycompany.com or
server99.mycompany.com.
Password/Confirm password: Passwords must be at least six characters long and contain
at least four different characters.
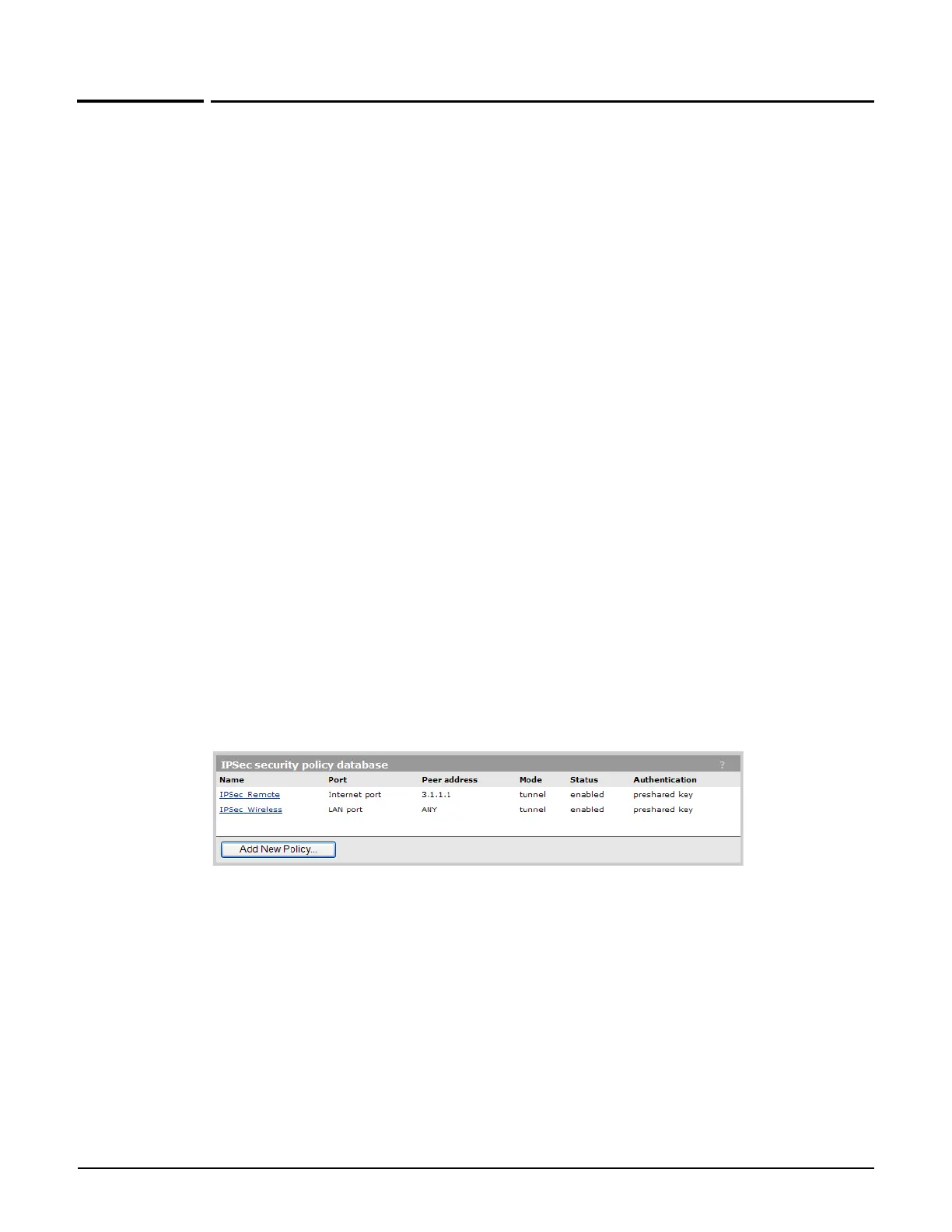
IPSec security policy database
The IPSec security policy database table shows all the IPSec security policies that are
defined on the controller. A security policy defines the criteria that must be met for a peer to
establish an IPSec security association (SA) with the controller.
This information is provided:
Name: Name assigned to the security policy.
Port: Port assigned to the security policy.
Peer address: Address of the peer which can establish an SA using this policy.
Mode: Indicates the IPSec mode (tunnel or transport) supported by this policy.
Status: Indicates whether the policy has been enabled. An SA can only be established
when a policy is enabled.
Authentication: Indicates the method used to authenticate peers.

 Loading...
Loading...